SIEM in AWS: Native and Third Party Solutions
Benefits of Implementing SIEM in AWS
Implementing SIEM in AWS provides several key advantages, including:
- Centralized security monitoring: SIEM aggregates logs from multiple sources, providing a unified view of security activities across the entire AWS environment. This centralization helps simplify security operations and reduces the complexity of monitoring disparate systems.
- Enhanced threat detection: By leveraging AWS-native services such as GuardDuty, CloudTrail, and Security Hub, SIEM solutions can detect threats in real time. These services continuously monitor for suspicious activities and provide actionable insights to help mitigate potential risks promptly.
- Improved incident response: With extensive log data and analytics, SIEM solutions enable faster and more effective incident response. Security teams can quickly identify, investigate, and respond to incidents, minimizing potential damage and reducing downtime.
- Compliance and reporting: SIEM in AWS helps organizations meet regulatory compliance requirements by providing detailed audit trails and standardized reporting.
- Scalability and flexibility: AWS SIEM solutions scale with the cloud environment. As the infrastructure grows, the SIEM system can handle increasing amounts of data without compromising performance. Additionally, the flexibility of AWS services allows for easy integration with various third-party tools and custom configurations.
- Cost efficiency: Using AWS-native SIEM solutions can be more cost-effective compared to traditional on-premises systems.
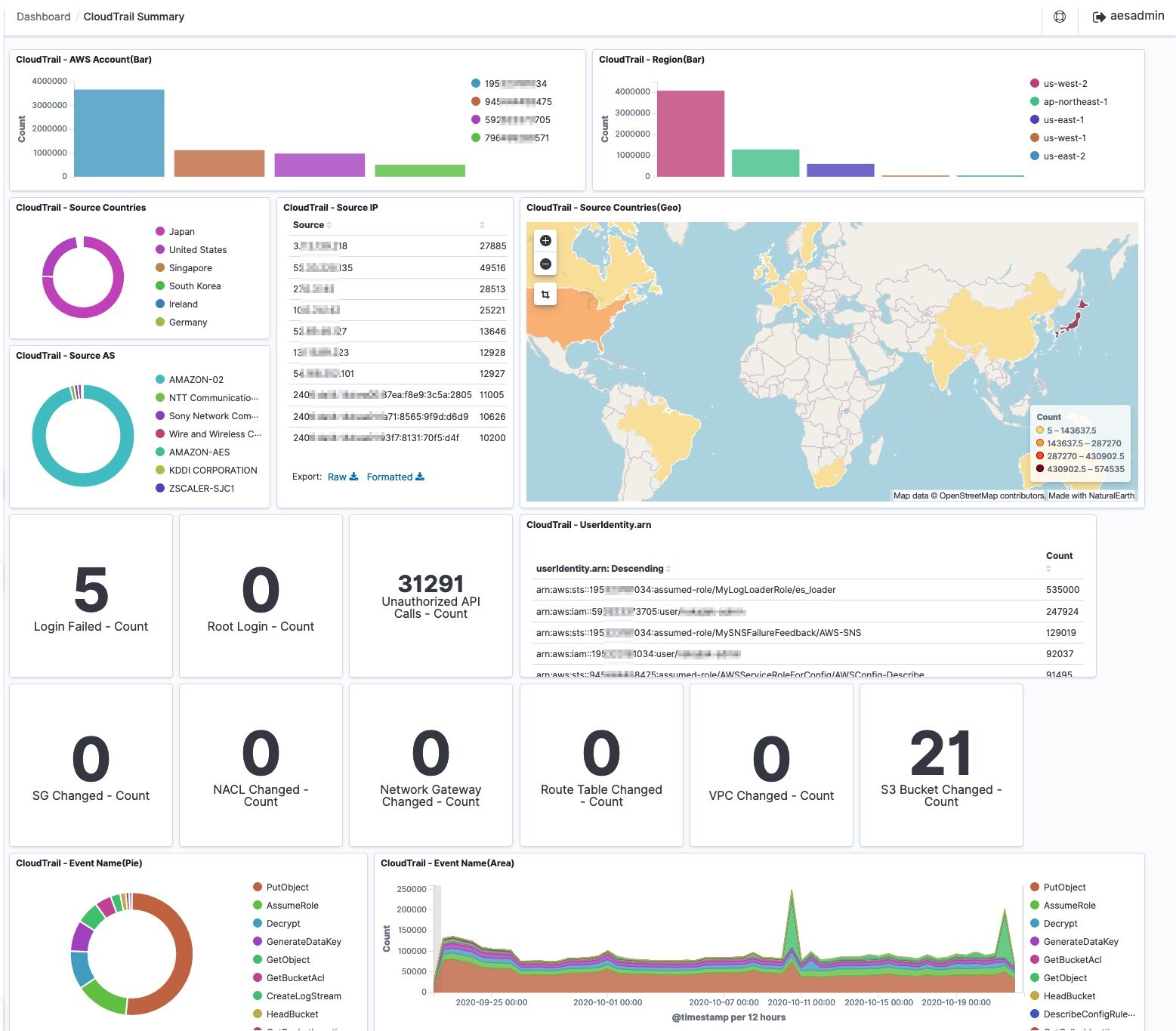
Example of Native AWS SIEM Solution: SIEM on Amazon OpenSearch Service
SIEM on Amazon OpenSearch Service aids in collecting, correlating, and visualizing logs from multiple AWS accounts. This system enhances the ability to investigate security incidents by consolidating various types of logs into a single platform.
Source: AWS
Deployment Process
Deployment of SIEM on OpenSearch Service is simple and can be completed in about 30 minutes using AWS CloudFormation or AWS Cloud Development Kit (CDK). Once the deployment is set up, logs from AWS services are automatically loaded into the system through a designated Amazon S3 bucket. A purpose-built AWS Lambda function enables the automatic transfer of these logs into OpenSearch, where they can be visualized and analyzed.
Log Visualization and Correlation
The service allows users to visualize logs on a dashboard, making it easier to correlate multiple logs and investigate security incidents. This capability helps in identifying patterns and potential threats across different AWS accounts.
Location and Threat Information Enrichment
SIEM on OpenSearch Service can enrich log data with geographic and threat information. It integrates with GeoLite2 by MaxMind to add country and location data based on IP addresses. For threat information, it supports integration with various sources such as Tor Project, Abuse.ch Feodo Tracker, and AlienVault OTX. Users can also incorporate their own indicators of compromise (IoCs) in TXT and STIX 2.x formats to enhance threat detection capabilities.
Configuring OpenSearch Dashboards
After deployment, users can configure OpenSearch Dashboards by accessing the AWS CloudFormation console and retrieving login credentials from the Outputs section. Once logged in, users can select a global or private tenant and import configuration files to customize their dashboards.
Third-Party SIEM Solutions Supporting AWS
Coralogix

Coralogix SIEM delivers a powerful, cost-effective solution that significantly reduces data processing expenses while enhancing security visibility across your organization. By enabling in-stream data analysis, Coralogix optimizes data management, streamlines threat detection, and simplifies overall system management, providing unmatched efficiency and security.
Key Features:
- Comprehensive Security: Over 2,500 pre-configured alerts across 200+ data sources, hundreds of pre-built integrations, intuitive visualizations, 24/7 customer support, and real-time threat detection for proactive security.
- Significant Cost Reduction: In-stream data analysis reduces processing costs by more than 50% compared to traditional SIEM solutions.
- Unified Observability: Centralizes logs from various sources, enhancing data correlation and providing a holistic view of your environment.
- Advanced Management Tools: Features robust user and team management, including SSO, RBAC, and detailed audit trails for secure and flexible operations.
Splunk Cloud

Splunk Cloud integrates with AWS Control Tower, allowing administrators to automatically configure and set up AWS services. It incorporates data from AWS CloudTrail, AWS Config, and other sources using Kinesis Data Firehose and the Splunk HTTP Event Collector (HEC). This helps provide insights into security and operational metrics.
Features:
- Compliance reporting with control: Provides pre-configured Tower Guardrail dashboards for compliance reporting, ensuring organizations meet regulatory requirements and maintain visibility over their security posture.
- Automated AWS account enrollment: New AWS accounts can be automatically enrolled into Splunk’s data collection process, simplifying the setup of continuous monitoring without manual intervention.
- Simplified data collection: Integrates with Kinesis Data Firehose and HEC to simplify the process of ingesting data from various AWS services, such as from AWS CloudTrail, AWS Config, and AWS CloudWatch Logs.
Source: Splunk
Sumo Logic

Sumo Logic Cloud-Native Machine Data Analytics aggregates critical operational data from across services and accounts, offering a unified view of AWS environments. Its dashboards enable teams to quickly resolve issues, minimize downtime, and enhance system availability. The platform automates the collection, ingestion, and analysis of application, infrastructure, security, and IoT data to derive actionable insights.
Features:
- Self-service provisioning and security certifications: Allows teams to set up and manage their analytics environment. Adheres to high security standards, ensuring data protection and compliance.
- Unified service visibility: The platform provides detailed dashboards that offer visibility into different levels of the AWS infrastructure, including accounts, Regions, Availability Zones, and services.
- Intuitive navigation: Enables quick navigation through logs and metrics, allowing teams to identify and resolve issues swiftly, reducing system downtime.
- Reduced time to value (TTV): Offers pre-configured dashboards tailored for AWS services, reducing the time needed to set up monitoring and analysis.
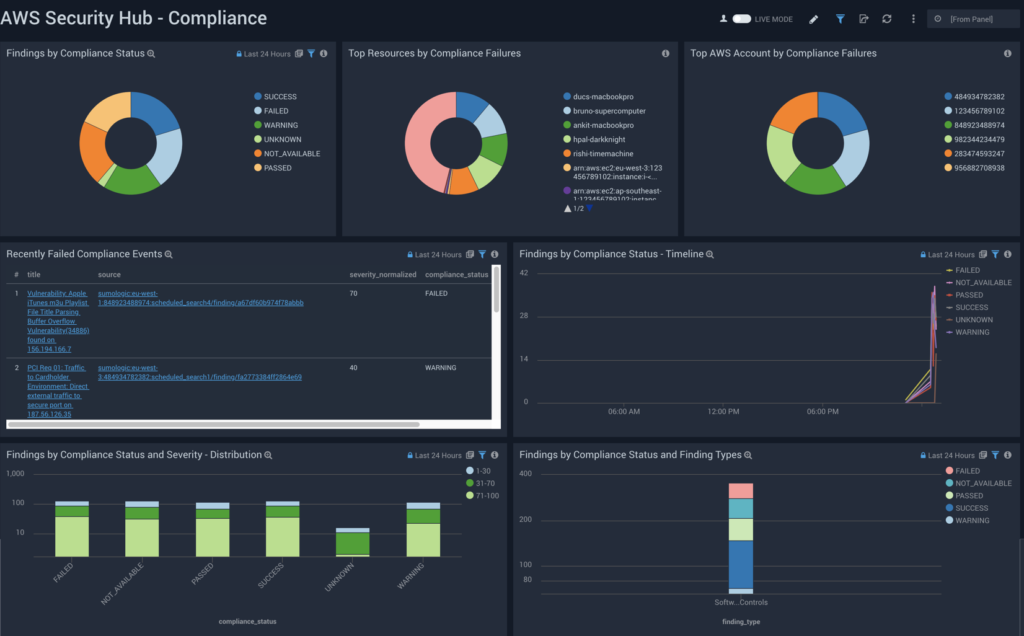
Source: Sumo Logic
Logz.io

Logz.io AI-Powered ELK-as-a-Service is a cloud-native observability platform that provides unified monitoring, troubleshooting, and security for distributed cloud environments. By using log analytics, Logz.io helps engineers detect and resolve incidents more efficiently while simplifying cloud security operations.
Features:
- Machine learning-based automatic threat detection and aid resolution: Uses machine learning algorithms to automatically detect threats and assist in their resolution, enhancing the security posture of the organization.
- Built-in integration with AWS services: The platform seamlessly integrates with various AWS services, ensuring comprehensive monitoring and analysis of AWS environments.
- Real-time alerting of high-priority attacks: Enables prompt responses and minimizes potential damage from security breaches.
- Scheduled, automated reports of detected threats: Users can schedule automated reports that provide insights into detected threats over specific time periods, aiding in compliance and long-term security strategy development.
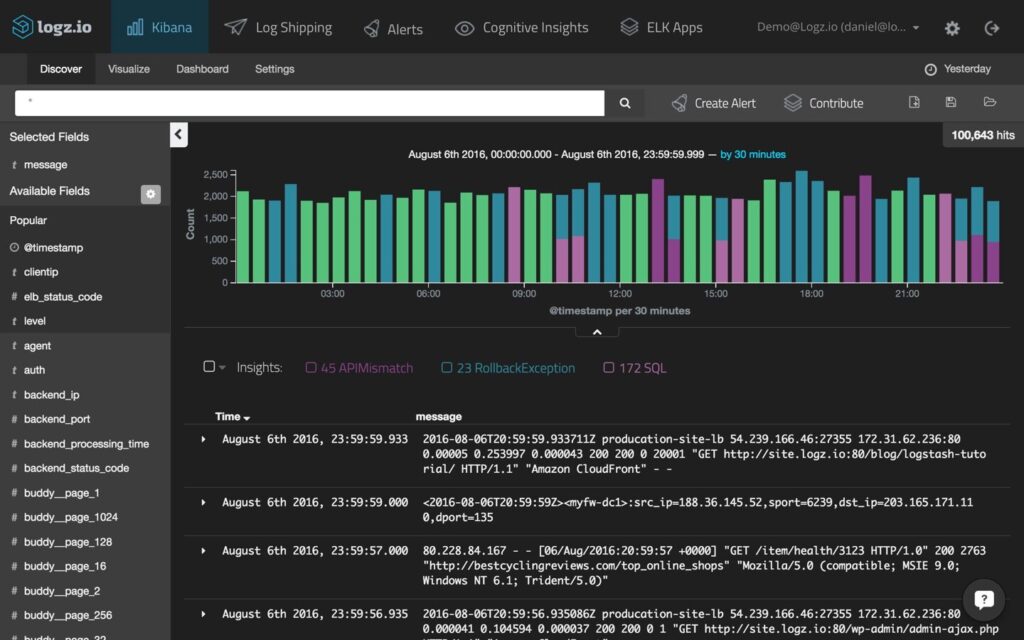
Source: Logz.io
Cribl LogStream
Cribl LogStream aims to optimize observability data collection. It provides a vendor-neutral observability pipeline that allows the collection of data from any source to any destination, transforming, enriching, shaping, and routing the data to suit organizational needs.
Features:
- Flexible data routing: Enables organizations to direct data to the most suitable and cost-effective storage or processing destinations, optimizing resource usage and reducing costs.
- S3 data replay: Allows users to replay data from Amazon S3, helping them analyze historical data and aiding in forensic investigations and long-term trend analysis.
- Reduced data volumes: Helps reduce the volume of log data by filtering and summarizing information, which helps in managing storage costs.
- Cloud migration support: Helps organizations smoothly transition their observability data workflows to the cloud, ensuring data integrity and continuity during the migration process.
- Increased resource utilization: Optimizes data before it reaches analytics platforms, improving the performance of these platforms and enabling better insights and faster processing times.
Source: Cribl
Conclusion
Implementing SIEM in AWS significantly strengthens an organization’s security posture by centralizing and simplifying the monitoring and analysis of security events. This integration uses AWS-native tools to provide real-time threat detection, improve incident response, and ensure compliance. With scalable and flexible solutions, organizations can efficiently manage their security data, reduce costs, and enhance overall operational efficiency.




