Observability guides
Deep-dive guides from observability experts
All Articles
- All
- Observability
- General
- AIOps
- CSPM
- SOC
- CDN
- WAF
- Prometheus
- Kubernetes
- OpenSearch
- OpenTelemetry
- ELK
- SIEM
- MDR
- RUM
- APM

10 Threat Hunting Tools to Know in 2024
Key Features of Cyber Threat Hunting Tools Threat hunting tools typically include the following cybersecurity capabilities. Automated Threat Detection Threat hunting tools use algorithms and machine learning models...

Arctic Wolf MDR: Key Features, Architecture, Pros and Cons
Key Features of Arctic Wolf MDR Here are some of the main capabilities of this...

SIEM Architecture: 10 Key Components and Best Practices
The Key Components of SIEM Architecture SIEM systems include the following components. 1. Data Sources...

10 Observability Tools to Know in 2024
Observability Tools vs Observability Platforms Observability tools are often specialized, focusing on narrow aspects like metrics, logs, or traces. They provide deep insights into particular segments of the...

Observability vs Monitoring: 5 Key Differences
What Are the Similarities Between Observability and Monitoring? Observability and monitoring share the goal of ensuring that systems operate reliably and efficiently. Both practices involve collecting data that...

Observability: Principles, Challenges, Capabilities & Practices
Benefits of Observability Implementing observability across an organization’s IT infrastructure provides several benefits: Monitoring vs...

Cloud SIEM vs Traditional SIEM: What Is the Difference?
Cloud-Native SIEM Features and Capabilities Cloud SIEM platforms typically offer the following features: Traditional SIEM...
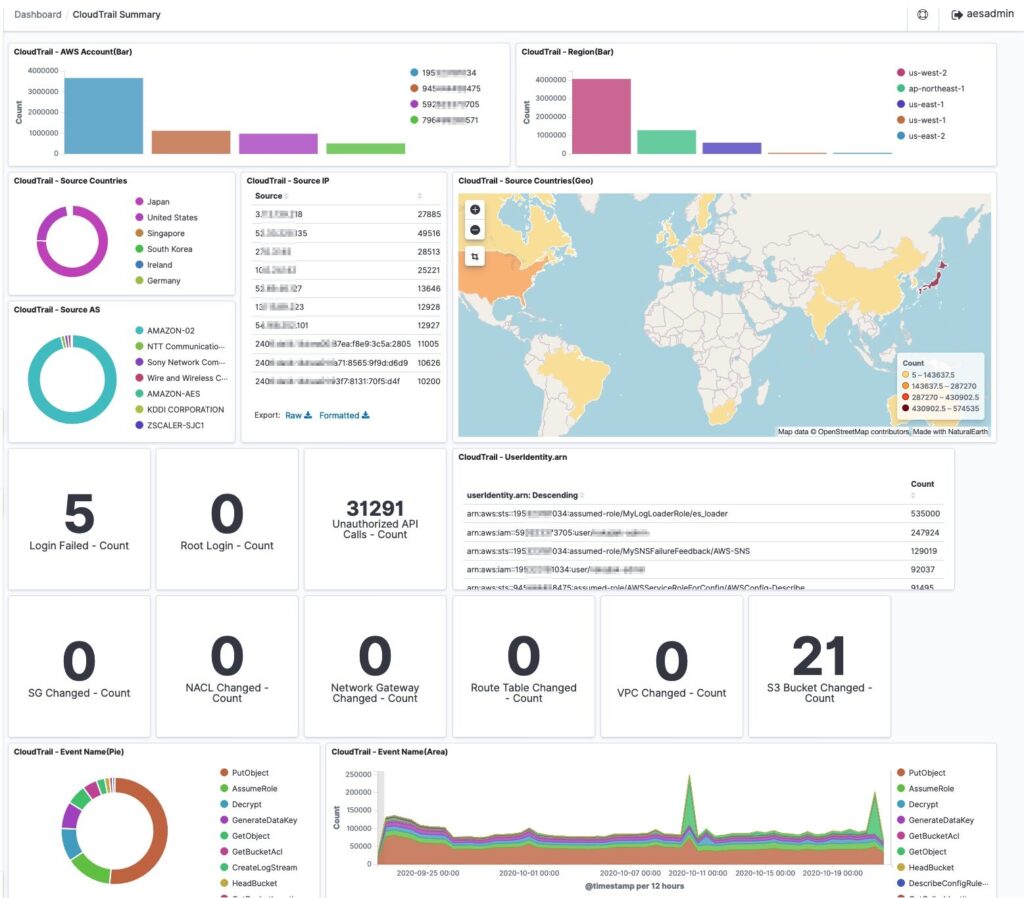
SIEM in AWS: Native and Third Party Solutions
Benefits of Implementing SIEM in AWS Implementing SIEM in AWS provides several key advantages, including: Example of Native AWS SIEM Solution: SIEM on Amazon OpenSearch Service SIEM on...

OpenSearch with Python: The Basics and a Quick Tutorial
OpenSearch Python Clients There are several clients that can be used to interface with OpenSearch...

Coralogix SIEM vs. Datadog SIEM
Not all SIEMs are built the same If you’re evaluating options for a modern SIEM platform, chances are you’ve come across the Datadog SIEM and the Coralogix SIEM....

SIEM Logging: Components, Log Sources & Best Practices
Why Is SIEM Logging Important for IT Security? SIEM logging enables real-time threat detection and...
What Are AWS Edge Locations & Using Lambda@Edge with CloudFront
How Do Edge Locations Work? Edge locations respond to user requests with the nearest cached...

