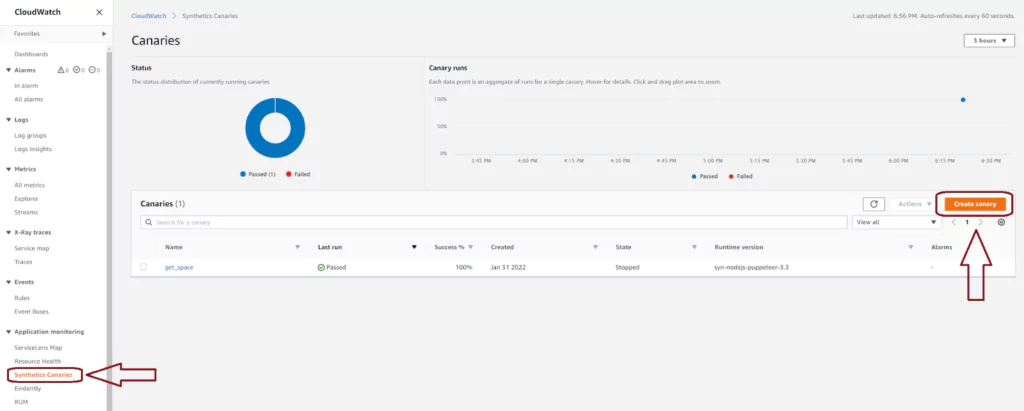
Observability strategies are needed to ensure stable and performant applications, especially when complex distributed environments back them. Large volumes of observability data are collected to support automatic insights into these areas of applications. Logs, metrics, and traces are the three pillars of observability that feed these insights. Security data is often isolated instead of combined with data collected by existing observability tools. This isolation leaves security teams to use separate tools and data collection independent of existing observability strategies.
Combining security and observability data can benefit organizations by enhancing overall system resilience, identifying potential threats, and improving incident responses.
By utilizing the internal visibility offered by observability and integrating it with security data, businesses can expand their monitoring capabilities across every aspect of their IT environment, establishing security observability. This single pane of glass, in turn, makes it easier to identify, analyze, and respond to suspicious activity and anomalies that can come from various attack vectors.
Application performance monitoring and security
Application performance monitoring (APM) uses software tools to detect and isolate application performance issues. Couple APM with observability techniques to assess application health by tracking relevant key performance indicators (KPIs) such as load, response time, and error rate. The results of these KPIs logically overlap with security metrics, so they can be used to detect security events. Security data, like logs from SIEM systems, can be integrated with the APM logs to detect security issues more efficiently. The SIEM data could include information like login attempts and authentication failures.
Consider a web application that provides financial services that uses APM tools to track user experience. The APM data would detect events like a user experiencing slow response times when accessing the application. Given it is below some threshold, DevOps teams would be alerted to this issue. When combined with security data, a matching alert might show a spike in authentication failures. When these two data are correlated, the ops team can quickly discern that the slowdown and the authentication errors are associated with a potential brute-force attack against user accounts.
Real user monitoring and security
Real user monitoring (RUM) collects data about user interaction with applications. RUM data detects poor user experience, telling DevOps teams there is some issue in the stack. Tools collect details about user interaction, such as page load times and click-through rates. When combined with observability data, RUM helps teams identify issues’ root causes so teams can quickly fix and reduce effects on user experience. Combining this data further with security data like logs from web application firewalls or intrusion detection systems would help teams identify when the problem is not with the stack directly but due to a security breach.
RUM metrics will detect when users experience a sudden increase in page load times while security logs simultaneously show a surge in requests with potentially nefarious payloads. Combining security and observability data would correlate these events, revealing that the detected performance degradation is likely linked to a distributed denial of service (DDoS) attack. An early response due to a linked alarm allows response teams to quickly implement security measures to mitigate the ongoing threat.
Infrastructure monitoring and security
Infrastructure monitoring collects performance data from your technology infrastructure, including servers, networks, containers, virtual machines, and databases. This monitoring aims to identify bottlenecks or anomalies in near real-time so maintenance can occur quickly, improving reliability and providing optimal performance. When combined with security metrics, infrastructure monitoring can further enhance the security of underlying IT infrastructures.
Infrastructure monitoring commonly collects CPU usage, memory consumption, and other performance-related metrics. Security metrics like SIEM logs contain information on detected security incidents like firewall events. If an unusual spike in network traffic is detected through infrastructure monitoring and security events show high numbers of suspicious login attempts across multiple servers, these events could be correlated, indicating a potential distributed brute-force attack. Early detection allows for quick incident response and implements security measures to thwart the attack and resume real-user performance by optimizing resources.
Anomaly detection and security
Anomaly detection in observability analyzes patterns in observability data to help predict issues. The purpose is to quickly identify and notify teams of unexpected data patterns like CPU or memory usage surges, a spike in erroneous transactions, or a sudden drop in web traffic. Algorithms are available within observability tools that track such changes, including thresholding, outlier detection, and machine learning algorithms that learn your system’s typical behavior. Giving these algorithms access to security data gives them more context to detect anomalies and identify security threats as a potential cause.
Cybersecurity teams are responsible for monitoring network traffic. Anomaly detection can detect unusual patterns in network traffic to identify potential security incidents. Machine learning algorithms recognize standard patterns and flag deviations that indicate anomalous activity. If this anomaly detection system is integrated with security data such as firewall logs and intrusion detection system logs, the ability to identify anomalies indicative of security threats increases. Unusual spikes in network traffic and security events like failed authentication attempts raise suspicion of a potential brute-force attack or a compromised user account. Early detection from these insights means the security team can mitigate the incident by blocking suspicious IP addresses or strengthening authentication controls.
Identity Management and security
Identify management systems maintain a repository of user identities. These repositories include user profiles, roles, and permissions and are the authoritative source for managing user identities. Access controls must be defined within the system based on principles of least privilege, where users only have access to what they need and use and nothing more. Policies must be configured to restrict access to sensitive resources based on assigned roles. Anomaly detection can be used in identity management systems to monitor authentication events, looking for unusual patterns such as multiple failed login attempts. Observability tools can also detect if users do not use their accessible data so that permissions can be revoked for unnecessary data.
Combining identity management observability with security data such as SIEM logs and authentication server logs allows for the correlation of events. A sample case could be if the anomaly detection systems flag a spike in failed login attempts while simultaneously having security logs showing unauthorized attempts to a sensitive database associated with that user account. Correlating these events signals a security incident and a compromised user account. Correlating these events allows for early detection and incident response to prevent malicious users from accessing sensitive data.
Summary
Full stack observability is critical to provide fast incident responses and prevent future incidents from occurring. When security threats cause incidents, there is an added urgency where fast incident thwarting will reduce damage. Combining security and observability data to give a single pane of glass allows teams to detect malicious actions faster than looking at this data separately. This is the case for many different monitoring techniques like APM, RUM, and infrastructure monitoring.
Coralogix is an observability SaaS tool offering full-stack observability and security observability with SIEM, CSPM alongside managed detection and response services. Teams can easily combine observability and security data easily using Coralogix’s single observability offering.