The Coralogix blog
Expert insights, bold ideas, and company news
All Articles
- All
- Alerts
- OpenTelemetry
- Olly
- Uncategorized
- Software development
- AI
- AWS
- Product
- CDN monitoring
- CloudWatch
- Logging
- Real user monitoring
- Data
- Gaming
- APM
- Cloud
- Fintech
- FinOps
- Kubernetes
- Microservices
- Compliance
- Observability
- Metrics
- Security advisory
- Tracing
- CI/CD
- IaC
- Elasticsearch
- Migrations
- DevOps & IT operations
- Troubleshooting
- Service Management
- Company news
- Case studies
- MDR
- Security
- Performance
- Extensions
- Tutorials
- Audit logs
- Infrastructure monitoring
- Logs
- Application performance monitoring
- SRE
- Monitoring
- Log analytics
- DataPrime

Hybrid Cloud Defense Grid: Bridging Wiz and Runtime Telemetry
The modern cloud security landscape is often fighting a war on two disconnected fronts. On...

Threat hunting with Olly
Effective threat hunting requires both comprehensive visibility and quick, data-driven insights. Olly, the AI-powered observability teammate within Coralogix, provides just that. Whether you’re tracking lateral movement, uncovering stealthy...

Building visibility and resilience across Kubernetes
Why Kubernetes Security and Monitoring Matter Kubernetes has transformed how modern applications are deployed and scaled. Its flexibility and automation power innovation but also expand the attack surface....

Mastering OWASP Detection: Enterprise Rules for AWS, Akamai, F5, and Cloudflare
Application Security, WAF, and OWASP form an interconnected defense strategy for web applications. OWASP (Open...

Turn AI ambition into secure operations
If you attended AWS re:Invent last year, it probably felt like there was an AI solution for everything. Models, copilots, agents; by the end, someone had to pitch...

Smarter SIEM starts here: Context, speed, and the power of MCP
Traditional SIEMs were built for a simpler time, when infrastructure was static, data was structured,...

Coralogix Expands Unified Threat Intelligence Coverage
Coralogix is excited to announce a major enhancement to our Unified Threat Intelligence (UTI) capabilities...

Raising the Bar in Observability and Security: Coralogix Extensions at Scale
In today’s high-velocity digital ecosystem, visibility isn’t enough. SREs and engineering leaders need real-time insights,...

GitHub Action Supply Chain Attack (CVE-2025-30066)
Summary On March 14, 2025, a critical supply chain attack targeted the widely used GitHub Action tj-actions/changed-files. This action, utilized in over 23,000 repositories, was compromised when attackers...

The Digital Operational Resilience Act (DORA) is coming – are you ready?
As the official implementation date approaches for the Digital Operational Resilience Act (DORA) – financial...
Track SBOM Compliance with Coralogix
A Software Bill of Materials (SBOM) is essentially an inventory of the components used to build a software artifact, such as an application. While the concept of tracking...
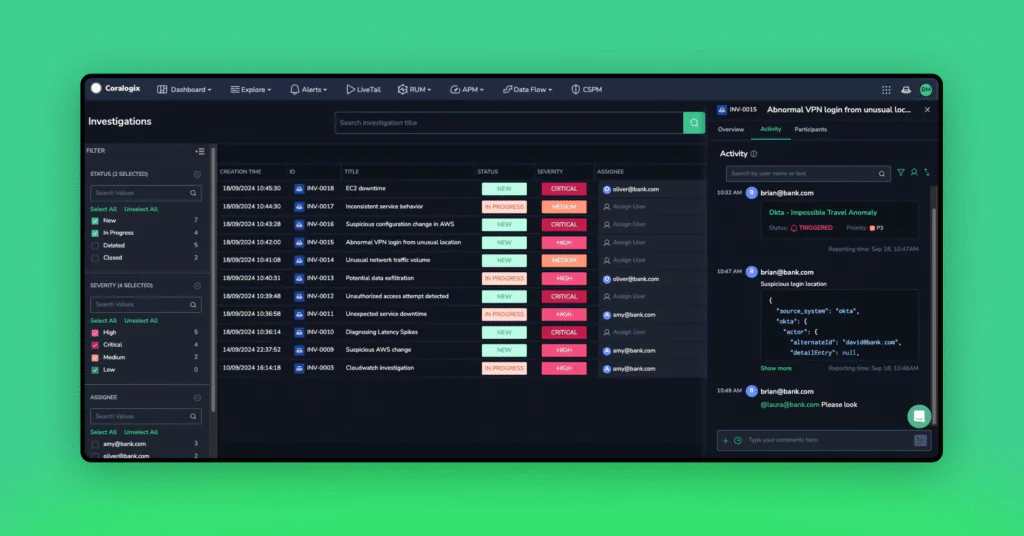
See the Bigger Picture: How Coralogix Investigations Speeds Up Root Cause Analysis
In the fast-paced world of business, timely and accurate incident investigations are crucial. The ability...

