Optimized Security Traffic Mirroring Examples – Part 1
You have to capture everything to investigate security issues thoroughly, right? More often than not, data that at one time was labeled irrelevant and thrown away is found to be the missing piece of the puzzle when investigating a malicious attacker or the source of an information leak.
So, you need to capture every network packet. As ideal as this might be, capturing every packet from every workstation and every server in every branch office is usually impractical and too expensive, especially for larger organizations.
In this post, we’ll look at an example of a fictional bookstore company and the recommended mirroring strategies for that specific scenario.
For a list of the most commonly used strategies, check out our traffic mirroring tutorial.
MyBookStore Company
This example represents a simple books store. The frontend servers hold the code for handling customers’ requests for searching and purchasing books, all the system’s data is stored in the database servers. Currently, the throughput to the website is not extremely high but is expected to grow significantly in the upcoming months due to the new year’s sales.
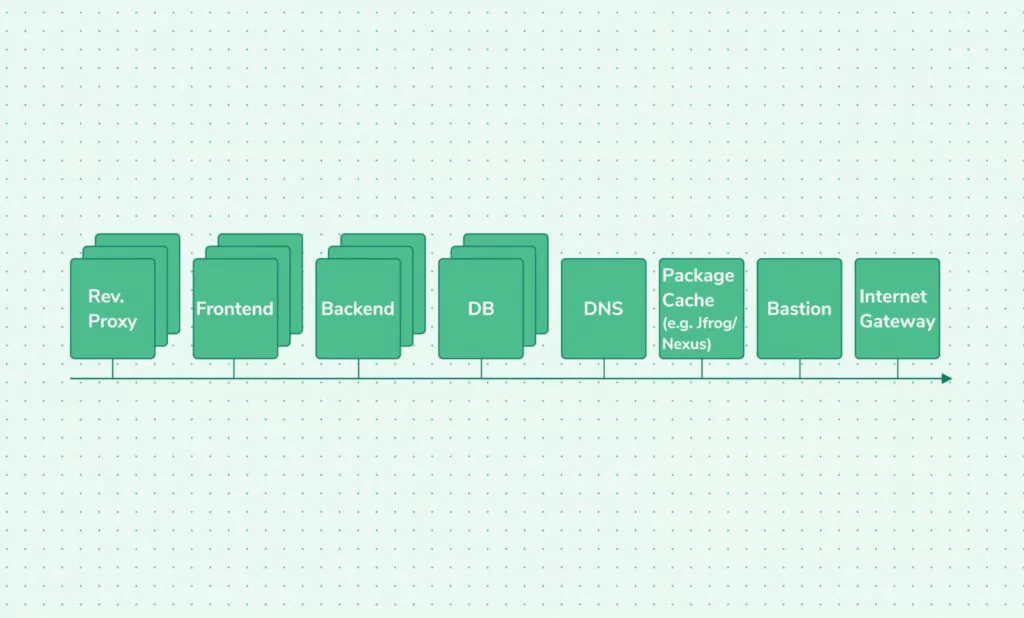
The network diagram above describes a typical network of a SaaS service. It’s a collection of reverse proxies that handle HTTPS encryption and client connections after basic validation, such as URIs paths and sometimes even parameters and HTTP methods. They then send the HTTP requests as HTTP to the frontend servers, making requests to their backend servers that process the data and update or query the DB servers and return the requested result.
Security groups and public IP configuration
The following table represents the network security measures indicated by the allowed connections in and out of each server shown on the diagram.
Rev Proxy
(With public IP)
| From | To | Service | Status |
|---|---|---|---|
| any | any | HTTP/tcp | Allow |
| any | any | HTTPS/tcp | Allow |
| 192.168.1.0/24 | Frontend | HTTP/tcp | Allow |
| 192.168.1.0/24 | any | NTP/udp | Allow |
| Bastion | any | SSH/tcp | Allow |
| 192.168.1.0/24 | DNS | DNS/udp | Allow |
| 192.168.1.0/24 | Packages Cache | HTTP/tcp, HTTPS/tcp | Allow |
Frontend
(No public IP)
| From | To | Service | Status |
|---|---|---|---|
| Rev. Proxy | 192.168.1.0/24 | HTTP/tcp | Allow |
| 192.168.1.0/24 | Backend | Set of custom ports | Allow |
| 192.168.1.0/24 | any | NTP/udp | Allow |
| Bastion | 192.168.1.0/24 | SSH/tcp | Allow |
| 192.168.1.0/24 | DNS | DNS/udp | Allow |
| 192.168.1.0/24 | Packages Cache | HTTP/tcp, HTTPS/tcp | Allow |
Backend
(No public IP)
| From | To | Service | Status |
|---|---|---|---|
| Frontend | 192.168.1.0/24 | Set of custom ports | Allow |
| 192.168.1.0/24 | DB | DB Ports | Allow |
| 192.168.1.0/24 | any | NTP/udp | Allow |
| Bastion | 192.168.1.0/24 | SSH/tcp | Allow |
| 192.168.1.0/24 | DNS | DNS/udp | Allow |
| 192.168.1.0/24 | Packages Cache | HTTP/tcp, HTTPS/tcp | Allow |
DB
(No public IP)
| From | To | Service | Status |
|---|---|---|---|
| Backend | 192.168.1.0/24 | DB ports/tcp | Allow |
| 192.168.1.0/24 | any | NTP/udp | Allow |
| Bastion | 192.168.1.0/24 | SSH/tcp | Allow |
| 192.168.1.0/24 | DNS | DNS/udp | Allow |
| 192.168.1.0/24 | Packages Cache | HTTP/tcp, HTTPS/tcp | Allow |
DNS
(No public IP)
| From | To | Service | Status |
|---|---|---|---|
| 192.168.1.0/24 | DNS | DNS/udp | Allow |
| 192.168.1.0/24 | any | NTP/udp | Allow |
| 192.168.1.0/24 | any | DNS/udp | Allow |
| Bastion | 192.168.1.0/24 | SSH/tcp | Allow |
| 192.168.1.0/24 | Packages Cache | HTTP/tcp, HTTPS/tcp | Allow |
Packages Cache
(No public IP)
| From | To | Service | Status |
|---|---|---|---|
| 192.168.1.0/24 | any | HTTP/tcp, HTTPS/tcp | Allow |
| 192.168.1.0/24 | any | NTP/udp | Allow |
| 192.168.1.0/24 | any | DNS/udp | Allow |
| Bastion | 192.168.1.0/24 | SSH/tcp | Allow |
Bastion
(With public IP)
| From | To | Service | Status |
|---|---|---|---|
| Well defined set of IP addresses | 192.168.1.0/24 | SSH/tcp | Allow |
| 192.168.1.0/24 | any | NTP/udp | Allow |
| 192.168.1.0/24 | DNS | DNS/udp | Allow |
| 192.168.1.0/24 | Packages Cache | HTTP/tcp, HTTPS/tcp | Allow |
In this setup, the only servers that are exposed to the Internet and expected to be reachable by other servers on the Internet are the proxy servers and the bastion server. All other servers do not have a public IP address assigned to them.
All DNS queries are expected to be sent to the local DNS server, resolving them against other DNS servers on the Internet.
Package installations and updates for all the servers on this network are expected to be handled against the local packages caching server. So all other servers will not need to access the Internet at all except for time synchronization against public NTP servers.
SSH connections to the servers are expected to happen only via the bastion server and not directly from the Internet.
In this scenario, we would recommend using the following mirroring configuration by server type.
Reverse Proxies
Since these servers are contacted by users from the Internet over a TLS encrypted connection, most of the traffic to it should be on port 443 (HTTPS) and its value to traffic rate ratio is expected to be quite low, we would recommend the following mirror filter configuration:
Outbound
| Rule number | Description | Rule action | Protocol | Source port range | Destination port range | Source CIDR block | Destination CIDR block |
| 100 | Monitor everything * | accept | All protocols | – | – | 0.0.0.0/0 | 0.0.0.0/0 |
* Note – Although this rule will also mirror the server’s encrypted responses to the HTTPS requests we do recommend that you mirror it since it might also contain HTTPS connections initiated by malware running on the proxy servers to command and control servers and especially since the traffic volume of the server’s responses is not expected to be extremely high.
Inbound
| Rule number | Description | Rule action | Protocol | Source port range | Destination port range | Source CIDR block | Destination CIDR block |
| 100 | Exclude incoming HTTPS | reject | TCP | – | 443 | 0.0.0.0 | <your servers subnet> |
| 200 | Monitor everything else | accept | All protocols | – | – | 0.0.0.0/0 | 0.0.0.0/0 |
Frontend servers
Since the frontend servers receive the unencrypted traffic they are essentially the first place on the network in which we can detect attacks against the system and therefore their traffic data is very valuable from an information security perspective.
This is why we believe that you would mirror any traffic from and to these servers. This will, of course, include the valid traffic by the customers. Although this can be extremely valuable for creating a good baseline that can later be used to detect anomalies, it can also be rather expensive for the organization.
For such cases we would recommend the following mirroring configuration for detecting abnormal behavior of the frontend servers that can indicate a cyberattack that is currently in progress:
Outbound
| Rule number | Description | Rule action | Protocol | Source port range | Destination port range | Source CIDR block | Destination CIDR block |
| 100 | Monitor everything * | accept | All protocols | – | – | 0.0.0.0/0 | 0.0.0.0/0 |
* Note – Although this rule will also mirror the server’s responses to the HTTPS requests, we do recommend that you mirror it since it might also contain HTTPS connections initiated by malware running on the proxy servers to command and control servers. Also, this might include unintended responses that will indicate that an attack (such as XSS or SQL Injection) took place.
Inbound
| Rule number | Description | Rule action | Protocol | Source port range | Destination port range | Source CIDR block | Destination CIDR block |
| 100 | Exclude incoming HTTPS | reject | TCP | – | 80 | 0.0.0.0/0 | <your servers subnet> |
| 200 | Monitor everything else | accept | All protocols | – | – | 0.0.0.0/0 | 0.0.0.0/0 |
Backend servers
Since the frontend servers are contacting these servers with requests that are supposed to be valid after the checks done by the proxy and frontend servers, the traffic volume is expected to be significantly lower than traffic volume to the proxy and frontend servers.
Also, since this is the last chance to detect malicious traffic before it reaches the database, we believe that all traffic from these servers should be mirrored. However, if this is still too expensive for your organization, we would recommend that you use the following mirroring configuration to at least be able to tell if a backend server is behaving abnormally, which may indicate that it has already been breached:
Outbound
| Rule number | Description | Rule action | Protocol | Source port range | Destination port range | Source CIDR block | Destination CIDR block |
| 100 | Monitor everything * | accept | All protocols | – | – | 0.0.0.0/0 | 0.0.0.0/0 |
* Note – Although this rule will also mirror the server’s responses to frontend requests we do recommend that you mirror it since it might also contain HTTPS connections initiated by malware running on the proxy servers to command and control servers. Also, this might include unintended responses that will indicate that an attack (such as XSS or SQL Injection) took place.
Inbound
| Rule number | Description | Rule action | Protocol | Source port range | Destination port range | Source CIDR block | Destination CIDR block |
| 100 | Exclude incoming HTTPS | reject | TCP | – | Set of custom ports | <your servers subnet> | <your servers subnet> |
| 200 | Monitor everything else | accept | All protocols | – | – | 0.0.0.0/0 | 0.0.0.0/0 |
Databases
Since this server is at the heart of the customer’s system, we recommend that you would mirror all traffic in and out of this server.
DNS server
Since this server generates a very minimal amount of traffic that is so extremely valuable for detecting so many types of attacks we recommend that you would mirror all traffic in and out of this server.
Package cache server
Since this server is responsible for packages installations on all other servers, the data from and to this server can answer questions like who installed what and when which can be crucial in a forensic investigation and for detecting installation of malicious tools on the server. Also, the traffic volume from and to this server is expected to be quite low. Therefore, we recommend that you would mirror all traffic in and out of this server.
Bastion server
Since this server is serving as the only way to manage all other servers, provided that it is being used to update the code on the various servers, install required packages, etc., the traffic volume should be relatively low and the value of the data it can provide is extremely high and therefore we recommend that you would mirror all traffic in and out of this server.
Summary
Just like in any other field of security, there is no real right or wrong here, it’s more a matter of whether or not it is worth the trade-off in particular cases. There are several strategies that can be taken to minimize the overall cost of the AWS traffic monitoring solution and still get acceptable results.
For a list of the most commonly used strategies, check out our traffic mirroring tutorial.




