Okta Log Insights with Coralogix
This post will show you how Coralogix can provide analytics and insights for your Okta logs, both performance, and security. Okta is one of the leading…
Whether you are just starting your observability journey or already are an expert, our courses will help advance your knowledge and practical skills.
Expert insight, best practices and information on everything related to Observability issues, trends and solutions.
Explore our guides on a broad range of observability related topics.


Today, Okta, a leading enterprise identity and access management firm, reported that it had launched an inquiry after the LAPSUS$ hacking group posted screenshots on Telegram. The hackers claimed the pictures were taken after obtaining access to “Okta.com Superuser/Admin and various other systems.”
If your organization uses Okta as its SSO, and you are currently forwarding Okta audit logs to your Coralogix account it is likely that your logs already contain information that can help you investigate if you were attacked. This article will describe the steps you need to create alerts that will notify you if such an event happens.
If you haven’t yet, the first thing you need to do is get the Okta audit logs shipped to Coralogix. The steps are detailed here: Okta Audit Logs.
Now that the data is coming in, you can enable the Okta audit extension pack by following these steps:
Several alerts and (Kibana) dashboards will be added to your account and will detect anomalies related to this attack. These dashboards will help investigate Okta authentication-related security issues. These alerts (such as ‘Unauthorized admin request,’ ‘A new non-browser like tool used to enter an app,’ and ‘Access admin app event from unknown actor’) can detect this specific breach.
To improve the detection even further, you can also enable the security enrichment in Coralogix on the logs from Okta. To do that, follow these simple steps:
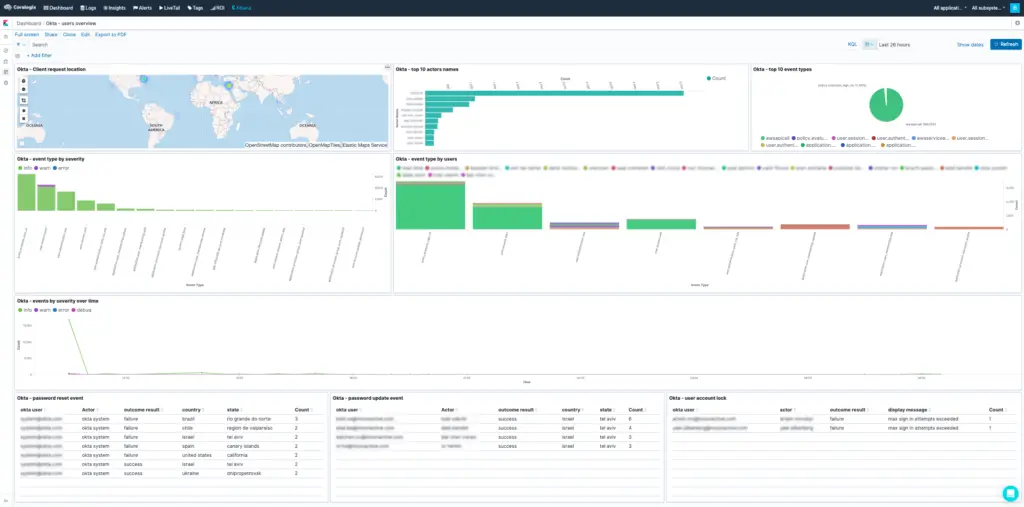
The steps mentioned above will help you detect and alert about unusual Okta activities, which will indicate malicious activity such as the one done by the LAPSUS$ hacking group. In addition, you can build the following table visualization in Kibana and use it to examine the Okta logs from the past 24 hours to see if there was any alarming activity:
You can now check the number of source countries per user across the selected time range at the top right. If you find a user that has connected from multiple locations, especially if this user is a privileged user, you can use this visualization to investigate the behavior of this user in the past to see if this is a new behavior.
If you have any further questions and need assistance, you can reach out to our 24×7 support team via the in-app chat.
This post will show you how Coralogix can provide analytics and insights for your Okta logs, both performance, and security. Okta is one of the leading…
The wide-spread adoption of cloud infrastructure has proven to be highly beneficial, but has also introduced new challenges and added costs – especially when it comes…

With the exponential rise in cybercrimes in the last decade, cybersecurity for businesses is no longer an option — it’s a necessity. Fuelled by the forced…






