The Definitive Guide to Configuration Management Tools

Today, it’s not possible to manually manage homegrown softwares in large environments anymore. It’s necessary to change to a software-defined approach, which has become known as Infrastructure-as-Code (IaC).
Many of the available configuration management tools, such as Ansible, Terraform, Puppet, Chef, and Saltstack provide automation for infrastructure, cloud, compliance and security management, and integration for deployment and continuous deployment (CI / CD). But what is the best tool to start automating your particular environment?
The difficult task of evaluating Configuration Management Tools prevents DevOps from evolving technically and proposing improvements to the environment they manage. The task can seem daunting when many of the tools perform similarly and there doesn’t seem to be much difference. With this guide, sysadmins who aren’t yet on the automation bandwagon don’t have to remain in the dark any longer.
The main benefits of Configuration Management (CM) in infrastructure are:
- Quickly provision and configure new servers
- Faster recovery from critical events
- Version control and replicating environments for Quality Assurance (QA) or development
According to Stack Overflow Trends and Google Trends, Ansible leads the marathon in the searches for automation tools, followed by Terraform, Chef, and Puppet, as can be seen in the graphs below (Saltstack didn’t appear in the Stack Overflow search):
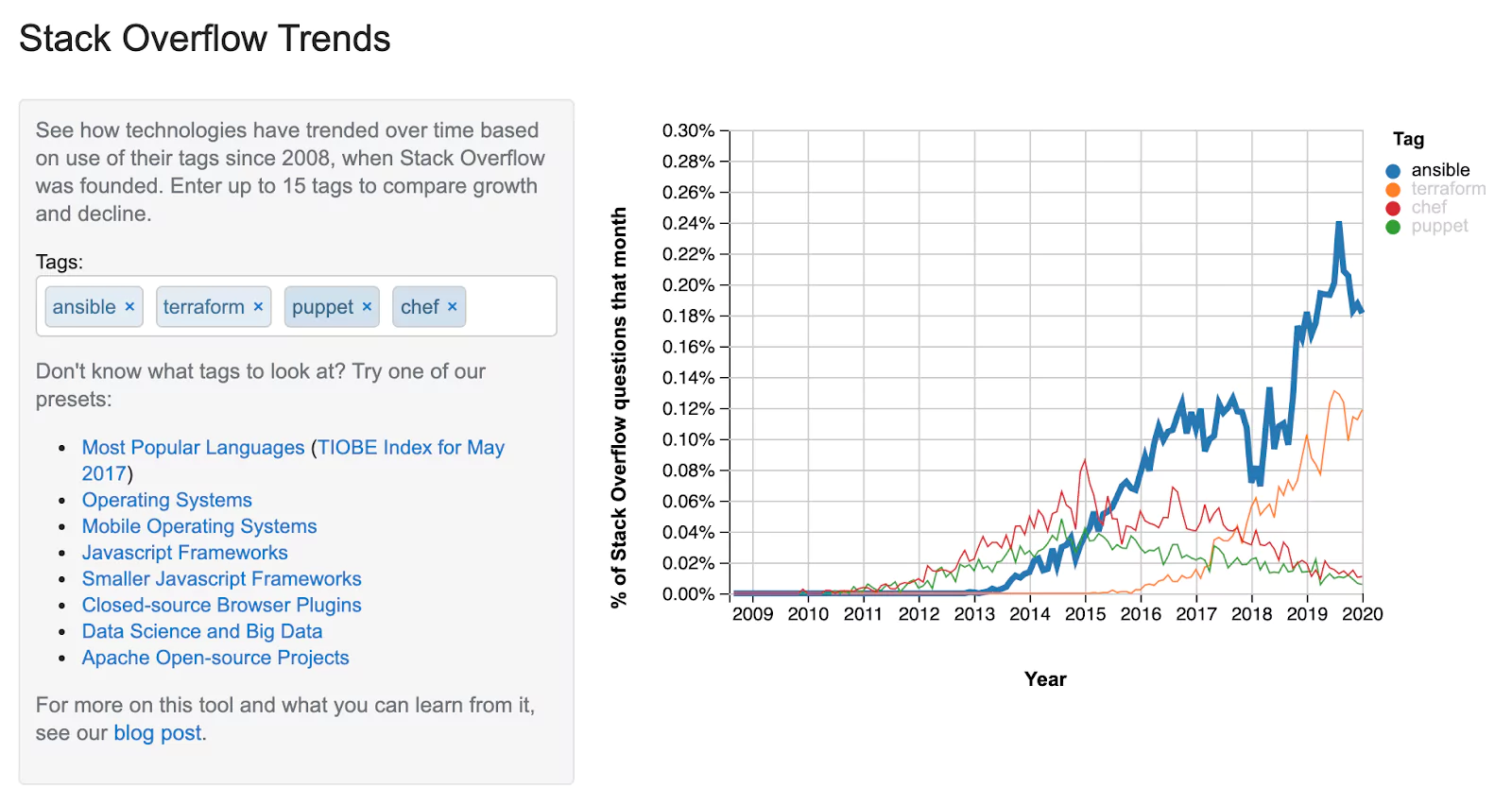
Stack Overflow Trends
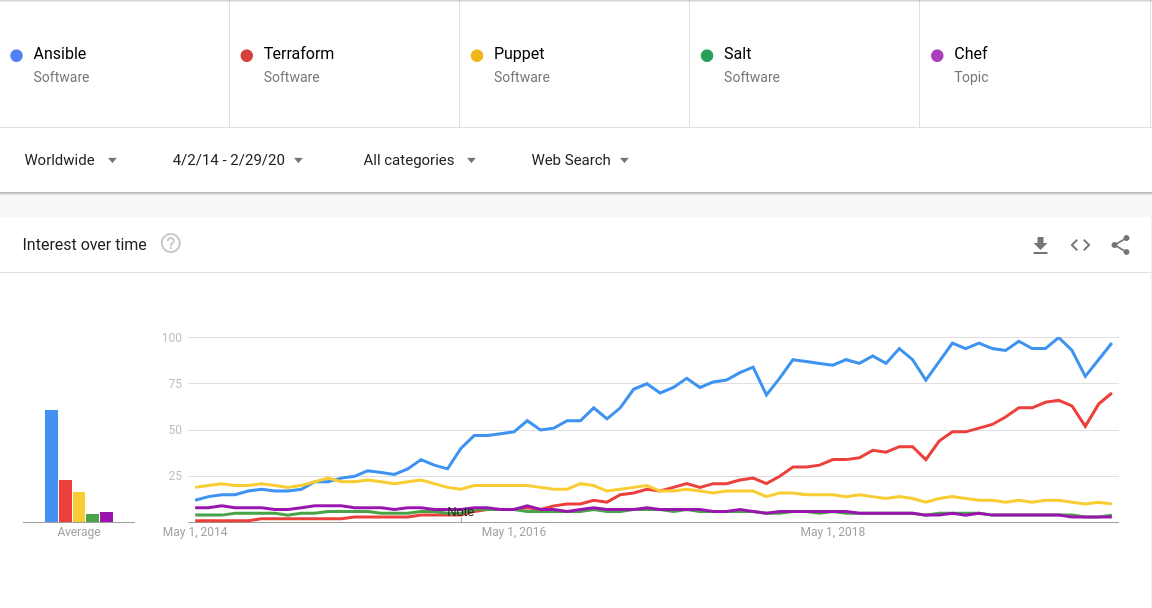
Google Trend for web search
These graphs show that, from the five tools being analyzed, Ansible and Terraform have had the most interest in the last five years. On the other hand, interest in Puppet, Chef, and Salt has decreased.
Ansible vs. Terraform vs. Puppet vs. Chef vs. Saltstack
| Tool |  |  |  |  |  |
| Supported resources | Configuration Management, Orchestration and Provisioning | Provisioning | Configuration Management | Configuration Management, Orchestration | Configuration Management, Vulnerability Compliance, |
| Desired State | Idempotency | Convergence | Convergence | Convergence | Idempotency |
| Infrastructure | Mutable | Immutable | Mutable | Mutable | Mutable |
| Syntax | Declarative | Declarative | Declarative | Declarative / Imperative | Declarative / Imperative |
| Approach control | Serveless and Agentless | Serveless and Agentless | Server and Agent | Server and Agent | Server and Minion (Agent) |
| Configuration Language | ✓✓✓✓ | ✓✓✓✓ | ✓✓✓ | ✓✓✓ | ✓✓✓✓ |
| Community and Cost Support | ✓✓✓✓ | ✓✓✓✓ | ✓✓✓✓ | ✓✓✓✓ | ✓✓✓ |
| Maturity and Learning Curve | ✓✓✓✓ | ✓✓✓✓ | ✓✓✓✓ | ✓✓✓✓ | ✓✓✓ |
| Can it be used with other tools? | ✓✓✓✓ | ✓✓✓✓ | ✓✓✓✓ | ✓✓✓ | ✓✓✓✓ |
| Best for | The best tool for those beginning with Infrastructure-as-code managing heterogeneous environments. | To simplify the management of environments in the public and private clouds, multi-cloud and hybrid clouds. | To orchestrate environments that have rigid compliance requirements, maintaining an immutable configuration. | Continuous Automation on complex topologies or deployments that need speed. | To orchestrate and to automate IT tasks with speed and flexibility. |
| RATING SCORE | 4.83 | 4.50 | 4.17 | 3.67 | 3.67 |
Fundamentals
Before diving into the configuration tools themselves, let’s explore some fundamental concepts. Feel free to skip the tool reviews below if you’re already familiar.
Configuration Management Tools: Orchestration and Provisioning
Traditional software configuration management (SCM) tools are used to track changes made during the lifetime of an application. Among the benefits of using SCM are; keeping track of configuration items, establishing baselines, controlling changes and auditing.
Configuration Management Features:
- Enforcement: ensure that the resources are in the desired state
- Enabling cooperation: team members are able to cooperate
- Version control: baseline with tracking all versions of code
- Enable change control process: every change made over time and
- Abstraction: e.g. different Linux flavors with the same software version and configuration
Idempotency or Convergence
The concept of convergence and idempotency is a little confusing and leads to some mistakes. Convergence typically means if a process is run 4 or 5 times, only the necessary changes are made so that the resource being managed converges to the desired state defined in the configuration files. Idempotency is the characteristic of verifying the current state of what will be modified. If it is already in the desired state, no action is taken.
Mutable or Immutable Infrastructure
The concept for mutable and immutable infrastructure is whether or not an environment can change after its creation. While a mutable environment allows changes to be made during its lifecycle, like fixing configuration errors and updating the resources that are already provisioned, in an immutable environment, that would not be possible. The resource is destroyed and created again with a new version.
Procedural or Declarative Approach
The configuration management tools work with different methodologies to define configuration in code namely procedural or declarative syntax. While the first describes all steps necessary to reach a specific state in sequence, the second one simply defines a state that a resource should be. How that state is reached is left to the engine of the automation tool.
A procedural syntax is best exemplified as a common shell script. For instance, if a systems administrator uses a shell script to customize the access.conf file of a server to include a set of lines authorizing access to that server, they will have to define a number of instructions. The instructions are to check if the file exists, to load its contents to memory, check if any of the lines already exist, insert those who aren’t in the file and finally, save the new content on disk.
The Terraform tool, for example, uses the declarative approach: An infrastructure object is defined as a resource. The particular configurations of this object are defined as parameters in the resource definition. The administrator does not declare how a particular state will be reached, that will be done by the Terraform Engine. If a number of servers are defined, Terraform will create or destroy the instances until the defined number of infrastructure objects are present.
Master Server and Agents
One of the things a sysadmin must evaluate when choosing tools is trade-off between benefits and the complexity a tool will add to the environment being managed.
Managing master servers and client agents can be a daunting task, especially in big environments . A main challenge being how to provision the agents for the first time and how to keep them up to date.
On the other hand, an agentless solution has some limitations and it needs some extra work to maintain the resources’ compliance. All of this has to be taken into account and placed on a scale when deciding.
Ansible

Brief Summary
Ansible is described as “a radically simple IT automation platform that makes your applications and systems easier to deploy. Avoid writing scripts or custom code to deploy and update your applications — automate in a language that approaches plain English, using SSH, with no agents to install on remote systems.[1]“
What can I do using Ansible?
It’s no accident that Ansible is the most popular choice of automation tools. It’s very flexible and can be considered an “all-in-one” tool. All automation steps can be done with Ansible, from Orchestration, Configuration Management, Application Deployment, Provisioning, Continuous Deployment & Delivery (CI/CD) to Security & Compliance.
This is due to the fact that Ansible was developed in Python, and in addition to inheriting the general-purpose language feature, you can make use of thousands of existing packages from the Python community to create your own modules.
Supported resources:
- Configuration Management and Security & Compliance: Code, life-cycle management, and changes can be made through inventories, playbooks, and roles in Ansible. It is possible to manage desired states and idempotency natively in the tasks that will be performed.
- Orchestration and CI/CD: Ansible is a simplified and powerful orchestration engine. It integrates with almost every area of the infrastructure, from provisioning virtual machines (VMs) to creating rules on a firewall. It also focuses on areas where other tools leave gaps such as zero stop and continuous updates for multi-tier applications across the infrastructure.
- Provisioning: Ansible has modules for containers, virtualization, cloud vendors, and can easily integrate with other tasks from previous steps.
On Devices and Resources:
Ansible does not require agents installed on the endpoints. So, it supports equipment such as Firewalls, Load balancers, Containers, enterprise storage appliances, other network devices, etc .
Technologies you can use:
Ansible, currently in version 2.9, has more than 3300 modules in several areas of IT infrastructure:
- Cloud: AWS, Azure, Digital Ocean, Google, OpenStack, Rackspace, and others
- Operating Systems: RHEL, Linux Flavors, MS Windows, and others
- Virtual & Containers: Docker, VMware, RHV, OpenStack, Openshift and others
- Storages: Netapp, Red Hat Storage, Infinidat, and others.
- Windows: NTFS permissions with ACLs, handle files, install and update packages, manage IIS, alter registry keys, manage Windows File Server, Services, Local and Domain user management, and others.
- Network: A10, Arista, Aruba, Cumulus, Bigswitch, CISCO, Dell, Extreme, F5, Lenovo, MikroTik, Juniper, OpenSwitch and others
- Security: Checkpoint, Cisco, Cyberark, F5, Fortinet, Juniper, IBM, Palo Alto, Snort and others
- Monitoring: LogicMonitor, New Relic, Sensu, Coralogix, and others
- DevOps: Jira, GitHub, Vagrant, Jenkins, Slack, and others
How Does Ansible Work?
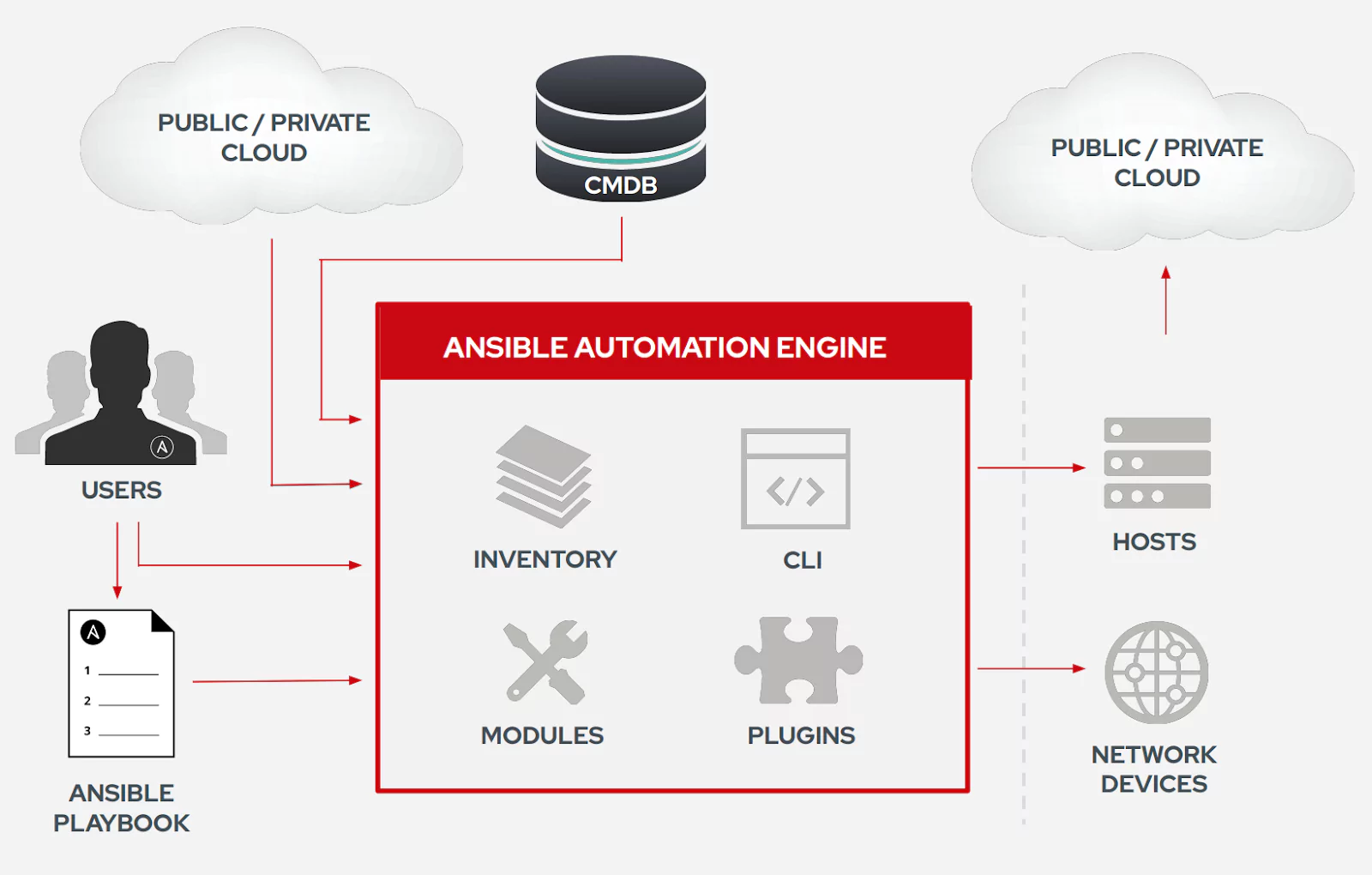
Source: Deck Ansible Workshop
- Playbook: Written in YAML, playbooks are a set of one or more tasks that are executed in sequence. Tasks execute an Ansible module. In cases where the resource being managed does not have Python installed or no API is available, shell commands can be executed through the raw module. The “playbook” name is an analogy to a Rugby game, where the list of plays that you execute during a match is called a playbook.
- Module: Can be written in Python, PowerShell (for Windows resources), and any language that is able to generate a JSON formatted output.[2] They are the core of the Ansible stack. They can be part of the main Ansible code base or external.
- Inventory: List of the resources in your infrastructure that will be managed with Ansible. Ansible allows static inventory files or dynamic inventories, through the use of scripts and inventory plugins. Dynamic inventories are generated at execution time from sources like a Configuration Management Database (CMDB), Satellite (or Foreman) managed hosts, and VMware vCenter virtual machines and hosts.
- AD-HOC: The execution of ad-hoc commands (through the ansible cli command) is a feature for remotely executing simple tasks (using modules) without having a playbook.
- Plugins: “Plugins are pieces of code that augment Ansible’s core functionality. Ansible uses a plugin architecture to enable a rich, flexible and expandable feature set”[3] like mail, Slack notifications, enhancing inventories, and sending events to Foreman, Grafana, Logstash or Jabber.
Other Resources
- Ansible Galaxy: A hub for searching and sharing Ansible content from the community in various formats like Roles and Playbooks Bundle (APB).
- Ansible Tower (AWX community version): A web interface to orchestrate projects at scale.
Community and Support
The Ansible community is very active, they have meet-up groups across the globe, IRC Channels, and Mailing Lists. Like other Red Hat maintained products, Ansible’s code is open source and receives direct contributions from the community.
Support plans are available for Ansible Engine, Ansible Tower, and Ansible Content Collection. The price varies from US$5000 to US$14000. The licensing is done in 100 server groups and it is billed annually.
Maturity and Learning Curve
Ansible has a very short learning curve, with easy installation and initial configuration. In less than 30 minutes, it is possible to install, configure and execute ad-hoc commands for ’n’ servers to solve a specific problem, such as daylight saving time adjustments, time synchronization, root password change, updating servers, restarting services, etc.
Syntax and workflow are simple to understand, making it easy to learn for new users. The files use YAML (YAML Ain’t Markup Language), a user-friendly declarative language standard that is widely used by other tools and easy to understand, with the addition of using the Python language to extend the functionality of Ansible with customized modules.
Can it be used with other configuration management tools?
Even though Ansible is like a swiss army knife, it can also be used with other tools. Due to its flexibility and simplicity, Ansible can be combined with Terraform for maintaining immutable environments or with Puppet for persistent configuration in servers.
Ideal Use Case
Due to the great (and increasing) number of supported resources and its ease of use, Ansible is a great choice for those starting with configuration management tools and infrastructure-as-code.
The tool is ideal when automating tasks that do not depend on maintaining state. So first installations of software, correcting configuration files across several instances, backing up switches configuration, and similar activities are easily automated with Ansible.
In heterogeneous environments, Ansible is an excellent choice because it allows all these resources to be managed with a single tool. Being able to manage Windows and Linux boxes or provisioning resources in more than one cloud provider and on-premises with the same tool saves a lot of time for the Ops teams.
Even the management of different Linux distributions can be simplified with little adaptations on playbooks. It is necessary to note that the support for Linux and Unix-like systems is greater than the support for Windows in Ansible. However, Ansible can be used to orchestrate PowerShell scripts and Desired State Configuration (DSC) resources if a specific Windows Module was not yet developed.
Read this tutorial to get started with Ansible quickly
Terraform
Brief Summary
Terraform is an open-source infrastructure-as-code software tool written in the Go Language. As described in their first blog post, “it focused on providing a way to describe the complete Infrastructure as Code from physical servers to containers to SaaS products, Terraform is able to create and compose all the components necessary to run any service or application. With Terraform, you describe your complete infrastructure as code, even as it spans multiple service providers. Your servers may come from AWS, your DNS may come from Cloudflare and your database may come from Heroku”[4]
What can I do using Terraform?
As described above, Terraform has come to cover the growth of cloud platforms. A gap began to increase when the paradigm of infrastructure changed from the on-premises solutions to the cloud platform services. A tool was needed to facilitate handling all the solutions for several cloud providers at the same time without having to implement different APIs and develop scripts to orchestrate all the different components.
Terraform makes it possible to change from one platform to another painlessly, including in-house solutions mixed with multi-cloud platforms (e.g.: IaaS or SaaS services), all in a transparent way. “It is a tool for building, changing, and managing infrastructure in a safe, repeatable way.”[5]
Concrete use cases of Terraform are Multi-Tier Applications, Self-Service Clusters, Software Demos, Disposable Environments, Software Defined Networking (SDN), Resource Schedulers, and Multi-Cloud Deployment.
The resources and features available[6]:
- Infrastructure-as-Code (IaC): It allows handling the datacenter as code that can be shared and reused.
- Execution Plans: One of the stages of a run, shows the changes that will be made and the impacts on the existing infrastructure when apply is called.
- Resource Graph: Shows a graph of the plan with all the resources that will be created and modified, parallelizing the tasks of non-dependent resources.
- Change Automation: Knowledge of the exact changes and in what order they will be done with minimal human interaction, avoiding possible human errors.
On Devices and Resources:
Terraform does not require agents installed on the endpoints. The tool’s concept is to understand any service that exposes an API interaction in order to make resources available, managing low-level components such as computer instances (physical and VMs), storages, and networking (switches) as well as high-level components such as containers, DNS entries, SaaS services, etc11.
Technologies you can use:
Terraform, currently in version 0.12, has more than 300 providers in several areas of cloud computing like IaaS, SaaS and PaaS services.
- Major Cloud Providers: Google, AWS, Azure, Alibaba, VMware Cloud, Oracle Cloud, and others.
- Others Cloud Providers: Heroku, BaiduCloud, DigitalOcean, Openstack, Cisco ACI, and others.
- Infrastructure Software: Docker, Kubernetes, Rancher, Chef, Consul, and others.
- Network: A10 Networking, F5 BIG-IP, Check Point, Palo Alto, Cisco ASA, and others.
- VSC: Gitlab, Github, Bitbucket
- Monitoring & System Management: Grafana, New Relic, Coralogix, OpsGenie, and others.
- Databases: Mongo, MySQL, Postgres, and others.
- Misc. and Community: Openshift, Foreman, AWX, Google G Suite, Active Directory, Elasticsearch, NetApp, Proxmox, and others.
How Does Terraform Work?
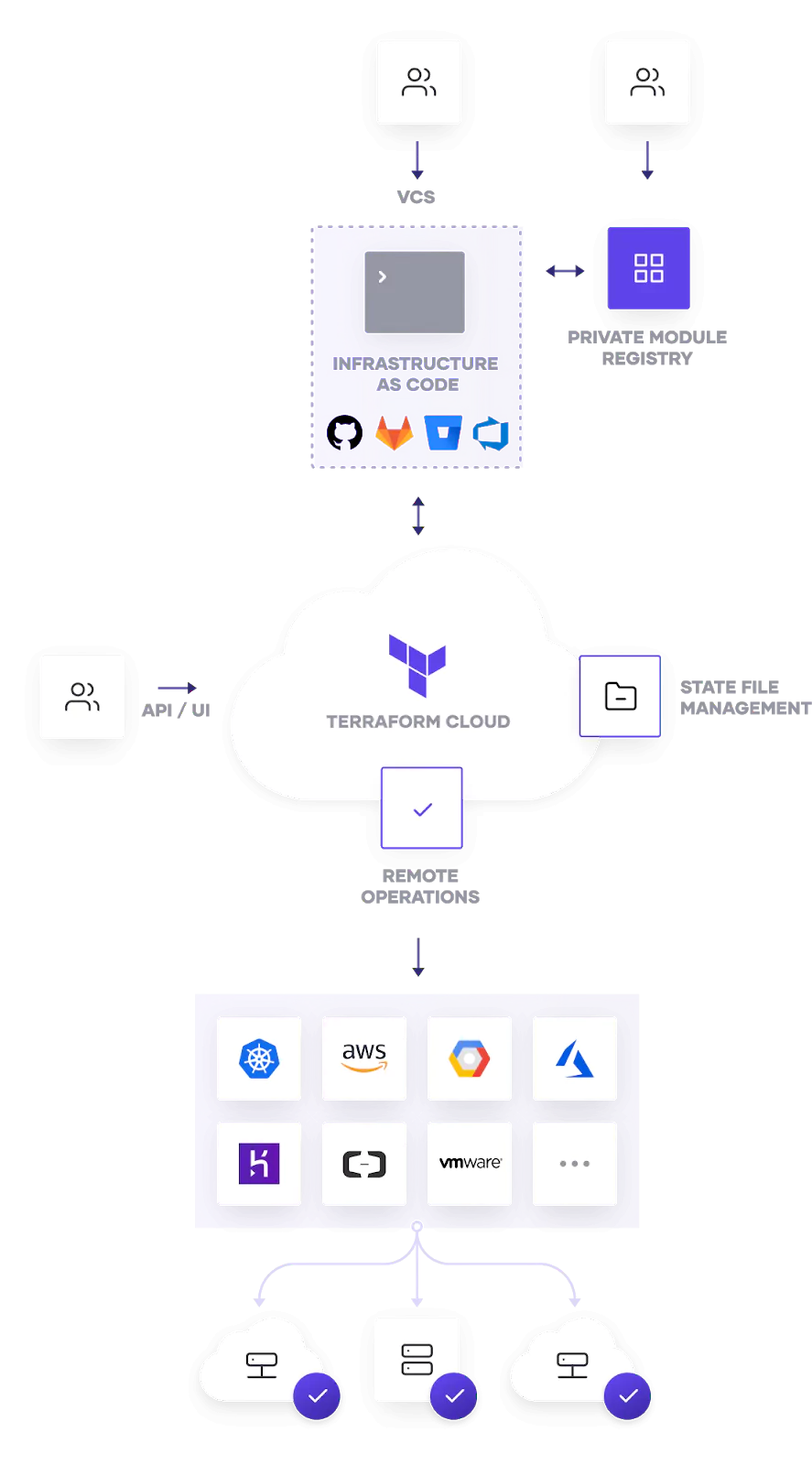
Source: Open Source and Cloud
- Resources: The most important part of Terraform. The resources are divided into blocks and each block describes one or more infrastructure objects (E.g. virtual networks, compute instances, or higher-level components)
- Providers: The behavior of resources is defined by Providers (SaaS or IaaS services). Each provider offers a set of named resource types and defines for each resource type which arguments it accepts. It’s compared with Ansible Modules.
- Modules: Module is a container with multiple resources. They can be compared with Ansible Roles. Terraform Register is an online resource to share and download modules.
- Provisioners: If the Modules do not provide a task automating a specific resource or if certain behaviors can’t be directly represented in Terraform’s declarative model, Provisioners can be used to model specific actions on the local machine or on a remote machine in order to prepare servers or other infrastructure objects.
- Templates: Piece of code written in a special language named HashiCorp Configuration Language (HCL).
Other Resources
- Terraform Cloud: Terraform Cloud provides a central interface for running Terraform within a large collaborative organization.
- Terraform Enterprise: Terraform Enterprise is the self-hosted distribution of Terraform Cloud.
- Terraform Register: It’s a repository of modules written by the Terraform community.
Community and Support
Terraform is an open-source tool and its code is hosted on Github. Anyone can contribute to the development and help to extend its features, fixing bugs and document new use cases. The community is growing and people are willing to help the project through various sources like forums, bug trackers and community portals.
Hashicorp offers the support plan for Terraform Cloud and Terraform Enterprise described above. This includes a central interface for running Terraform, access and privilege control, remote state file storage, notifications and built-in integration with Version Control System (VCS).
Terraform Cloud is free for up to 5 Users, and “for Terraform teams that do want enterprise governance features, Terraform Cloud for Teams comes with role-based access control for private module registries and support for unlimited collaborators in a version priced at $20 per user per month. For $70 per user per month, Terraform Cloud for Teams also includes Sentinel policy as code and advanced policy and permissions features that can be customized among multiple regions and time zones and enforced as mandatory or suggestions. The $70 per month version also includes a new cloud infrastructure cost estimation feature that alerts users about the projected costs of infrastructure they are about to provision with Terraform.” [7]
Maturity and Learning Curve
The drawback of the Terraform is the State. Terraform uses the command plan for storing the state in a local file named terraform.tfstate. When you work with a team, you must use the remote state, a kind of remote storage for storing state files, which is shared with all members of a team.
There’s a modest learning curve and the documentation helps those that are getting started. The organization of the documentation is well structured, visually clean and very well written. A learning platform is available with several Getting Started tutorials, mini online training courses, which are totally free. The learning platform also includes a review guide for Product Certification Exam Prep.
Can it be used with other configuration management tools?
Yes. Terraform is not incompatible with other tools. Provisioners can be used to model specific actions on the local machine or on a remote machine in order to prepare servers or other infrastructure objects for service using the provisioners. There are Provisioners for Chef, Puppet and Salt. Provisioners are a last resort and must use it in “certain behaviors that can’t be directly represented in Terraform’s declarative model.”[8]
Ideal Use Case
Terraform is growing due to it simplifying the management of environments in the cloud. Several cloud services appeared over time and what was supposed to be a simple task ended up becoming a complex thing. There are public and private clouds, multi-clouds and hybrid clouds. Terraform arrived with the intent of being the tool to manage resources in varied cloud providers:
- Bootstrapping and initializing resources.
- Provides a flexible abstraction of resources and providers.
- Turn manual customizations into code-defined infrastructure.
Read this tutorial to get started with Terraform quickly
Puppet

Brief Summary
Puppet is a company that began around the name of its main product, despite having other products and services today. Puppet represents the very implementation of the configuration management specification.
The basic architecture of Puppet is a master-client approach, in which a master node controls the desired state of a number of managed nodes through agents.
A Puppet agent “regularly performs Puppet runs, wherein it sends facts to a master and receives a configuration catalog, then applies the catalog to the local system using its providers.” [9]
What can I do using Puppet?
Puppet is an ecosystem of products that provides tools to automate the management of your infrastructure. The community of users and contributors are involved in the Puppet Open Source version. There are also other Puppet enterprise products available with a support plan for increased functionality and performance of the core product.
Available resources and features:
- Continuous Delivery: Integrate with other tools for cloud-native deployments, infrastructure deployment workflow, self-service, and cloud provisioning.
- Continuous Compliance: For critical environments, with regulatory requirements and security standards, use Puppet to ensure your infrastructure is always compliant. It allows auditing with reports that demonstrate compliance.
- Incident Remediation: For quick remediation, removing barriers between DevOps and InfoSec, reducing surface attack area, and integrating with leading vulnerability assessment tools.
- Configuration Management: It’s the flagship of the Puppet solutions. You can quickly harden existing systems, automate your environment to minimize the risk of human error, reduce manual work, make a faster recovery possible by reducing downtime, integrate with existing automation code, and begin to tackle your patch management backlog.
On Devices and Resources
By default, Puppet requires agents installed on the endpoints and managed nodes. Another approach is to use modules backed by an API for providing services that do not permit installed agents. Thus, it supports management configuration of almost all operating systems, Cloud, Virtualization and Containers, Applications, Networking, Databases, and integrates with other Provisioning tools.
Technologies you can use:
Puppet, currently in open source version 6.14, has more than 6443 modules in the Puppet Forge to support several areas of IT infrastructure, such as:
- Cloud: AWS, Azure, Cloud, OpenStack, and others.
- Operating Systems: RedHat, Debian, Ubuntu, OS X, Solaris, SLES, Solaris, AIX, FreeBSD, OpenBSD, NetBSD, and others.
- Virt & Containers: Docker, Kubernetes, VMware Vcenter and VSphere, Rancher, and others.
- Application: IBM Websphere, IIS, Apache, HA Proxy, Tomcat, and others.
- Networking: Palo Alto, Cisco, F5 Big-IP, and others.
- Databases: Postgres, MySQL, MS SQL Server, and others.
- Provisioning tools: Terraform, Satellite, and others.
How Does Puppet Work?
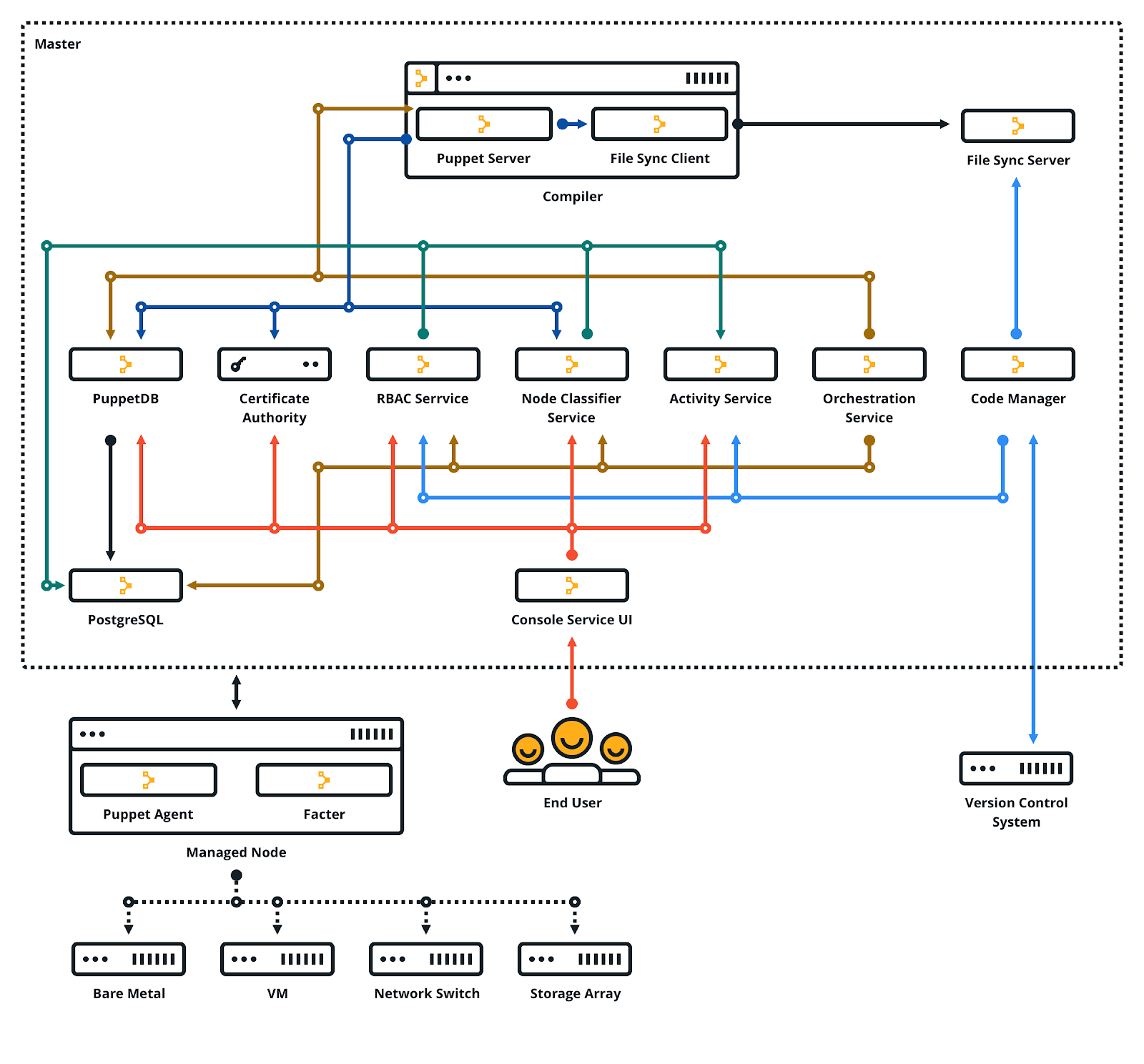
Source: Open Source and Cloud
- Puppet Server: The Puppet Server performs the role of the master node. It runs on the Java Virtual Machine (JVM) as an application using the Trapperkeeper service framework. It’s written in Ruby and Clojure, providing the services for the classic Puppet master application.
- Hiera: Hiera is used to separate data from Puppet code. Puppet uses Hiera to store the configuration data in key-value pairs and to recover data a particular module needs for each node during the catalog compilation.
- Facter: Facter has the feature to collect facts of the nodes. These facts will be used in your Puppet manifest as variables for cross-platform systems.
- Manifest: Files to describe the desired state of your system using a custom non-standard Declarative Domain Specific Language (DSL) with restrictive rules. These manifest files saved with .pp extension are compiled and applied across your infrastructure.
- Resources: It describes the configuration of elements of a node, in DSL, to be managed over time, such as user, package, service, interface, exec, or a registry key, without needing all steps to achieve a final desired state.
- Classes: It’s a grouping of the resources, which are organized in Modules and are only executed when they are invoked.
Other Resources

Puppet Enterprise: It’s a web User Interface (UI) for configuring and deploying applications for your servers, with a unified view of all your nodes, the status run, jobs, events and the last reports.
Puppet Remediate: Remediate is a tool for vulnerability management, find and fixing vulnerabilities for Infosec and IT Ops teams.
Project Nebula (Beta): Nebula is used for the continuous deployment of multiple cloud-native applications and infrastructure in the repeatable workflows simplest way.
Bolt: A tool for automating basic infrastructure manual tasks using Ad-hoc commands and task plans for remote nodes without the needs of agents. It’s very similar to Ansible’s approach, including the inventory, but with a reduced number of actions. It’s useful for installation, upgrade and management of Puppet agents in the nodes or other simple tasks.
Puppet Forge: A repository or collective for pre-built Puppet modules.
Community and Support
The members of the Puppet community are very active. The Puppet Forge has over 6.000 community modules created by a network of users and developers. There are several events such as Puppet Camps, Puppet Champions, and Puppet Test Pilots.
Puppet at its core is open-source software and most users will start off with the Open Source version of Puppet. Puppet Enterprise can be used for free on up to 10 nodes. For the support plans, Puppet Enterprise standard pricing starts at $112 per node/year. Bolt is completely free.
Maturity and Learning Curve
The programming language (DSL) is easy to learn and robust for complex implementation. Puppet was released in 2005 and it has good community support across development tools.
The basic infrastructure for the initial configuration is complex. Installations, configuration, and maintenance of Puppet Master and Agent are not trivial to sysadmins that are entering the DevOps world or finding automation tools. Despite the arrival of the Bolt tool, facilitated for news adepts, the potential of the use of Puppet is in an architecture client-server.
Can it be used with other configuration management tools?
Puppet integrates best with Terraform, using Bolt tasks for executing many Terraform actions like “apply”, “destroy”, “init” and “output”. There are other initiatives from the user communities for any management tools like Ansible, Chef, and SaltStack.
Ideal Use Case
Puppet is recommended for orchestrating environments that have rigid compliance requirements, maintaining an immutable configuration of nodes, with reports and role-based access control.
Read this tutorial to get started with Puppet quickly
Chef

Brief Summary
Don’t read this part hungry. You’ll hear a lot of culinary terms like recipe, cookbook, kitchen, knife, and supermarket, but keep calm, we’re talking about a company called Chef. Chef was created in 2008 around one product called Chef Infra. The company grew by creating good products focused on delivering a fast automation solution for both infrastructure and applications.[10]
In their mission, they describe themselves as a platform “to help the most enduring and transformative companies use Chef to become a fast, efficient, and innovative software-driven organization.”[11]
What can I do using Chef?
Like the other automation tools, Chef embraces several areas in the DevOps (ALDO[12]) software solutions, but with a different premise: Speed and scalability. Chef’s architecture is a client-server approach similar to Puppet, with one difference that each node computes its settings and manages its own needs.
Chef states the quality of their solution is due to the assurance that the “configuration policy is flexible, versionable, testable, and human-readable”[13]. The main resources and features are:
- Configuration automation: Configuration management automation enables configuration at scale. The configurations are continuously evaluated to determine whether the desired state is compliant or not, and corrects the configuration drift.
- Patcher management: To remove the pain from the software patching by automating the validation and configuration of the infrastructure.
- Continuous configuration: Configure your system to continuously be in the desired state and automate the process of managing configurations, ensuring that every system is configured correctly and consistently.[14]
- Security and compliance: A solution for compliance auditing, compliance solutions, GDPR (General Data Protection Regulation), and Government legislation..
- Application Delivery: Cloud Migration, Cloud Native, Modernizing Legacy Applications, Application Migration Program (Windows Server 2008 R2) and Implementation DevSecOps are available.
On Devices and Resources:
The main product is Chef Infra that interacts with Chef Workstation and Chef Server. Chef Infra supports several areas of automation like Cloud, overall Operating Systems nodes, Virtualization, Containers, Provisioning, Continuous Integration, and Configuration Management Tools.
Technologies you can use:
Chef supported, free distribution is currently in version 12, while Chef Infra Server and Chef Client are in version 14. It has more than 3,914 Cookbooks at its public Chef Supermarket covering several areas of IT infrastructure:
- Cloud: Amazon Web Services, Google Cloud Platform, Microsoft Azure and others.
- Operating Systems: AIX, Amazon Linux, CentOS, Debian FreeBSD, macOS, Oracle Enterprise Linux, Red Hat Enterprise Linux, Solaris, SUSE Linux Enterprise Server, Ubuntu (LTS releases), Microsoft Windows and others.
- Virt & Containers: VMware, Vmware on AWS, Kubernetes, Docker and others.
- Provisioning tools: Terraform, CloudFormation and others.
- Continuous Integration: TravisCI, Jenkins, Drone and others.
- Configuration Management: Ansible, SaltStack, Puppet and others.
How Does Chef Work?
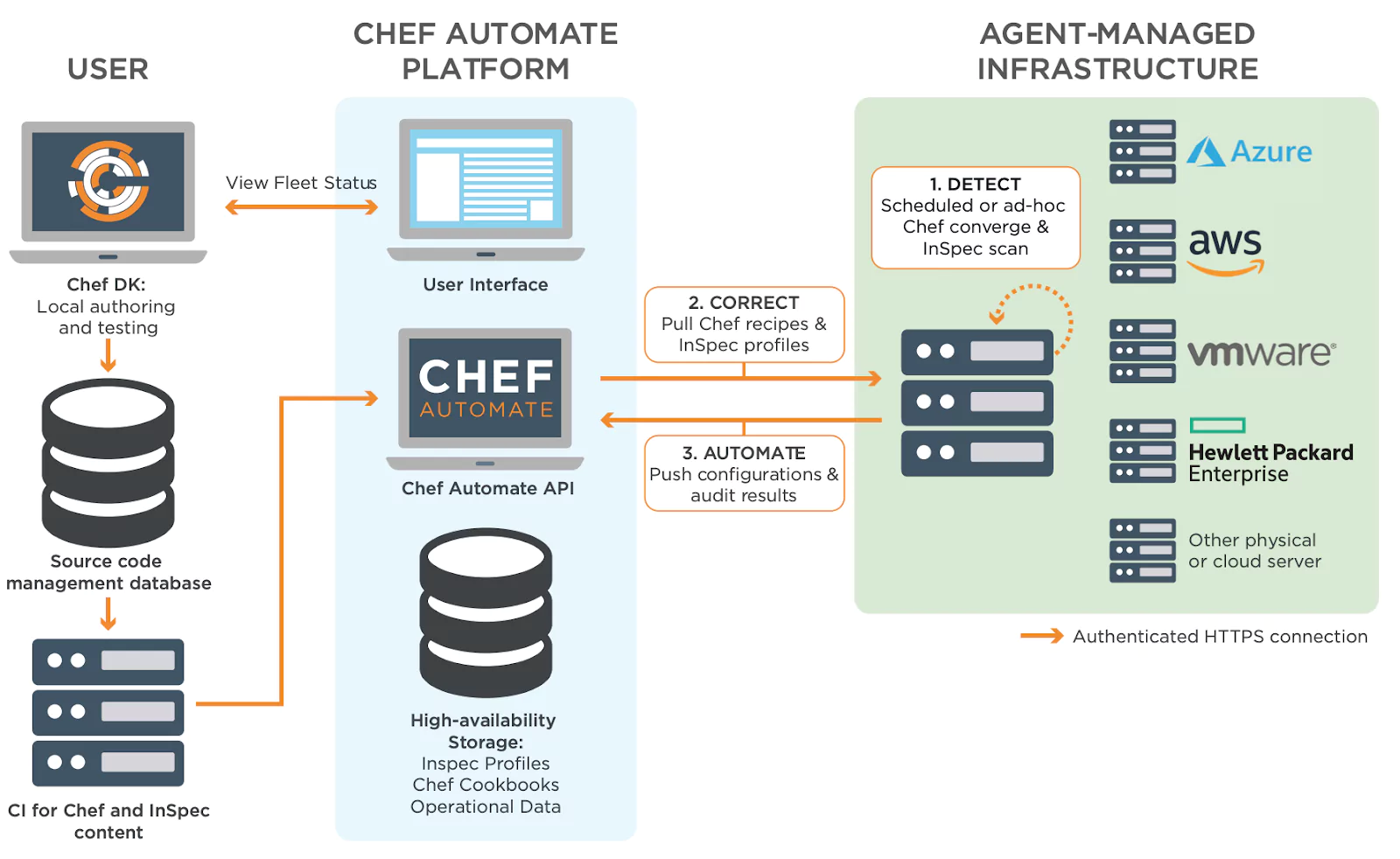
Source: Chef Get Data Sheet
- Resources: It provides a collection of Ruby Programming classes for automating infrastructure used in Chef Recipes like package, directory, mount, file, etc.
- Recipes DSL: It’s the same as Ruby DSL. Anything that can be done using Ruby can also be done in a Chef Recipe or custom resource. Users can leverage the full power of the Ruby programming language to model appropriate solutions.[15]
- Cookbook: Define a scenario with a collection of the Chef Recipes and other components that are required like attribute values, file distribution, templates, Extensions of Chef.
- Chef Infra: It’s part of Chef Automate and has the subcomponents Chef Workstation, Chef server and Clients for Infrastructure Automation.
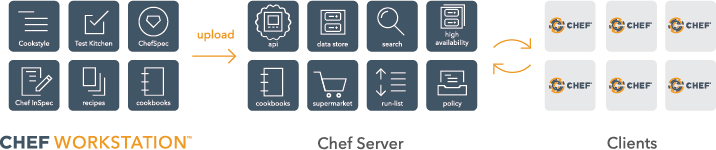
Source: An Overview of Chef Infra
- Chef Workstation: A toolset for users to interact with Chef Infra. With Chef Workstation, users can create and test cookbooks using tools such as Test Kitchen and interact with the Chef Infra Server using the knife and chef command-line tools.
- Chef Infra Client: Nodes that are managed by Chef Infra, like virtual machines, servers, cloud, networking devices and others.
- Chef Infra Server: Works as a hub for configuration data. Chef Infra Server stores cookbooks, the policies that are applied to nodes, and metadata that describes each registered node that is being managed by Chef. Nodes use the Chef Infra Client to ask the Chef Infra Server for configuration details, such as recipes, templates, and file distributions.[16]
Other Resources

Chef Automate: It provides a full suite of enterprise capabilities with support plans for node visibility and compliance. Chef Automate integrates with the open-source products Chef Infra Client, Chef InSpec and Chef Habitat.
Habitat by Chef: Habitat is open-source software that creates platform-independent build artifacts and provides built-in deployment and management capabilities for Application Automation.
Chef InsPec: It’s an open-source framework with a human-and-machine-readable language for testing, specifying compliance, security and auditing your applications and infrastructure for Compliance Automation.
KitchenCI: It provides a test harness to execute infrastructure code on one or more platforms in isolation. A driver plugin architecture is used to run code on various cloud providers and virtualization technologies such as Vagrant, Amazon EC2 and Docker.
Chef Supermarket: It’s the site for community cookbooks and tools as Knife and Ohai plugins. It provides an easily searchable cookbook repository with a web UI.
Community and Support
Chef has community support for each portfolio of products behind the Chef Supermarket, with events, meetings, forum discussion, Slack channels, podcasts and posts blogs. There is a big annual event called ChefConf where consumers, developers, enthusiasts, and fans meet at an event like Apple WWDC.
Pricing starts at $16,500 per year, for Standard support on smaller deployments, including Effortless Infrastructure Suite in Essential Plan with Chef Infra, Inspec Automate for 100 nodes/targets. This does not include Chef Habitat. The Essentials Plan, starting at $35,000 per year, for Enterprise Automation Stack, includes Chef Habitat for 100 service instances.[17]
Maturity and Learning Curve
Chef has a medium Learning Curve and provides learning resources. The Learn Chef Rally is an open platform of learning for the community that makes Tutorials, Quickstarts, Tracks, Hands-on with Modules and Demos available for “your DevOps learning journey with Chef, Chef Automate, InSpec, and Habitat”[18].
The quality of Chef materials and resources available is a highlight and improves the user experience. The website, documentation, whitepapers, datasheets, presentations and eBooks contain beautiful diagrams, infographics and graphic representations using a clean design.
Can it be used with other configuration management tools?
Like any configuration management tool, Chef is not incompatible with other tools. There are points of intersection, but they can be combined to extract the best features of each one. Terraform is the recommended tool to cover the gap of Chef concerning Cloud Providers.
Ideal Use Case
Chef’s main strength is Continuous Automation: Infrastructure, Application and enforcing compliance on complex topologies or deployments that need speed, efficiency, and risk management with cross-functional teams. It is “for organizations seeking the highest degree of confidence before introducing change to production systems.”[19]
SaltStack

- Website
- Documentation
- Community
Brief Summary
Salt is one of the open-source configuration management tools written in Python. The project was created in 2011 by the SaltStack company and “was largely the work of its co-founder, Tom Hatch. His street cred in CM development stems largely from his long-time use of both Puppet and Chef. He felt dissatisfied with both, particularly their slowness and over-reliance on Ruby.”[20]
What can I do using Saltstack?
As described in its getting started documentation “Salt is designed for high-performance and scalability. Salt’s communication system establishes a persistent data pipe between the Salt master and minions (agent nodes) using ZeroMQ or raw TCP, giving Salt considerable performance advantages over competing solutions”[21].
The main resources and features are:
- Security and Compliance: SecOps solutions like active vulnerability remediation and continuous compliance at scale.
- Infrastructure Automation: ITOps solutions for deployment and provisioning of several systems, infrastructure that self-heals, and control the cloud(s) and most complex IT environments.
- Network Automation: NetOps control software-defined network for global network management, programmatic network configuration, active security compliance enforcement and fast, accurate network audits at scale.
On Devices and Resources:
By default, Salt requires agents installed on the nodes (minions) and at least one Salt master server. The flexibility of Python allows Salt to run nearly everywhere that Python runs. There is a proxy minion system for devices that can’t be managed with Python. It supports various technologies for major cloud providers, almost all operating systems (including the Microsoft Windows ecosystem), the main virtualization and containers platforms, database infrastructure, monitoring and networking.
Technologies you can use:
Salt, currently in version 3000, has around 1200 modules or plugins in several areas of IT infrastructure, security compliance and networking automation:
- Cloud: AWS EC2, Azure, Digital Ocean, CloudStack, OpenStack, IBM Cloud and others.
- Operating Systems: Windows, macOS X, FreeBSD, Solaris, AIX, Raspbian, Amazon Linux, Oracle Linux, Red Hat Linux / CentOS, SLES, Debian, OpenSUSE, SmartOS and others.
- Virt & Containers: ProxMox, Vmware, Xen, Kubernetes and others.
- Databases: MySQL, Postgresql, Redis Server, MS SQLServer and others.
- Monitoring: Zabbix, Nagios, Coralogix and others.
- Networking: Juniper Junos, Palo Alto, or F5 Networks, Cisco, Brocade, HP Switches, Dell PowerConnect Switches, Extreme Networks and others.
- Windows: DSC, Group and Local User, Local GPO, IIS, PSGet, Windows Update, Firewall and others.
How Does Saltstack Work?
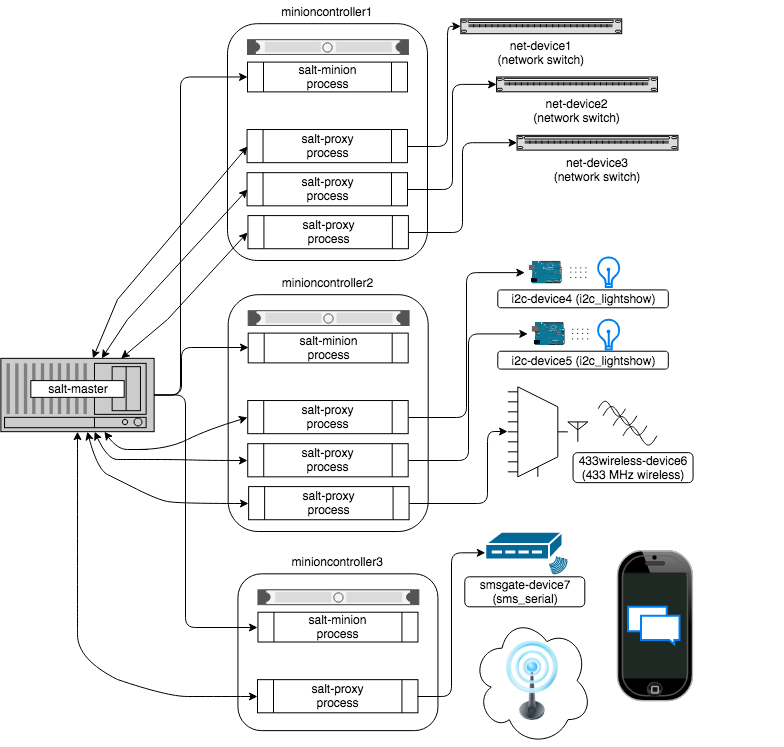
Source: Salt Proxy Minion
“Salt uses a server-agent communication model, (though it works well as a standalone single-server management utility, and also provides the ability to run agentless over SSH). The server component is called the Salt master, and the agent is called the Salt minion.”[22]
- Salt Master: It is responsible for sending commands to agent or proxy minions, and then aggregating and displaying the results of those commands.
- Salt Minions: Nodes or client agents.
- Plug-ins or modules: In Salt, plug-ins are known by their Python module name. Since each plug-in is a Python module, most of the time they are simply called modules, or more accurately, Salt subsystem modules (Salt auth modules, Salt fileserver modules, and so on).[23]
- Salt Grains: A key-value pair that contains facts about a system, such as its hostname and network addresses.
- Salt Pillar: It’s a system that lets you define data to store values such as ports, file paths, configuration parameters and passwords.
- Formula Salt State Files (SLS): Content files in YAML format that describe the state to be configured and enforced on the targeted machines, similar to Ansible Playbooks.
- Proxy Minions: Proxy minions are a developing Salt feature that enables controlling devices that, for whatever reason, cannot run a standard Salt minion.
- Salt SSH: An agentless tool to execute Salt ad-hoc commands in a node without Salt minion installed. It only needs the SSH protocol and Python installed.
Other Resources

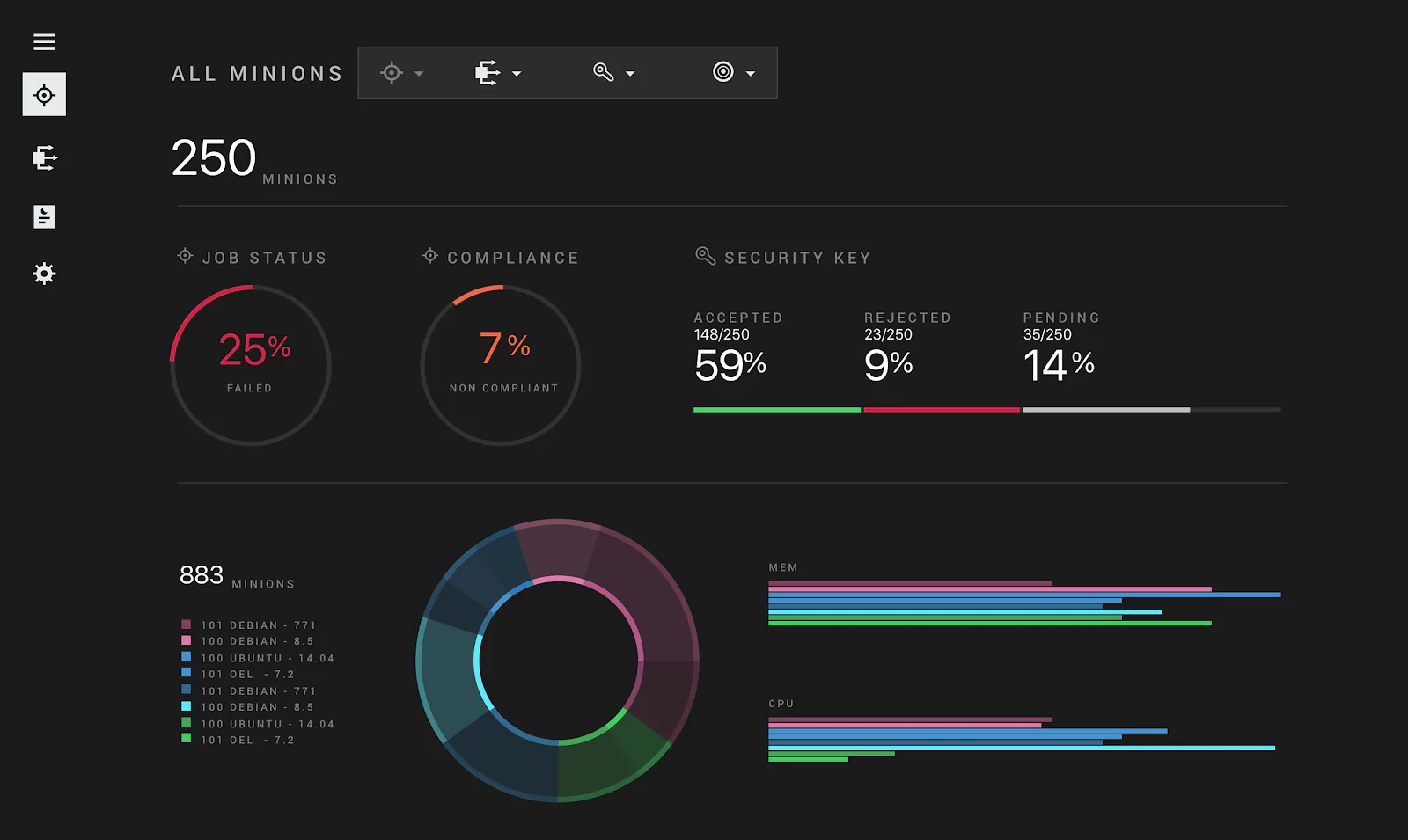
SaltStack Enterprise: This is the main product suite with a support plan. It provides powerful automation and orchestration for the entire IT operations team.

Salt SecOps: Automated continuous compliance for production infrastructure and collaborative security operations teams.
Community and Support
Salt has many resources for its community of users, contributors and developers. These include; meetups around the world, Virtual User Groups with weekly online events, IRC channels and a Slack workspace.
The big event for enthusiastic users, consumers, partners and developers is SaltConf. The SaltConf20 EU was scheduled to be held in the Netherlands, June 9-10, 2020.
The SaltStack Enterprise is the version with a support plan and can cost up to $150 per minion/year.
Maturity and Learning Curve
The Learning Curve is low for the basics of getting SaltStack up and running. Tutorials and Getting Started, online documentation, as well as The Hacks podcast are easily accessible.
Reference materials like the site, documentation, resources, and use cases fall short of expectations and can frustrate new fans. The tutorials, on the other hand, are well done. The organization of the online documentation is not intuitive and has terrible design compared with the other tools assessed in this article. This is the main drawback of SaltStack.
Can it be used with other configuration management tools?
Salt integrates with any management configuration tool. There are rosters for Ansible and Terraform (for Salt SSH), modules for Chef and Puppet, and the Ansbilegate. With the last one, it’s possible to use the playbooks and modules resources of the Ansible core.
Ideal Use Case
It is best for enterprise IT organizations that wish to orchestrate and to automate IT tasks with speed and flexibility to deliver continuous security compliance, vulnerability remediation and IT security.
Summary
How can you benefit from the DevOps Culture and be agile, with the daily increase in tools and solutions that are emerging and disappearing at every moment? How can you choose the best CM tool for your particulars?
The main challenges:
- The variety of configuration management tools (CM) .
- The best tool depends on your environment and the maturity of the team.
- For businesses that do not use any automation tool, studying the great number of tools is an additional challenge.
- The transition path for the Sysadmin to the DevOps Culture with automation.
- The constant changes and releases of the management configuration (CM) tools.
- Changing the paradigm of infrastructure to automation.
Recommendations:
DevOps and Sysadmins should make their own toolsets for infrastructure automation:
- Time is money and automation saves time.
- Understand the basic concepts behind infrastructure configuration management tools.
- The features of each of the main tools for configuration management.
- Study the scope of the work to be automated and the “ideal use case” of the main configuration management tools.
- Design your toolset for each situation in your environment.
- Defining the scope of what you want to accomplish helps to decide what tool to use.
- Evaluate creating a multidisciplinary automation team.
Footnotes
[1] “ansible/ansible: Ansible is a radically simple IT … – GitHub.” – Github
[2] “Ansible module development: getting started — Ansible ….” – Ansible
[3] “Working With Plugins — Ansible Documentation.” – Ansible
[4] “Terraform Announcement” – Terraform
[5] “Introduction to Infrastructure as Code with Terraform”, – Terraform
[6] “Intro – Terraform.” – Terraform
[7] “New HashiCorp Terraform pricing aims for midsize firms, teams”, – TechTarget
[8] “Provisioners”, – Terraform
[9] “Agent glossary”, – Puppet
[10] “The Overview platform”, – Chef
[12] “ALDO Agile Lean DevOps Outcomes”, – Chef
[16] “Chef Infra Overview”, – Chef
[18] “Learn Chef Rally”, – Chef
[19] “Chef and Puppet”, – Chef
[20] “Salt vs Puppet: Which One to Choose?”, – Upguard
[21] “Understanding SaltStack”, – SaltStack
[22] “Communication Model”, – SaltStack
[23] “Salt Plugins”, – SaltStack




