Fortinet Firewall Authentication Bypass Vulnerability (CVE-2024-55591)

Summary
As per a recent update from Fortinet, Exploitation of CVE-2024-55591, a recently disclosed authentication bypass vulnerability in FortiOS and FortiProxy, allows remote attackers to achieve super-admin privileges. By sending specially crafted requests to the Node.js WebSocket module, attackers can exploit this zero-day vulnerability to gain unauthorized access.
Fortinet reports that attackers exploiting the zero-day vulnerability in the wild are creating randomly generated admin or local user accounts on compromised devices. These accounts are then added to existing SSL VPN user groups or new groups created by the attackers.
Severity: CRITICAL
CVSSv3 Score: 9.6
Timeline
Nov 16-23, 2024 – Vulnerability scanning
Nov 22-27, 2024 – Reconnaissance
Dec 4-7, 2024 – SSL VPN configuration
Dec 16-27, 2024 – Lateral Movement
Jan 14, 2025 – Fortinet Published the Vulnerability
Products Affected

Mitigation/Solution
- Apply Security Patches: It is strongly recommended to apply the latest patches immediately to address the vulnerability. The vulnerability affects the following versions:
- Fortinet FortiOS: 7.0.0 to 7.0.16 (fixed in 7.0.17 or later)
- Fortinet FortiProxy: 7.2.0 to 7.2.12 (fixed in 7.2.13 or later) and 7.0.0 to 7.0.19 (fixed in 7.0.20 or later).
- Restrict Management Interface Access: Customers should ensure that firewall management interfaces are not publicly accessible and restrict access to administrative interfaces by allowing only specific IP addresses
- Monitor for Indicators of Compromise (IoCs): Review network logs for unusual activities, such as unexpected administrative actions or unauthorized configuration changes.
| Type | Values | Context |
| IP | 45.55.158[.]47 [most used IP address]137.184.65[.]71149.22.94[.]37155.133.4[.]175157.245.3[.]251167.71.245[.]1023.27.140[.]6531.192.107[.]16537.19.196[.]6564.190.113[.]2566.135.27[.]17887.249.138[.]47 | Threat Actor has been seen using these IP addresses for login to management interface |
| User | GujhmkEd8x4kG0xgeyPvnw81Alg7c4Ypda8aKmi8p41a2n6t8ah1t6M4ix9f | Randomly created user/admin users |
| IP | 1.1.1.1127.0.0.12.2.2.28.8.8.88.8.4.4 | login activity log with random scrip and dstip Note- Please note that the IP parameters are not the actual source IP addresses of the attack traffic, they are generated arbitrarily by the attacker as a parameter. Because of this they should not be used for any blocking. |
Snowbit Response
- We have onboarded the IOCs highlighted above into the Coralogix custom threat intel feed for real-time detection
- We have scanned SRC customer environments with Fortinet Firewall integrations for the aforesaid IOCs
- We have implemented the necessary alerts to monitor activities associated with this vulnerability. Here is the list of newly added alerts
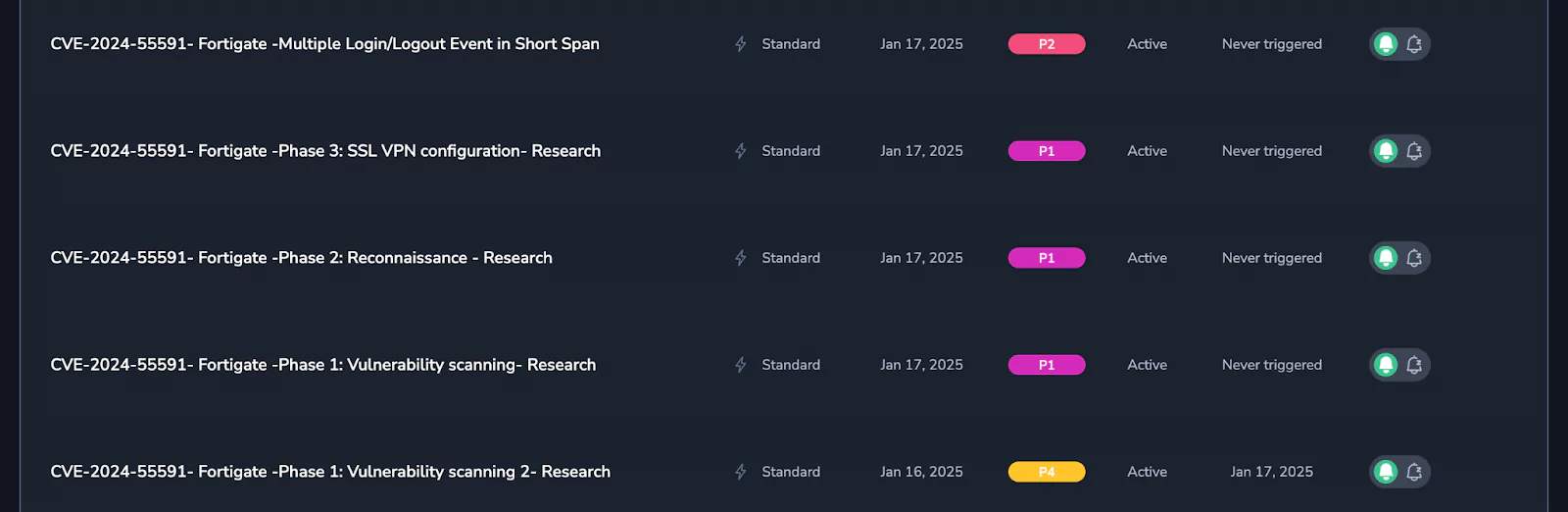
- If you need further assistance with respect to this vulnerability, our Security Resource Centre (SRC) and Research team would be happy to engage. Please reach out to your Account Manager, TAM or SRC SPoC in this regard
Reference
[1] https://www.fortiguard.com/psirt/FG-IR-24-535
[2] https://arcticwolf.com/resources/blog/console-chaos-targets-fortinet-fortigate-firewalls/
[3]https://www.rapid7.com/blog/post/2025/01/16/etr-fortinet-firewalls-hit-with-new-zero-day-attack-older-data-leak/[4]https://www.bleepingcomputer.com/news/security/fortinet-warns-of-auth-bypass-zero-day-exploited-to-hijack-firewalls/

