The Coralogix blog
Expert insights, bold ideas, and company news
All Articles
- All
- Alerts
- OpenTelemetry
- Uncategorized
- Software development
- AI
- AWS
- Product
- CDN monitoring
- CloudWatch
- Logging
- Real user monitoring
- Data
- Gaming
- APM
- Cloud
- Fintech
- FinOps
- Kubernetes
- Microservices
- Compliance
- Observability
- Metrics
- Security advisory
- Tracing
- CI/CD
- IaC
- Elasticsearch
- Migrations
- DevOps & IT operations
- Troubleshooting
- Company news
- Case studies
- Security
- Performance
- Tutorials
- Audit logs
- Logs
- Application performance monitoring
- Monitoring
- Log analytics

GitHub Action Supply Chain Attack (CVE-2025-30066)
Summary On March 14, 2025, a critical supply chain attack targeted the widely used GitHub Action tj-actions/changed-files. This action, utilized in over 23,000 repositories, was compromised when attackers...

The Digital Operational Resilience Act (DORA) is coming – are you ready?
As the official implementation date approaches for the Digital Operational Resilience Act (DORA) – financial...
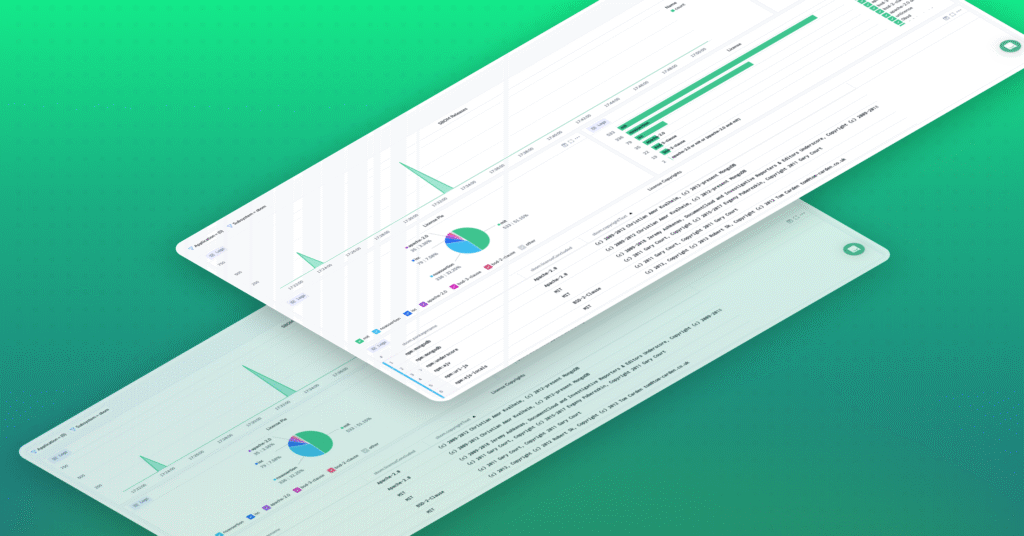
Track SBOM Compliance with Coralogix
A Software Bill of Materials (SBOM) is essentially an inventory of the components used to build a software artifact, such as an application. While the concept of tracking...
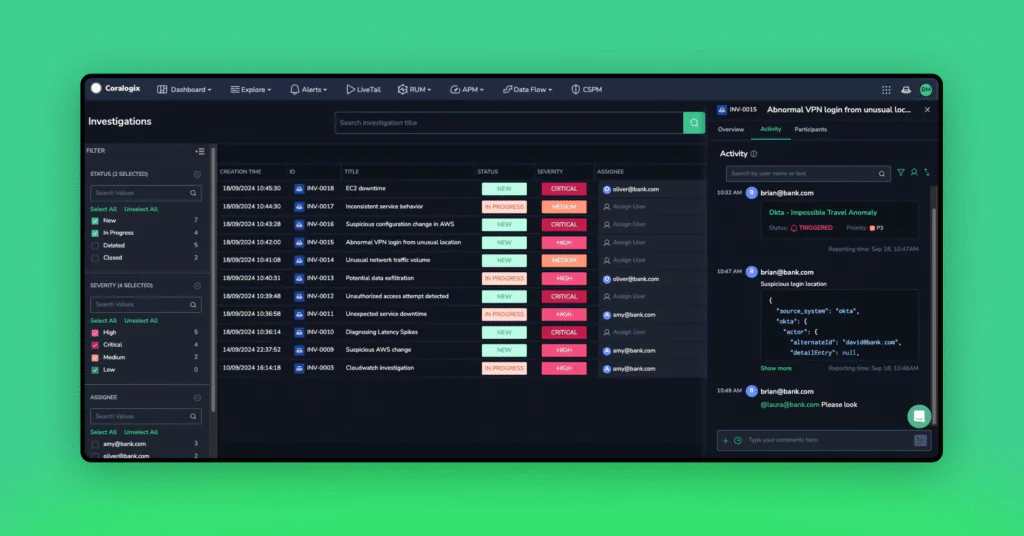
See the Bigger Picture: How Coralogix Investigations Speeds Up Root Cause Analysis
In the fast-paced world of business, timely and accurate incident investigations are crucial. The ability...

PCI DSS compliance with SIEM, CSPM and MxDR
In a world where increasing numbers of transactions are done online, compliance with PCI DSS (Payment Card Industry Data Security Standard) is crucial. However, with more organizations turning...

Dynamic Bad Actor Scoring in Coralogix
Bad bots, hackers, and other malicious agents can be tracked by a huge volume of metrics – session activity, HTTP headers, response times, request volume & cadence, and...

Palo Alto Global Protect Command Injection Vulnerability
On April 12, 2024, Palo Alto disclosed a critical vulnerability identified as CVE-2024-3400 in its...

Advanced Security: Marking AWS WAF’s Homework
The same security scenarios are checked thoroughly. Privilege escalation, SQL injection, Port scanning and so on. These checks form the bedrock of defensive security, but as solutions become...

Coralogix Alarms: Faster than WAF IP Detection and Remediation
There is one area of technology that requires the fastest possible response time, where every...

Azure Security Compromised – Hundreds Fell Victim to Phishing
In late November 2023, a phishing campaign successfully compromised hundreds of user accounts, including those...

AWS IAM Best Practices
In today’s interconnected digital landscape, robust IAM (Identity and Access Management) practices are critical pillars of an organization’s cybersecurity strategy. IAM serves as the fortress guarding sensitive data,...

What is the Benefit of Including Security with Your Observability Strategy?
Observability strategies are needed to ensure stable and performant applications, especially when complex distributed environments...

