AWS PrivateLink: Cross-Region Connectivity
Coralogix now supports AWS PrivateLink for native cross-region connectivity, making it dramatically easier to securely send observability data from multiple AWS regions to your Coralogix PrivateLink endpoint. This new capability eliminates the need for complex workarounds and simplifies cross-region integrations. Whether you're scaling globally or distributing workloads across regions, this enhancement reduces setup time and removes the need to duplicate infrastructure.
Benefits of native cross-region PrivateLink over VPC peering
Previously, enabling PrivateLink across regions required complex manual setup: cross-region VPC peering, route table configuration, DNS management, and more.
Native support replaces that complexity with a simpler, built-in alternative:
- No VPC peering or AZ alignment required
- IAM-based access control
- Built-in high availability with automatic routing across healthy zones
- Lower operational overhead with fewer networking components to maintain
How Coralogix uses native cross-region PrivateLink
You can now connect Coralogix to workloads in different AWS regions using a single, simplified PrivateLink configuration.
Note
Cross-region connectivity only works when both regions are in the same AWS partition. For example, connecting us-east-1 and eu-west-1 is supported, but connections between aws-us-gov (AWS GovCloud) and aws-cn (AWS China) partitions are not.
Prerequisites
Before configuring a cross-region endpoint, make sure you've reviewed the available service endpoints.
The IAM user or role creating the endpoint must have the following permission: vpce:AllowMultiRegion.
Cross-Region endpoint configuration
STEP 1. Create an IAM permission policy
Create an IAM permission policy and attach it to the IAM user or service creating the endpoint. This is explicitly required even if you have all access configured.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowMultiRegionPrivateLink",
"Effect": "Allow",
"Action": [
"vpce:AllowMultiRegion"
],
"Resource": "*"
}
]
}
STEP 2. Create a cross-region VPC endpoint
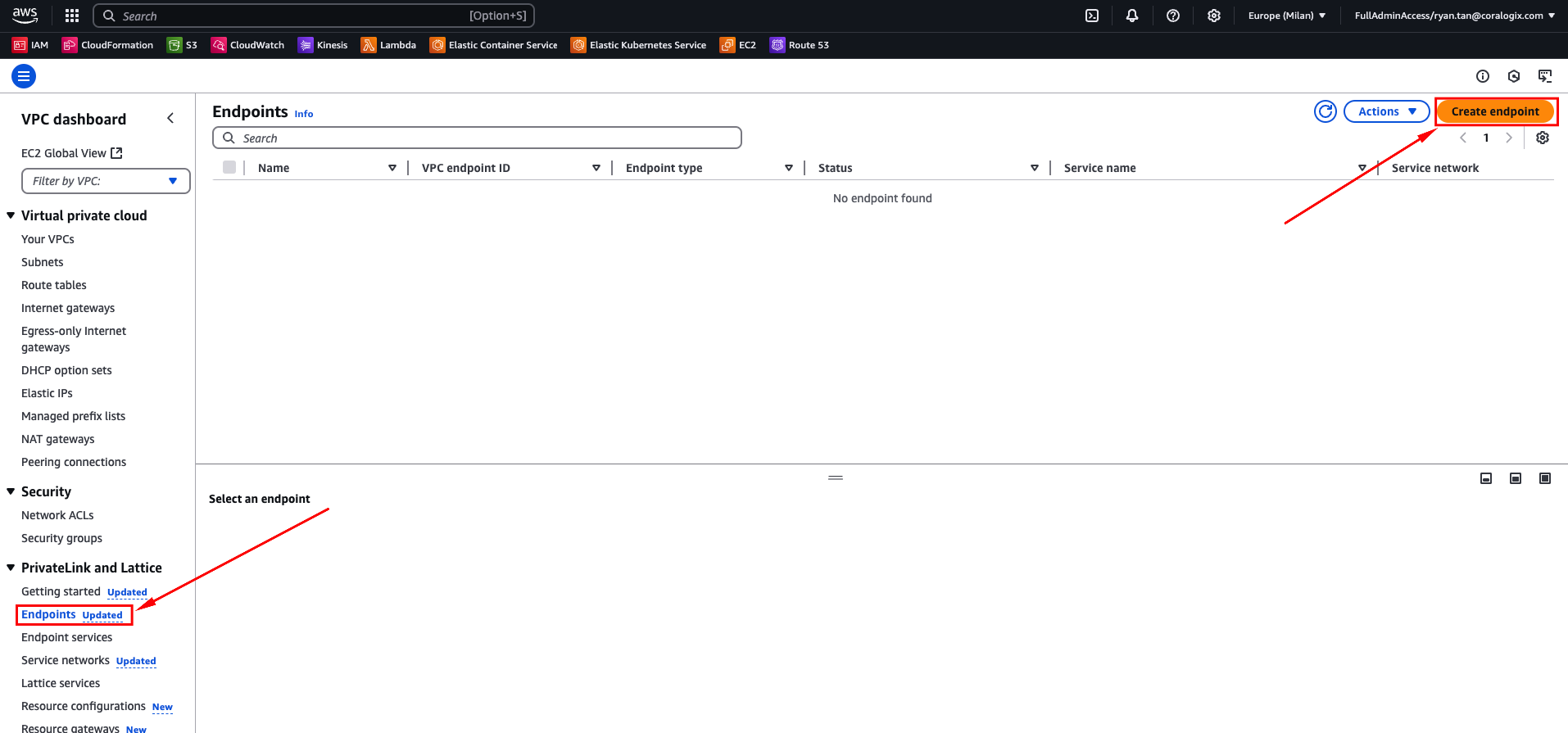
Navigate to the VPC console in your region.
Navigate to PrivateLink and "Lattice" > "Endpoints". Click "Create endpoint".
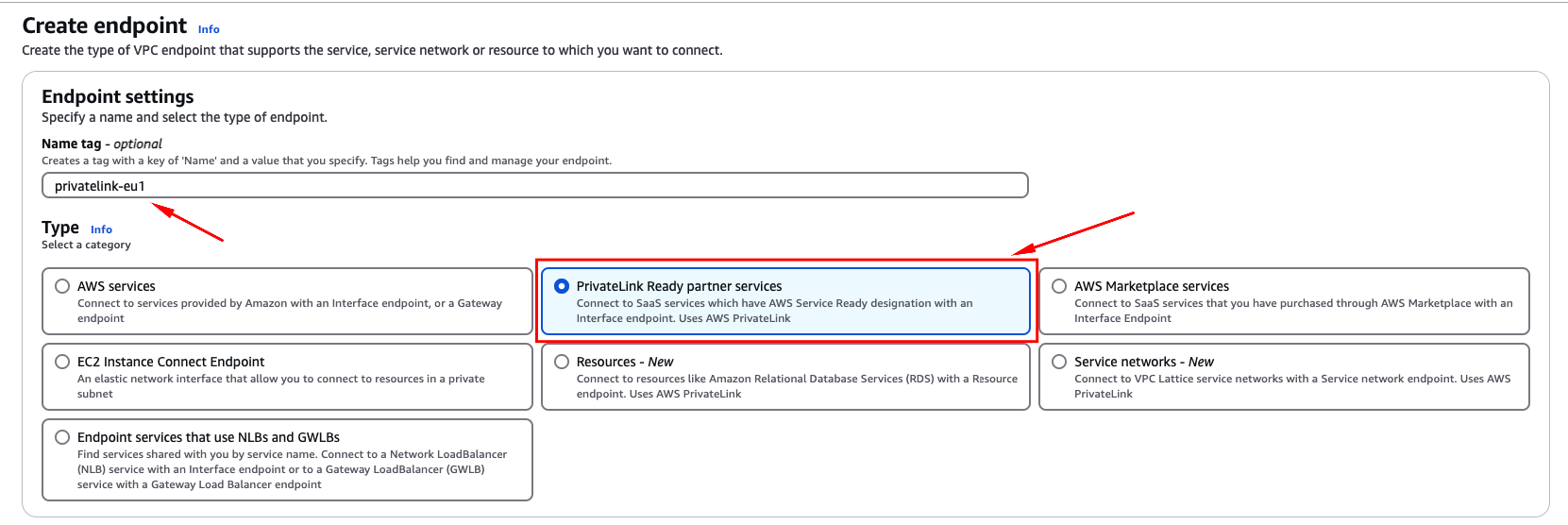
Enter the PrivateLink service name for the appropriate region.
Select "PrivateLink ready partner services" as the category.
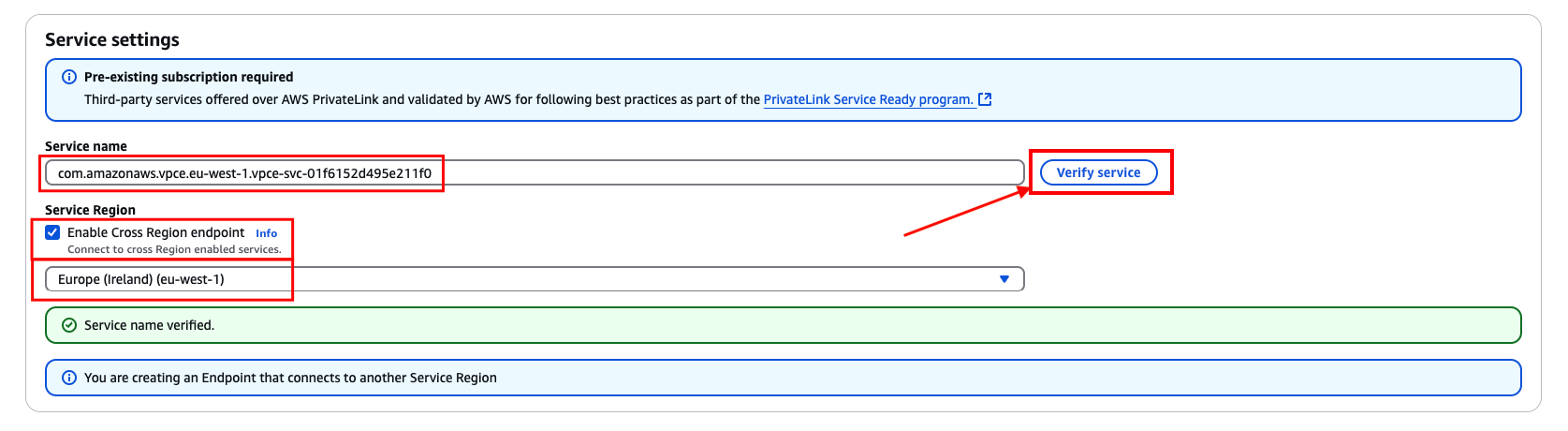
- In the Service settings section, copy the service name of the Coralogix PrivateLink address where your target region is hosted into the "Service Name" section. To find the correct Coralogix PrivateLink service name, select the PrivateLink endpoint associated with your Coralogix region and domain. The example below would be for the
coralogix.comdomain:
Under "Service Region", check the box "Enable cross-region endpoint".
Click "Verify service" to confirm that the service exists and is accessible.
STEP 3. Configure VPC and subnets
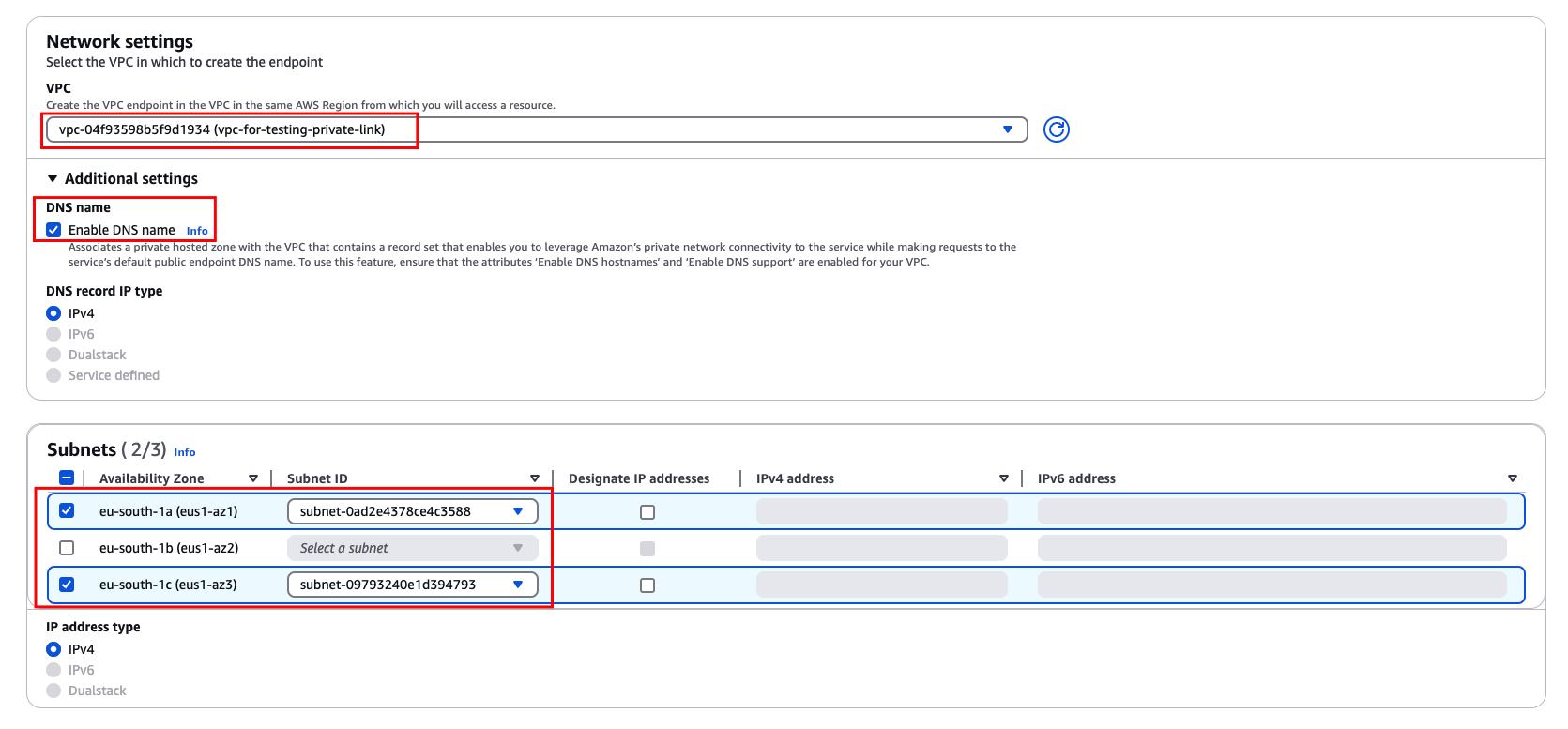
In the Network Settings, select the VPC in your region where you wish to create the endpoint.
Expand the "Additional settings" section and "Enable DNS name".
Under "Subnets", choose at least two availability zones for redundancy and high availability.
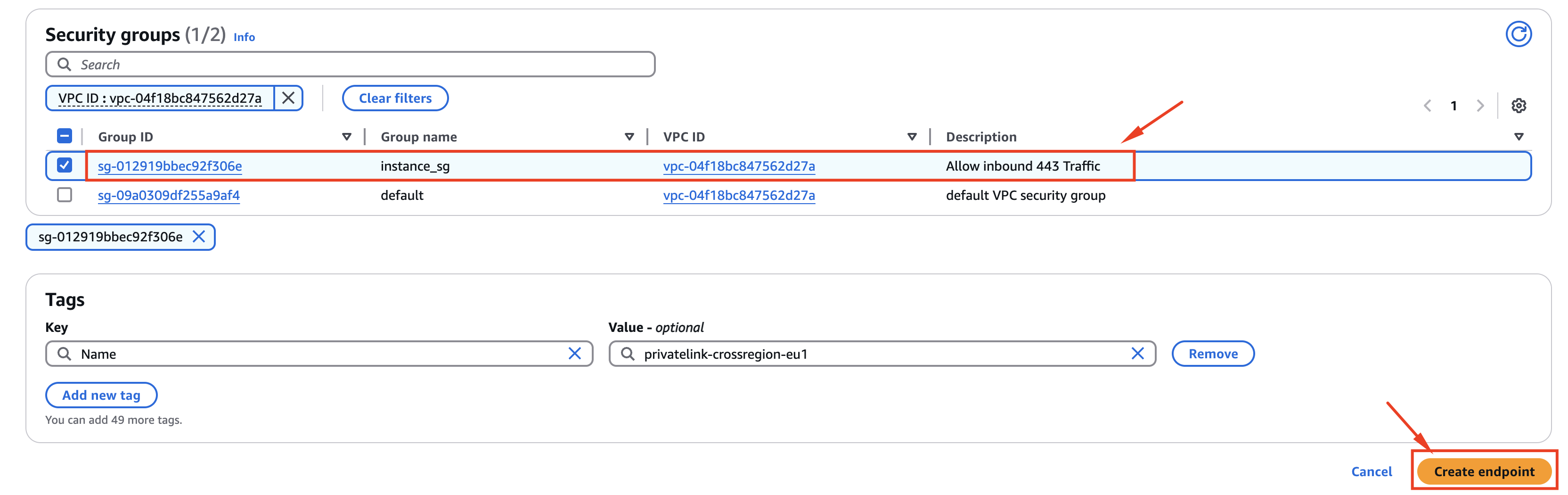
STEP 4. Select a security group to enable traffic to this VPC endpoint
The security group must accept inbound traffic in port 443 (TCP).
STEP 5. Verify endpoint status
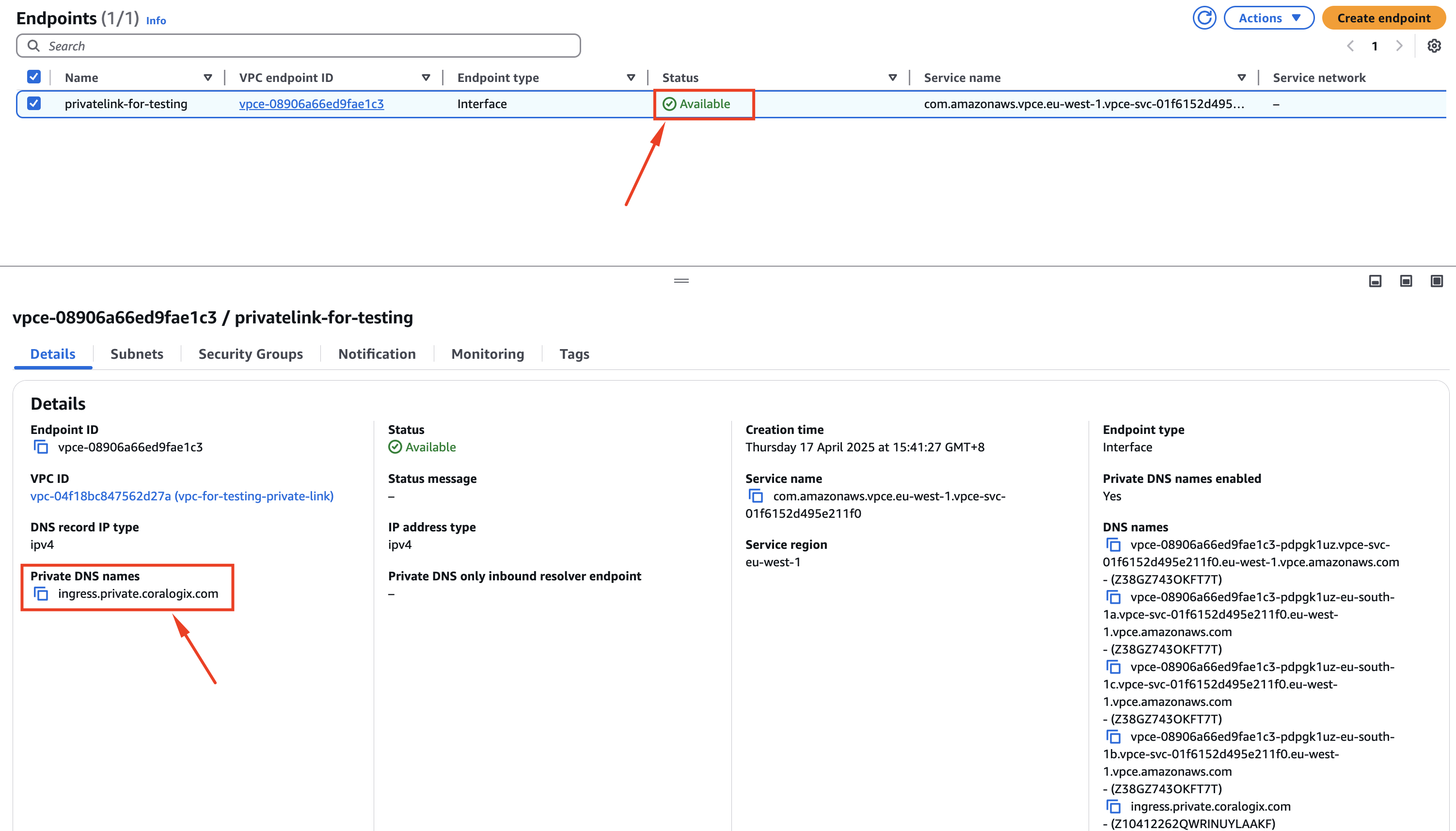
- Wait for the endpoint status to change from "Pending" to "Available". This may take a few minutes.
- Once available, note the DNS names generated for your cross-region endpoint. These will include:
- Private DNS names for each AZ (e.g.,
vpce-0123456789abcdef-abcdefgh-<region-az>.<region>.vpce.amazonaws.com) - A Coralogix domain-based private DNS name: ingress.private.<cx_domain>.
Note
With enabled DNS name in Step 3. This propagates the private dns endpoint (e.g. ingress.private.<region-domain>) to the private hosted zone. You can separately configure a DNS name to your vpce DNS (must be aligned to the coralogix domain SSL). Run the following command in a workload within the VPC to view cert:
STEP 6. Connect to the VPC network
Validate that the endpoint is working with either the following:
Connected VPC to a running workload (e.g. ec2 instance) and enter the following command, adjusted per cross-region:
Try sending a test log using the Coralogix REST API /singles
Best practices
For optimal performance, we recommend using at least two AZs for your VPC endpoint.
Limitations & considerations
- Cross-region connectivity is only supported for Interface type VPC endpoints.
- Both your region and the Coralogix service region must be in the same AWS partition.
- Cross-region endpoints count toward your Interface VPC Endpoints per VPC quota.