Rapid7 InsightVM: Key Features, Pros/Cons & Quick Tutorial

Key Features of Rapid7 InsightVM
Lightweight Endpoint Agent
The Rapid7 Insight Agent is a tool for continuous data collection from endpoints across an organization. Unlike traditional scanning methods, the Insight Agent operates in real time, gathering data even from assets that are difficult to scan actively. These include devices used by remote workers, systems that rarely connect to the corporate network, or sensitive assets that cannot be subjected to frequent scans.
Live Dashboards
Traditional software dashboards provide static snapshots that quickly become outdated. InsightVM’s Live Dashboards offer dynamic, real-time visibility into the organization’s risk landscape. These dashboards allow security teams to track progress, monitor trends, and explore data. Users can create views tailored to the needs of various stakeholders, from system administrators to executives like CISOs. The dashboard cards can be queried in plain language.
Active Risk Score
CVSS scores often result in thousands of vulnerabilities being flagged as critical, leaving security teams overwhelmed and unsure where to focus their efforts. The Active Risk Score provides an actionable approach by assigning each vulnerability a score from 1 to 1000. This score is based on the likelihood that a vulnerability will be exploited in a real-world attack. It incorporates data from threat intelligence feeds, including Rapid7’s proprietary research from resources like Project Lorelei and AttackerKB.
IT-Integrated Remediation Projects
Managing remediation workflows can be cumbersome, often involving lengthy reports, manual tracking, and inefficient communication between security and IT teams. InsightVM’s IT-Integrated Remediation Projects transform this process by providing a centralized platform for assigning, tracking, and managing remediation tasks in real time. Security teams can create projects that include vulnerabilities to be addressed and assign them directly to IT personnel. These tasks are then integrated into IT’s existing workflows, such as ticketing systems.
Attack Surface Monitoring with Project Sonar
InsightVM integrates with Rapid7’s Project Sonar, which continuously scans the public internet to identify exposed assets and vulnerabilities. This provides organizations with valuable insights into their external attack surface, including unmanaged or unknown assets that could pose security risks. By leveraging this data, security teams can ensure that they have a complete inventory of all external-facing systems.
Related content: Read our guide to threat hunting tools
Rapid7 InsightVM Pricing
Rapid7 InsightVM offers volume-based pricing, tailored to the number of assets an organization needs to monitor. The pricing model starts at $1.93 per asset per month when managing 500 assets, amounting to approximately $23.18 per asset annually. This pricing assumes a minimum commitment of 512 assets and requires annual billing.
The platform provides scalability, making it suitable for organizations of varying sizes. For larger environments with over 1,250 assets, volume discounts are available. For specific requirements or detailed cost breakdowns, customers can request a personalized quote.
In addition to the vulnerability management capabilities, the pricing includes features such as on-premises and remote endpoint assessments, unlimited scanning capabilities, attacker-based risk scoring, IT-integrated remediation tools, and access to Rapid7’s integrated threat intelligence feeds.
Rapid7 InsightVM Limitations and Challenges
While Rapid7 InsightVM is a vulnerability management solution, it does come with several limitations that organizations should consider. These limitations were reported by users on the G2 platform:
- Complex setup process: Initial deployment can be challenging due to the platform’s complexity. Setting up and configuring the tool often requires significant administrative effort and technical expertise, which can delay implementation.
- High cost: Compared to similar tools on the market, InsightVM is relatively expensive. This high cost may make it less appealing for smaller organizations or those with budget constraints.
- False positives: Some users have reported instances of false positives in scan results. This can lead to unnecessary remediation efforts, wasted resources, and potential frustration for IT and security teams.
- Buggy security console: The security console has been described as buggy by some users, potentially impacting its reliability during critical operations.
- Unreliable Jira integration: The native integration with Jira has been noted as unreliable, frequently breaking and disrupting workflows for organizations relying on this feature for vulnerability tracking and management.
- Delayed detection of vulnerabilities: In certain cases, InsightVM has taken days to identify vulnerabilities, even for high-risk ones. For example, it reportedly required three days to detect assets vulnerable to the JetBrains TeamCity CVSS10 issue.
- Limited filtering and encryption processing: The platform’s filtering capabilities are less advanced than some competitors, making it harder to fine-tune vulnerability results. Additionally, it does not process encrypted packets, which is a limitation for organizations that regularly use encryption.
- Complex reports: The generated reports are not intuitive, particularly for individuals without a technical or cybersecurity background. This makes it difficult for non-technical stakeholders to interpret findings, and the limited customization options further compound this issue.
Quick Tutorial: Getting Started with Rapid7 InsightVM
To install InsightVM on a Linux system, you will need:
- The latest Linux installer and its checksum file for verifying the download integrity.
- A valid product key for license activation.
- Ensure SELinux is disabled.
- It’s also recommended to install tmux or screen for interactive terminal sessions.
- According to our testing, to get reasonable performance, you will need to install InsightVM on a machine with 4 or 8 CPUs and at least 16GB RAM.
Installation Steps:
1. Disable SELinux: Open the file /etc/selinux/config with a text editor. Locate the line starting with SELINUX= and change its value to disabled. Save the changes and reboot the system using:
shutdown -r now
2. Verify the Installer: Download the installer and the checksum file. Validate the file using:
sha512sum -c <installer_file_name_checksum_file>
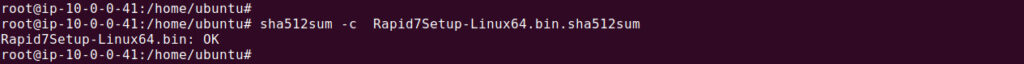
Ensure the checksum matches. If successful, you will see an “OK” message.
3. Make the Installer Executable: Grant execution permissions –
chmod +x <installer_file_name>
4. Run the Installer: Execute the installer with –
./<installer_file_name>
Follow the prompts to complete the installation.
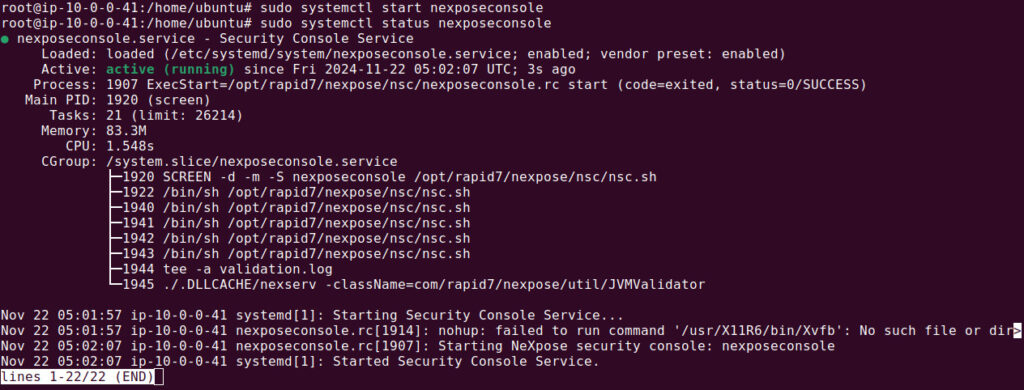
Check the Security Console service is running using the following command:
sudo systemctl status nexposeconsole
If not, please start it using this command:
sudo systemctl start nexposeconsole
You can access the security console by browsing to http://<YOUR IP OR HOSTNAME>:3780. Upon first access, you will be taken to the following:
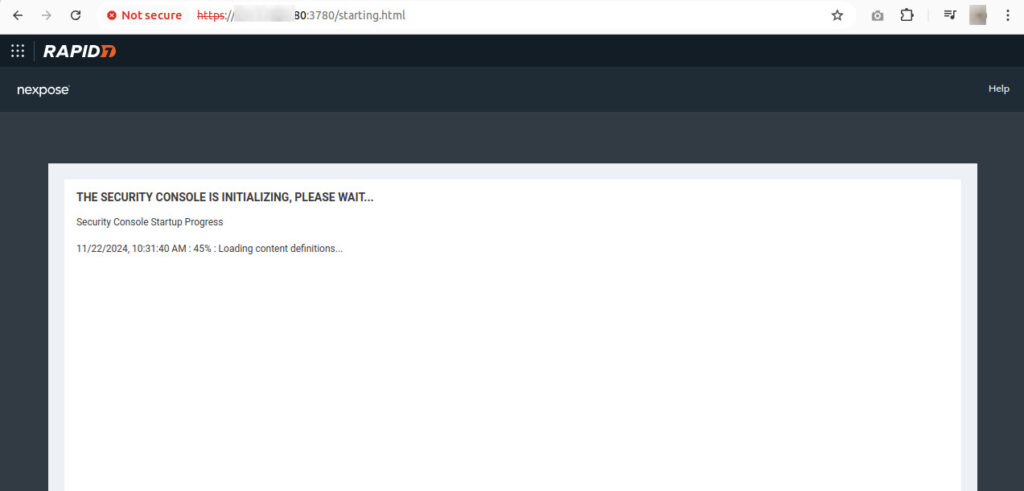
Exploring the InsightVM Security Console
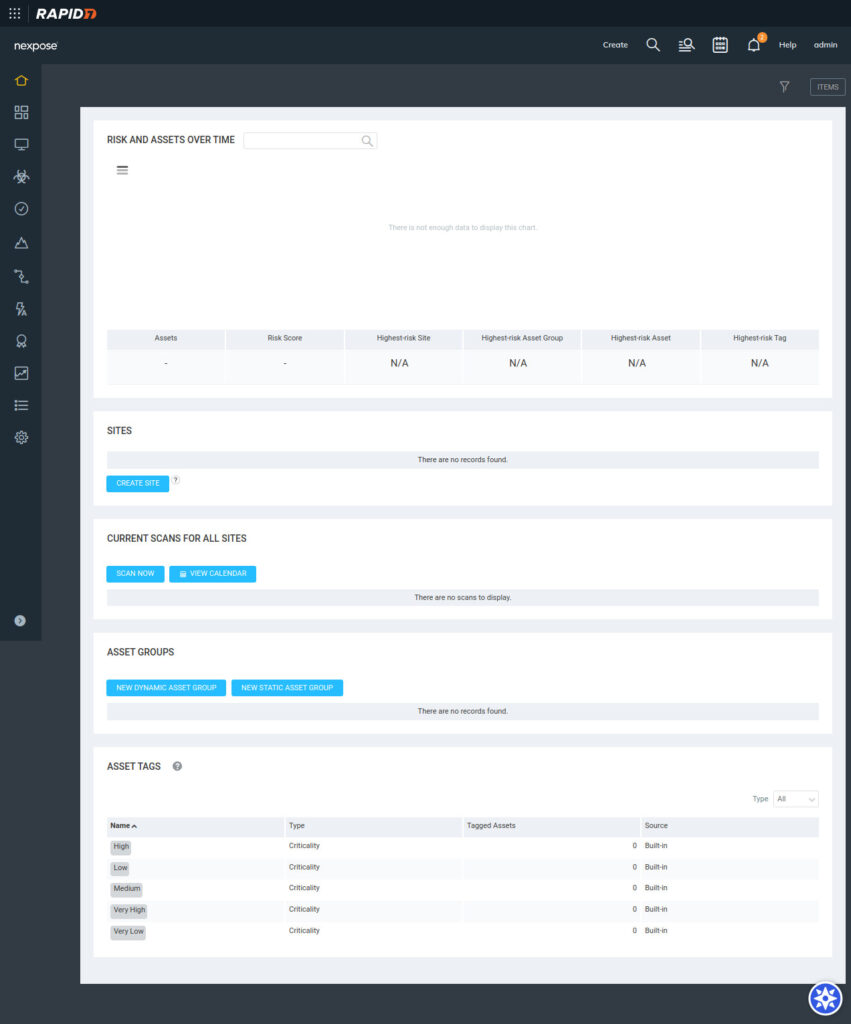
Once installed, the Security Console provides an overview of the IT environment. Key areas of the home page include:
1. Default Dashboard Panels
- Risk and Assets Over Time: Displays graphs for the total number of assets and your overall risk score. These metrics help you track vulnerability trends and management effectiveness.
- Sites: Lists all configured sites, their status, and scan metrics. Provides quick links to detailed scan results and site settings.
- Current Scans for All Sites: Shows scans in progress, with real-time updates on their status.
- Asset Groups: Displays groups of assets for ongoing monitoring, categorized by criteria like device type or risk level.
- Asset Tags: Shows tags applied to assets, making it easier to filter and organize based on attributes such as function or criticality.
2. Filtered Asset Search: Filter scanned assets by parameters like vulnerability severity, location, or operating system. This is essential for identifying high-risk assets or creating targeted reports.
3. Create Dropdown: A shortcut for tasks like creating new sites, asset groups, or reports.
4. Calendar: Displays all scheduled scans and reports, allowing you to manage timing and avoid conflicts.
Creating and Scanning a Site
From the home page, follow these steps.
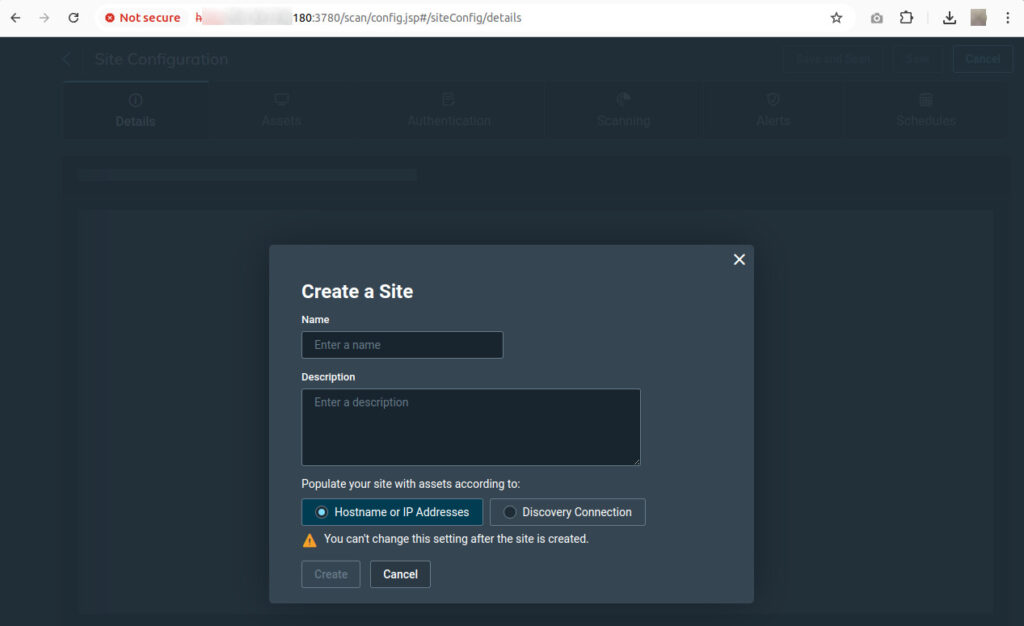
Define a Site
- Click the Create dropdown and select Site.
- Enter a name and description in the Info & Security section.
- In the Assets section, specify the assets to scan by IP address, range, or name.
Configure Authentication
- Go to Authentication and click Add Credentials.
- Provide a name and description for the credentials.
- Under the Account tab, select the authentication method and enter the required details.
- Test the credentials by providing an IP address or FQDN and port number. Successful tests will show a confirmation message.
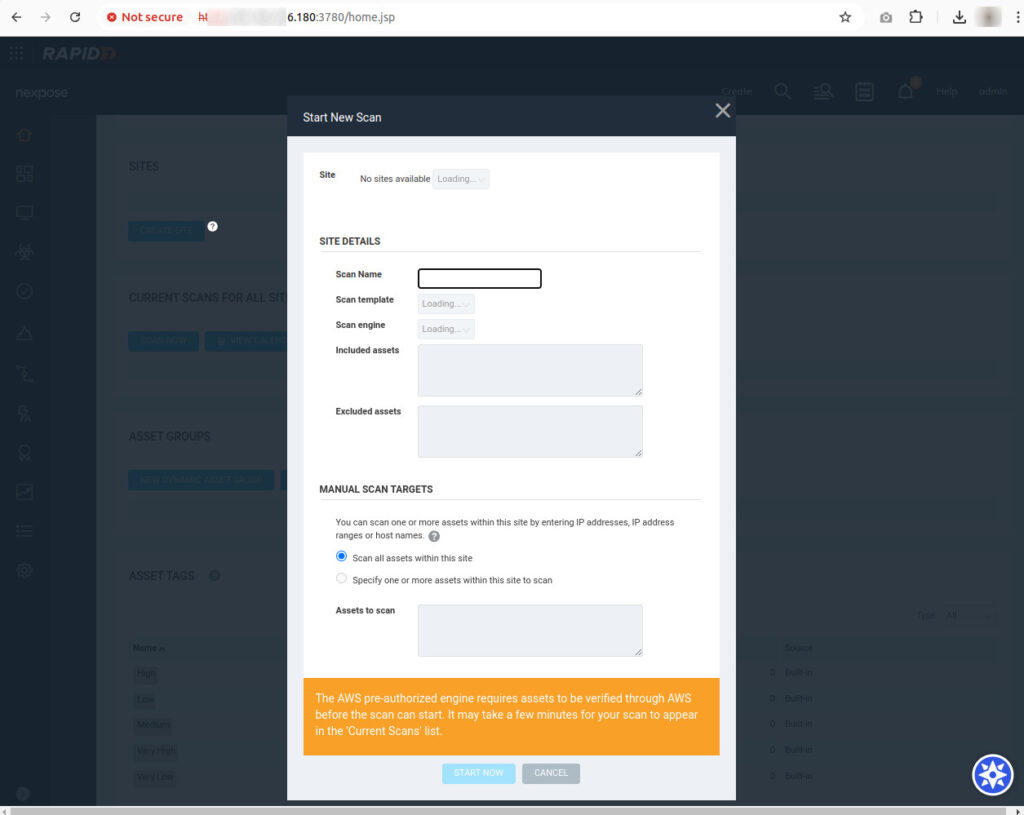
Perform a Full Scan
- Under the Scan Template tab, choose Full Audit without Web Spider.
- Select a scan engine under the Select Engine tab.
- Click Save & Scan to initiate the scan.
- Monitor the scan’s progress in the Scan Progress section. Once complete, review the results, including risk scores for each asset. Use this data to prioritize and remediate vulnerabilities.
Coralogix: Ultimate Alternative to Rapid7 InsightVM
Coralogix sets itself apart in observability with its modern architecture, enabling real-time insights into logs, metrics, and traces with built-in cost optimization. Coralogix’s straightforward pricing covers all its platform offerings including APM, RUM, SIEM, infrastructure monitoring and much more. With unparalleled support that features less than 1 minute response times and 1 hour resolution times, Coralogix is a leading choice for thousands of organizations across the globe.



