Home / User Guides / Security / Security Traffic Analyzer (STA) / Insights Detection Insights Detection STA is a tool for analyzing network traffic and host based activities. Using open-source services such as zeek and suricata, it enriches these events with other internal services.
To reduce the total cost of ownership of the STA, we have introduced a new insights service within the STA that will automatically detect possible threats and security related anomalies in your traffic.
Using the Coralogix Platform, configure alerts based on those insights and receive instant notifications if anomalies occur.
Insights Overview The following table contains a detailed list of the possible insights that can be detected by the sta-insights events.
Note:
To reduce the chances for false-positives, during the first three days the STA will only learn the patterns seen in the traffic. After that it will start sending events about anomalies to Coralogix.
Types of Insights Name Description Possible Attacks Message Sub Message File Similarity Insight changes to file paths that are very similar to others which encountered recently File encryption based Ransomware "Detected changes to file paths very similar to others seen recently " AnomalousSimhash::Document_Similarity_insight Connection To Suspiciously Looking Domain Name connections to suspicious domain using frequency score algorithms DGA activities Detected connection to suspiciously looking domain name AnomalousDomain-stats::Connection_to_suspiciously_looking_domain_name_insight Connection to baby domains connections to domains that created less than 90 days Phishing, C2C attacks Detected baby domain connection AnomalousDomain-stats::Baby-domain-connection_insight Connection to possible malicious IPs/Domains connection to IPs/Domains which flagged as malicious by at least one DNSRBL Phishing, C2C attacks Detected connection to IPs/Domains flagged as malicious by at least one DNSRBL AnomalousDNSRBL::Malicious_domain_ip_insight New top level domain encountered with new top level domain Phishing, C2C attacks Detected new top_level_domain AnomalousTLD::New_TLD_Insight Connection with redirection to another domain connection to URL which redirects to another domain Evasion techniques Detected connection to URL redirecting to another domain AnomalousUnsortenURL::url_redirecting_to_another_domain_insight DNS over TCP detects DNS queries over TCP download/upload payloads via DNS Detected dns over tcp AnomalousDns::Dns_over_tcp_insight Public IP echo requests detects requests for public IP using echo commands such as Geographical identification Detected Request for public IP echo AnomalousRdp::New_Rdp_cookie_insight SSH/RDP new country connection detects connection using SSH/RDP from a new country C2C attacks Detected ssh/rdp connection to new country for ip AnomalousNewCountryConnection::SSH_RDP_New_Country_Conn_Insight Number of lateral connections in given time detects more than 10 wide internal connections from one source in 10 minutes Network scan/propagation Detected more than lateral connections in AnomalousConn::10_lateral_connections_in_10min_insight number of NXDOMAIN responses in given time detects more than 100 NXDOMAIN responses in 10 minutes DGA activities Detected more than 100 NXDOMAIN responses in 10min AnomalousNXDOMAIN::100_NXDOMAIN_responses_in_10min_insight Connection to/from new country detects connection to/from new encountered country C2C attacks, DGA activity Detected connection to/from new country for ip AnomalousGeo::New_country_insight New FTP command detects new encountered FTP commands File transfer anomalies Detected new ftp command AnomalousFtp::New_Ftp_command_insight new HTTP method detects new encountered HTTP method Network anomalies, Log4Shell for example Detected new http method AnomalousHttp::New_HTTP_method_insight SSH/RDP with new destination connection detects connection using SSH/RDP to a new destination C2C attacks, DGA activity Detected ssh/rdp connection to new destination for ip AnomalousNewCountryConnection::SSH_RDP_New_Destination_Conn_Insight New MySQL instance detects new MySQL instance creation query Rogue server Detected New MySQL query AnomalousMySQL::New_MySQL_query_insight New AWS outbound connection Detects new AWS outbound connection C2C attacks Detected new outbound connection AnomalousConn::New_AWS_outbound_connection_insight new RDP cookie detects new RDP cookie brute force attempt, lateral movement, network propagation/scanning, etc. Detected new rdp cookie AnomalousRdp::New_Rdp_cookie_insight New software type detects new software type Malicious executable software, C2C attacks Detected new software type AnomalousSoftware::New_Software_type_insight New software with reported CVEs detects new software with reported CVEs Execution of known Exploited Vulnerabilities Detected connection to new software with CVEs AnomalousNIST::New_software_with_CVEs_insight New MySQL command detects new MySQL command C2C attacks, SQL injection Detected new MySql command AnomalousMySql::New_MySql_command_insight New tunnel type detects new tunnel type for traffic C2C attack, man in the middle Detected new tunnel type AnomalousTunnel::New_Tunnel_type_insight Outbound connection from DB server detects outbound connection from data base server C2C attack, data exfiltration Detected outbound connection from DB server on port AnomalousSatatsInfo::outbound_connection_from_DB_server_insight Outbound connection using services detects connections/attempts Data exfiltration, outbound scanning, etc. Detected outbound connection to service AnomalousConn::outbound__connection_insight invalid certification via TLS connection detects TLS connection with invalid certification Man in the middle Detected TSL connection with invalid certification AnomalousConn::TSL_connection_with_invalid_certification_insight Handle Insights After insight events are sent to Coralogix, you can find them under the Explore section with subsystem name sta_insight.
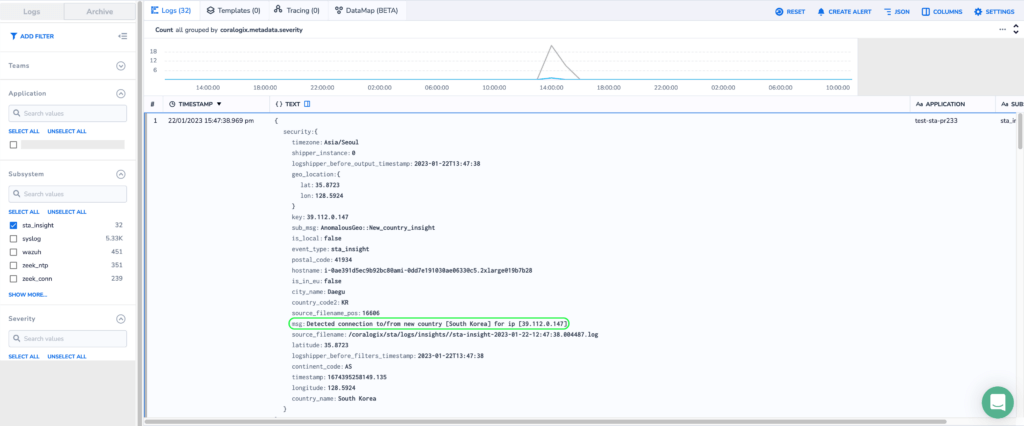 Example - New Country Connection Insight To enable alerts from within Coralogix, navigate to the Alerts section and set them accordingly. Find out more regarding alerts here .
Support Need help?
Our world-class customer success team is available 24/7 to walk you through your setup and answer any questions that may come up.
Feel free to reach out to us via our in-app chat or by sending us an email at support@coralogix.com .
Last updated: November 25, 2024 Theme
Light Theme
Light Home User Guides
DataPrime
Integrations
OpenTelemetry
Developer Portal