Track SBOM Compliance with Coralogix
A Software Bill of Materials (SBOM) is essentially an inventory of the components used to build a software artifact, such as an application. While the concept of tracking an application’s components is not new, its importance has grown in recent years due to the rising threat of software supply chain attacks.
One significant example is the SolarWinds attack, which highlighted how threat actors are increasingly targeting vulnerabilities in software components during the delivery process. These attackers often have access to extensive resources—time, funding, and expertise—enabling them to develop sophisticated tools that can bypass traditional security measures like patches and system upgrades.
In response to these growing threats, several developer platforms, including GitHub, GitLab, and Snyk, have already begun implementing SBOM functionality. Recognizing its importance, on July 13, 2023, the White House introduced the National Cybersecurity Strategy Implementation Plan (NCSIP), which includes SBOM as a key element in enhancing national cybersecurity oversight. The plan emphasizes that “increasing software transparency allows market actors to better understand their supply chain risk and hold vendors accountable for secure development practices.”
According to Gartner, every organization should generate an SBOM for each software package they develop, as well as verify the SBOMs of all third-party software they use. Without continuous SBOM management, companies are left vulnerable, unable to properly assess security risks or ensure that vulnerabilities are identified and addressed.
Effective SBOM management goes beyond merely generating a list of components. It enables organizations to gain actionable insights into open-source components and their impact on the software supply chain. While creating an SBOM is a critical first step in DevOps/SecDevOps, continuously managing it is essential for maintaining security. An SBOM that sits unused in a build directory provides no value. Instead, organizations must generate, store, analyze, and monitor SBOMs throughout the entire software lifecycle to track changes in dependencies, improve compliance, and enhance supply chain security.
SBOMs typically come in two widely-used formats: CycloneDX and SPDX. CycloneDX, designed to reduce cyber risk, is supported by third-party vendors and can be formatted in JSON or XML. SPDX, originally focused on license management, has since expanded to track project dependencies as well.
Choosing the right format depends on the specific business needs and security requirements of a given project.
How Coralogix Can Help
Coralogix aids in detecting and preventing software tampering, enabling seamless SBOM ingestion for each repository committed to GitHub, providing the following features:
- Automated SBOM generation via GitHub Actions
- A structured format that includes only relevant fields
- The ability to enrich SBOMs with metadata
- Visualization of software components
Coralogix enables proactive detection of unauthorized changes and malicious modifications within software components. It monitors and alerts customers on certificate changes, summarizes licenses, and tracks new packages to enhance security and compliance across the software supply chain.
Github using SPDX format – Software Package Data Exchange – an open-source specification for documenting the components, licenses, and copyrights of software packages. Its main goal is to provide a standard way of exchanging information about the software packages and their contents, making it easier to manage the compliance and distribution of open-source software.
Configuration
- Create Webhook
This feature enables you to automatically generate the webhook URL necessary to send to Coralogix Guthub SBOM Results
In your Coralogix UI, navigate to DataFlow →
STEP 1. In your Coralogix navigation pane, click Data Flow > Contextual Data.
STEP 2. In the Contextual Data section, click Generic Webhook ADD.
STEP 3. Click ADD NEW.
STEP 4. Fill in the integration details:
- Webhook Name: Name your webhook according to Github Repo you looking to ingest.
- Your API Key. Click CREATE NEW KEY to generate an API Key and name it.
- Enter an Application and Subsystem Name to use in the webhook. Make sure you create Application and Subsystem according to repo you integrating with.
- Content Type. Select either JSON or Text. If JSON is selected, the webhook expects requests with content-type as either
application/jsonorapplication/x-ndjson. - Timestamp. Select whether to generate the timestamp using the system time when the event was ingested or to extract it from the body of the event.
STEP 5. Click GENERATE URL. The URL for the webhook will be automatically created. Copy the URL – we will use it later.
- Create workflow file within your repo in Github
STEP 1. Create your Action as a .yml file inside our repository in the workflows directory .github/workflows/sbom.yml.
Note:
- Remember to place the .github folder inside the root folder of your repository.
STEP 2. Add the content of your action.
name: SBOM Generator
on:
push
jobs:
build:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v3
- uses: advanced-security/sbom-generator-action@v0.0.1
id: sbom
env:
GITHUB_TOKEN: ${{ github.token }}
- uses: actions/upload-artifact@v4
with:
path : ${{steps.sbom.outputs.fileName }}
compression-level: 0
name : sbom
- name: 'Setup jq'
uses: dcarbone/install-jq-action@v2
with:
version: '${{ inputs.version }}'
force: '${{ inputs.force }}'
- name: 'Check jq'
# language=sh
run: |
which jq
jq --version
- run: |
mv spdx*.spdx.json sbom.json
cat sbom.json| jq -r '.packages[]? | {"sbom":{packagename:.name,versionInfo:.versionInfo,licenseDeclared:.licenseDeclared,downloadLocation:.downloadLocation,licenseConcluded:.licenseConcluded,copyrightText:.copyrightText,SPDXID:.SPDXID,referenceLocator:.externalRefs[].referenceLocator,referenceCategory:.externalRefs[].referenceCategory,referenceType:.externalRefs[].referenceType}}' | while read -r repo; do echo "$repo"; done | jq -r tostring | jq -s '.' > sbom_output.json
curl -X POST '<https://ingress.**CORALOGIX_DOMAIN**/webhooks/v1/_hLsZCzkHFHkxB8sIXKbN?cx-api-key=**APIKEY**&cx-application-name=**My-App**&cx-subsystem-name=**My-subsystem**>' -H 'Content-Type: application/json' -d @sbom_output.json -v<My-app>– Your Application name.<My-subsystem>– Your Subsystem name.
| Coralogix Domain | Coralogix Region | AWS Region | Team Hostname |
|---|---|---|---|
| coralogix.us | US1 | us-east-2 (Ohio) | <team>.app.coralogix.us |
| cx498.coralogix.com | US2 | us-west-2 (Oregon) | <team>.app.cx498.coralogix.com |
| coralogix.com | EU1 | eu-west-1 (Ireland) | <team>.coralogix.com |
| eu2.coralogix.com | EU2 | eu-north-1 (Stockholm) | <team>.app.eu2.coralogix.com |
| coralogix.in | AP1 (IN) | ap-south-1 (Mumbai) | <team>.app.coralogix.in |
| coralogixsg.com | AP2 (SG) | ap-southeast-1 (Singapore) | <team>.app.coralogixsg.com |
STEP 3. After publishing a new release, the Action will run, and result of SBOM will be published in your Coralogix account.
{
"sbom": {
"SPDXID": "SPDXRef-npm-spdy-transport-3.0.0",
"copyrightText": "Copyright Fedor Indutny, 2015",
"downloadLocation": "NOASSERTION",
"licenseConcluded": "MIT",
"licenseDeclared": null,
"packagename": "npm:spdy-transport",
"referenceCategory": "PACKAGE-MANAGER",
"referenceLocator": "pkg:npm\/spdy-transport@3.0.0",
"referenceType": "purl",
"versionInfo": "3.0.0"
}
}
SBOM is Imported, What Next?
With the advanced Coralogix capabilities you can monitor changes in your software lifecycle.
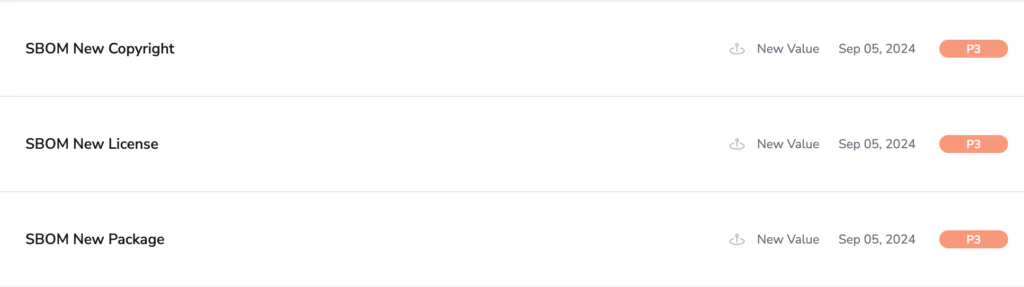
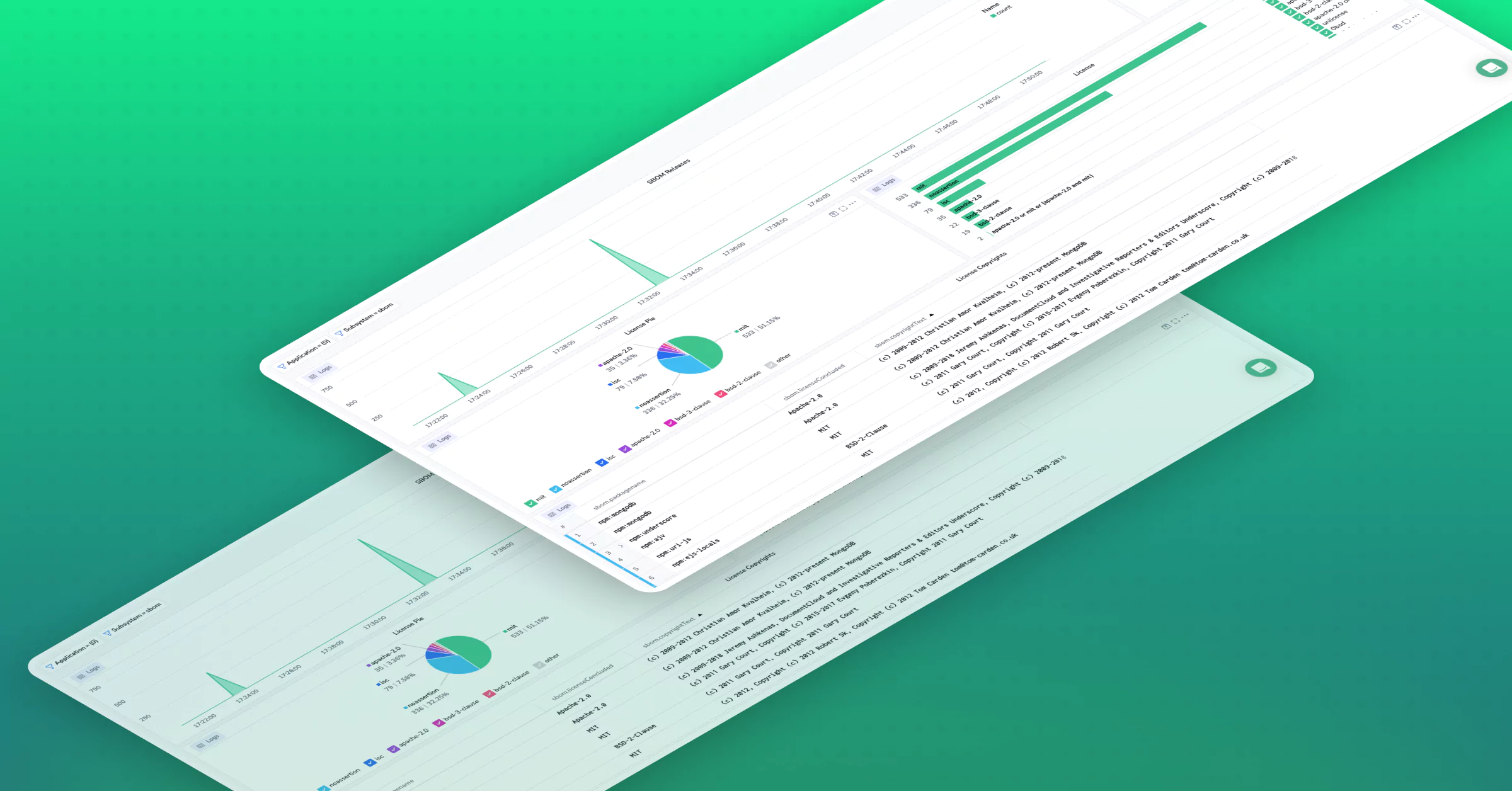
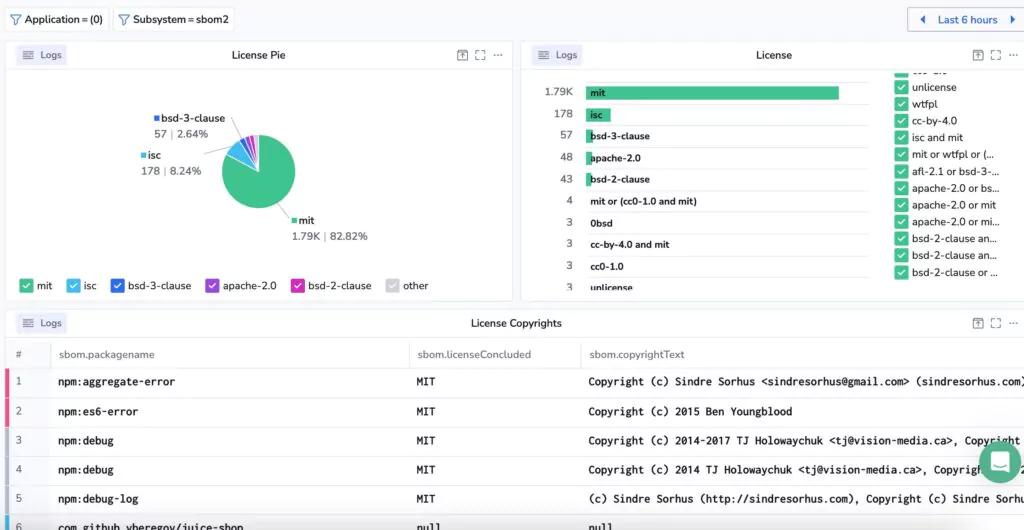
With this new data, Coralogix provides transparency and accountability in the software supply chain, enabling organizations to manage potential security and legal risks. Enable enrichment, custom dashboard’s and Alerts for pathway:
- Track and avoid SolarWinds Hack
- Observe and track changes in packages and dependencies
- Track compliance, copyright and licensing
- Alert and Visualize newly introduced packages within the repo
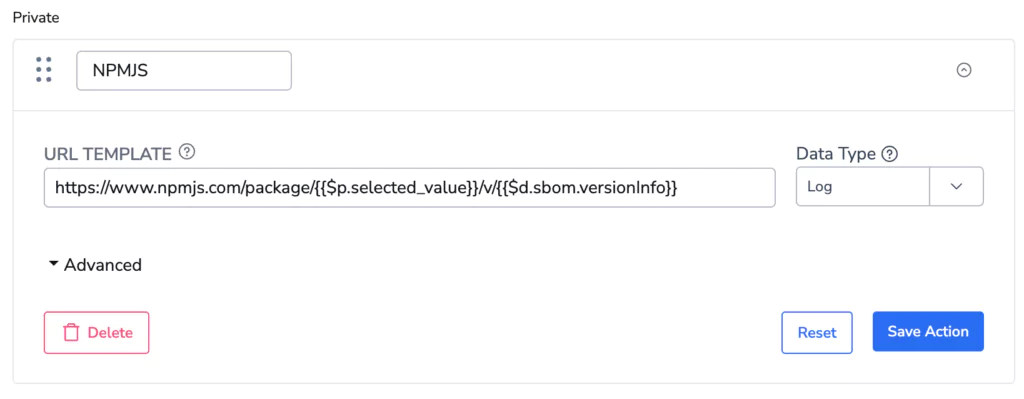
Create 3rd party request to get more insights of your application – example to npmjs database to query specific package.
Support
Need help?
Our world-class customer success team is available 24/7 to walk you through your setup and answer any questions that may come up.
Feel free to reach out to us via our in-app chat or by sending us an email at support@coralogix.com.