Okta Log Insights with Coralogix
This post will show you how Coralogix can provide analytics and insights for your Okta logs, both performance, and security.
Okta is one of the leading Identity provider platforms in the world, offering a variety of cloud services including a Single Sign-On solution to manage and secure company user authentication with 3rd party applications.
Okta Logs
Okta generates system events related to your organization’s authentication activity. The data provides an audit trail that helps you understand platform activity. Each log event object describes a single logged action or “event” performed by a certain actor for a certain target.
You can leverage these events data by using Coralogix alerts and dashboards to instantly diagnose problems, spot potential security threats, and get a real-time notification on any event that you might want to observe. Ultimately, this offers a better monitoring experience and more capabilities from your data with minimum effort.
Okta Dashboards
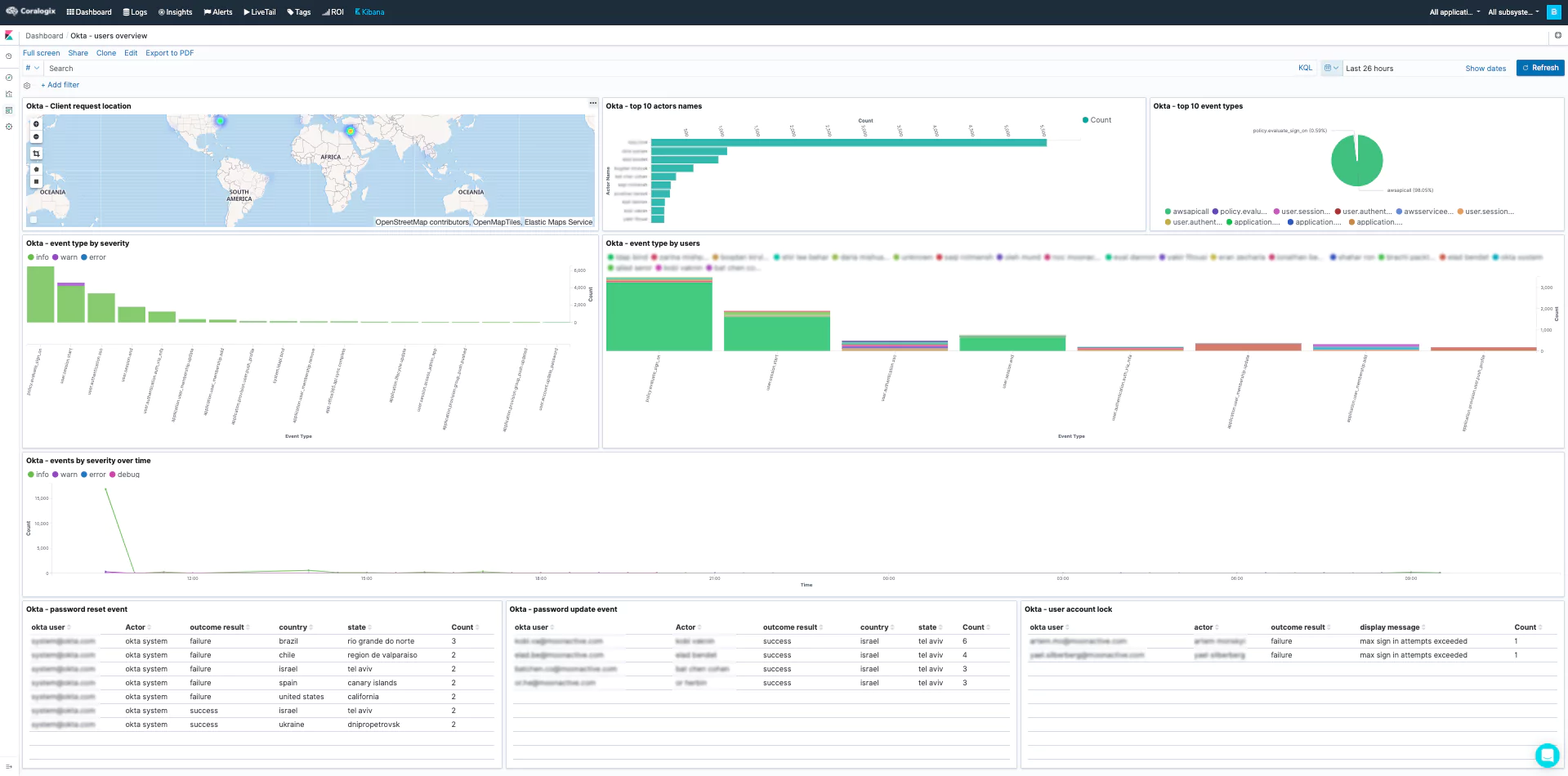
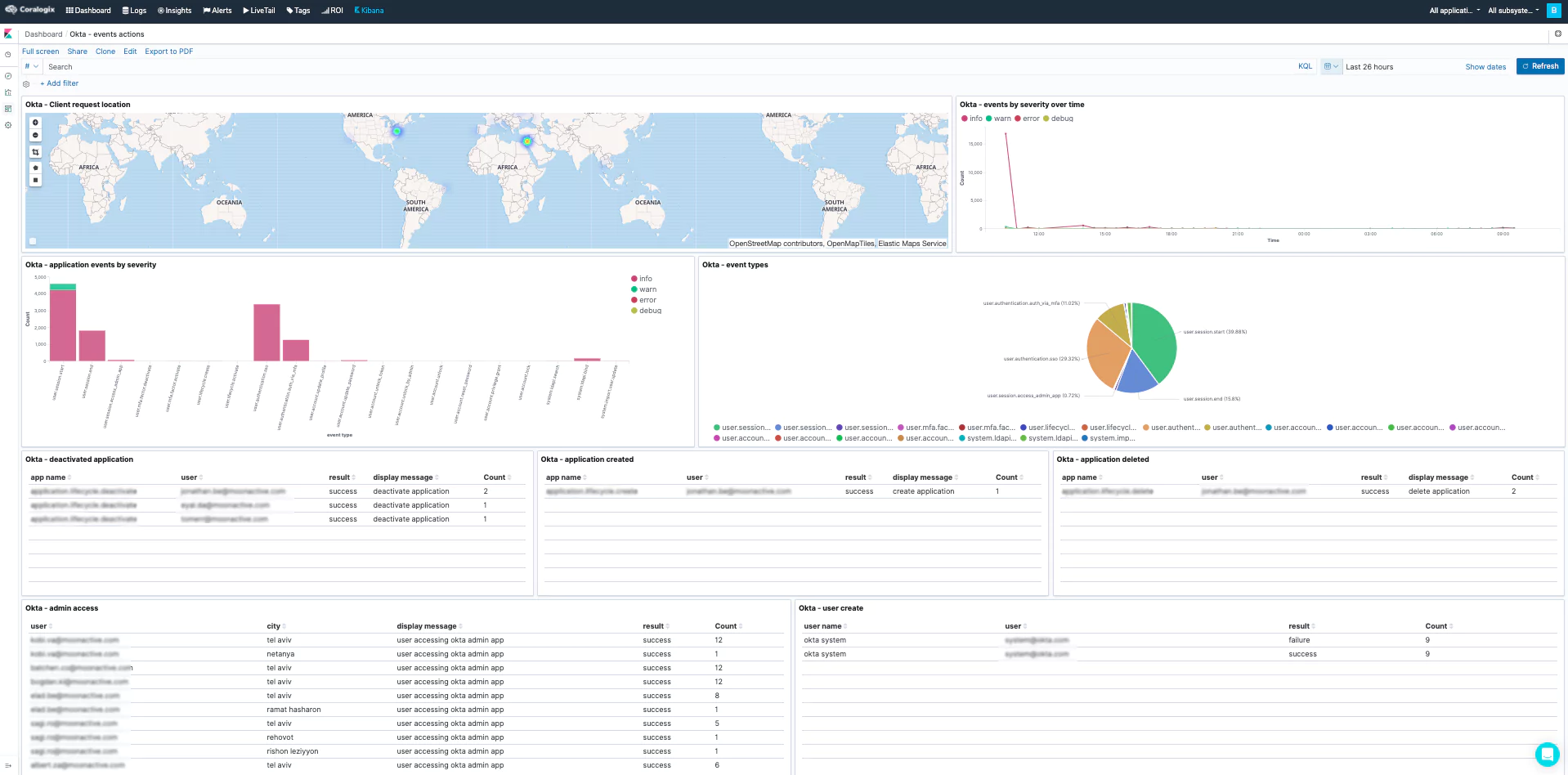
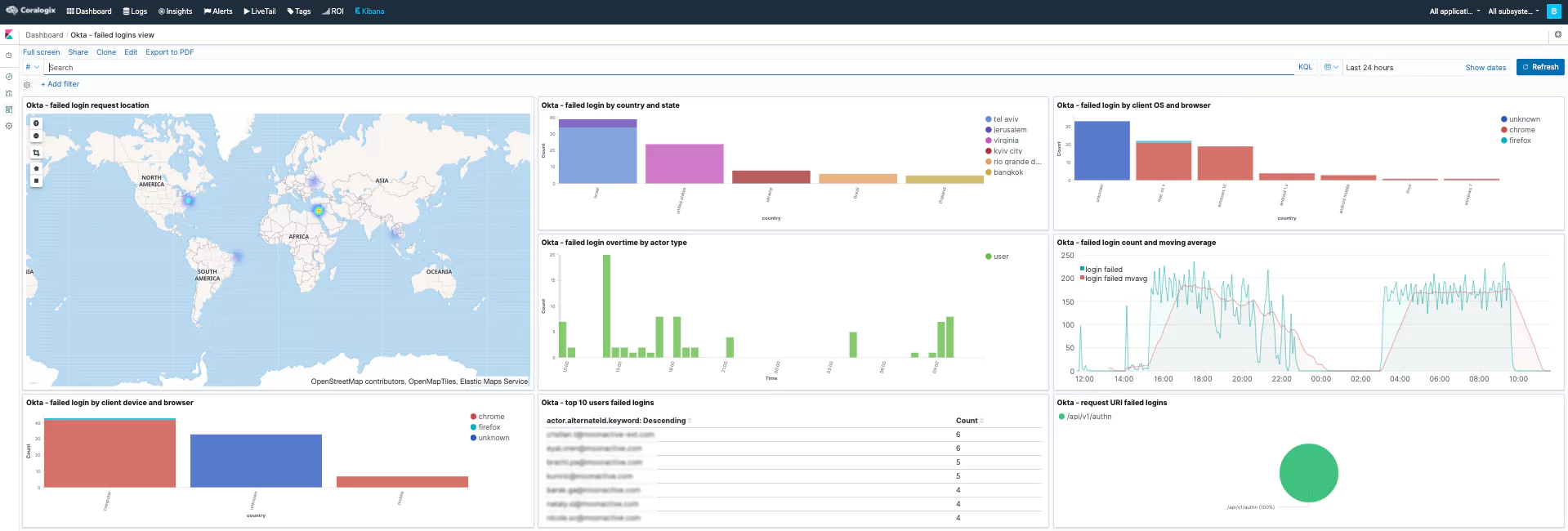
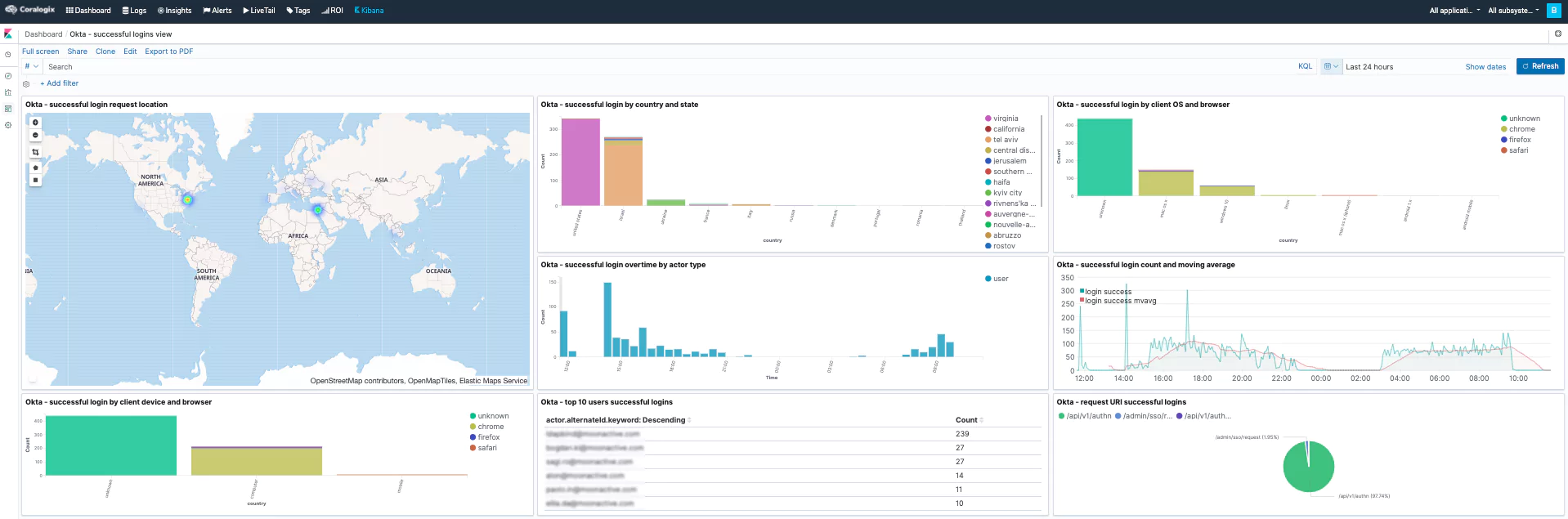
Here are a few examples dashboards we created using the Okta log data. Using fields like displayMessage, eventType, legacyEventType, client.geographicalContext.geolocation, client.geographicalContext.country, actor.displayName, etc..
We were able to create dashboards for:
- User Overview
- Events Actions
- Failed logins view
- Successful logins view
The options are practically limitless and you may create any visualization you can think of as long as your logs contain that data you want to visualize. For more information on using Kibana, please visit our tutorial.
-
User Overview
-
Event Actions
-
Failed Logins
-
Successful Logins
Okta Alerts
Coralogix User-defined alerts enable you to easily create any alert you have in mind, using complex queries and various conditions heuristics, thus being more proactive with your Okta logs with insights you could never gain or anticipate from a traditional log investigation. Here are some examples of alerts we created using traditional Okta logs data.
The alert Condition can be customized to your pleasing and how it fits or satisfies your needs.
| Alert name | Description | Alert Type | Query | Alert condition |
| Okta Policy update | Update access policy. | Standard | legacyEventType: “policy.updated” OR legacyEventType: “policy.rule.updated” NOT “test Infinipoint IdP – with mobile” OR “test Infinipoint IdP – without mobile” NOT “MFA-webauthn-Oktaverify-POC” | Notify Immediately |
| OKTA – Policy Rule Deactivated | Deactivate an access policy | Standard | legacyEventType: “policy.rule.deactivated” | Notify Immediately |
| OKTA – Policy Rule Deactivated | Deactivate a rule in a policy. | Standard | legacyEventType: “policy.rule.deactivated” | Notify Immediately |
| OKTA – Revoke user privilege | Revoke a user privilege from doing something or accessing something | Standard | legacyEventType: “core.user.admin_privilege.revoked” | Notify Immediately |
| OKTA – Policy Deleted | Delete a policy in okta app | Standard | legacyEventType: “policy.deleted” | Notify Immediately |
| OKTA – Admin Privilege Granted | Promote a user to be an admin | Standard | debugContext.debugData.privilegeGranted: “admin” OR debugContext.debugData.privilegeGranted: “administrator” | Notify Immediately |
| Okta – login failure | A user cannot log in to OKTA | Standard | legacyEventType:”login failed” NOT request.ipChain.geographicalContext.city:”ashburn” | More than usual |
| Okta – access admin app event from unknown actor | Login to okta admin app from an unknown source | Standard | eventType:”access admin app” AND NOT actor.alternateId:(root OR admin OR support) | Notify Immediately |
| Okta – unauthorized admin request | an unauthorized login access request to Okta app | Standard | actor.alternateId:(support OR root OR admin) AND NOT client.userAgent.browser:chrome | Notify Immediately |
| Okta – non-browser like tool used to enter an app | Use curl or wget or a utility that is not meant to browse the web. | Standard | client.userAgent.rawUserAgent.keyword:/.{0,19}/ | Notify Immediately |
| administrative access to Okta | Monitor admin access to okta all admin activity with failure. | Standard | eventType: “user.session.access_admin_app” AND legacyEventType:failure | Notify Immediatly |
| Okta – Admin app access | Monitor admin access to okta app | Standard | eventType:”access admin app” | More than Usual |
| Okta – login from an unfamiliar country | Login to okta from a country that you do not have users in. | New Value | legacyEventType:”login success” | · Key to trackBody.countryCode· Notify on new value in the last 48h |
| Abnormal amount of unique User Agents in OKTA | trying to access Okta from too many user agents that have not been seen before. | Unique Count | · Unique Count KeyClient.userAgent.rawUserAgent |
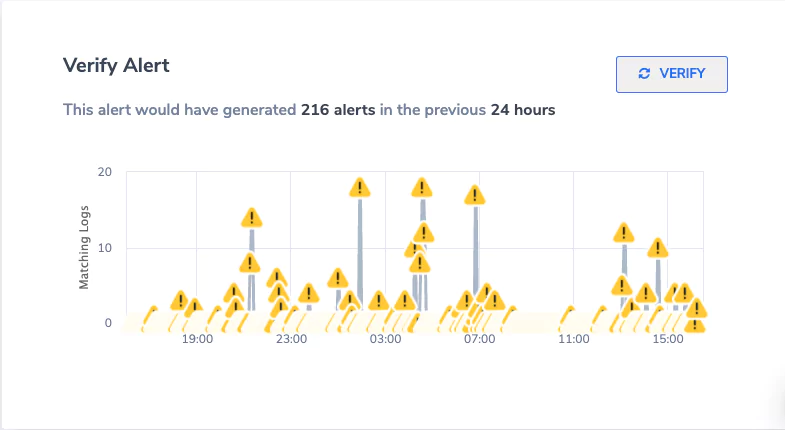
To avoid noise from these Alerts. Coralogix added a utility to allow you to simulate how the alert would behave. At the end of the alert, click verify Alert.
Need More Help with Okta or any other log data? Click on the chat icon on the bottom right corner for quick advice from our logging experts.




