Palo Alto Global Protect Command Injection Vulnerability

On April 12, 2024, Palo Alto disclosed a critical vulnerability identified as CVE-2024-3400 in its PAN OS operating system, which carries the highest severity rating of 10.0 on the CVSS scale. This vulnerability, present in certain versions of Palo Alto Networks’ PAN-OS within the GlobalProtect feature, allows unauthenticated attackers to execute any code with root privileges on the firewall through command injection.
The flaw, which has been actively exploited since at least March 26, 2024, affects approximately 22,500 exposed Palo Alto GlobalProtect firewall devices. The exploit involves command injection triggered by the creation of arbitrary files, posing significant security risks to affected systems.
This vulnerability applies only to
1. PAN-OS 10.2, PAN-OS 11.0 and PAN-OS 11.1 firewall configurations with a
GlobalProtect gateway or GlobalProtect portal (or both)
AND
2. Enabled Device Telemetry
Timeline of Events
The issue was found by Volexity, a cyber security company, on 10th April in one of its customer environments and shared with Palo Alto on April 12, 2024.

(Above are the timelines as shared by Volexity for the given findings.)
Products Affected
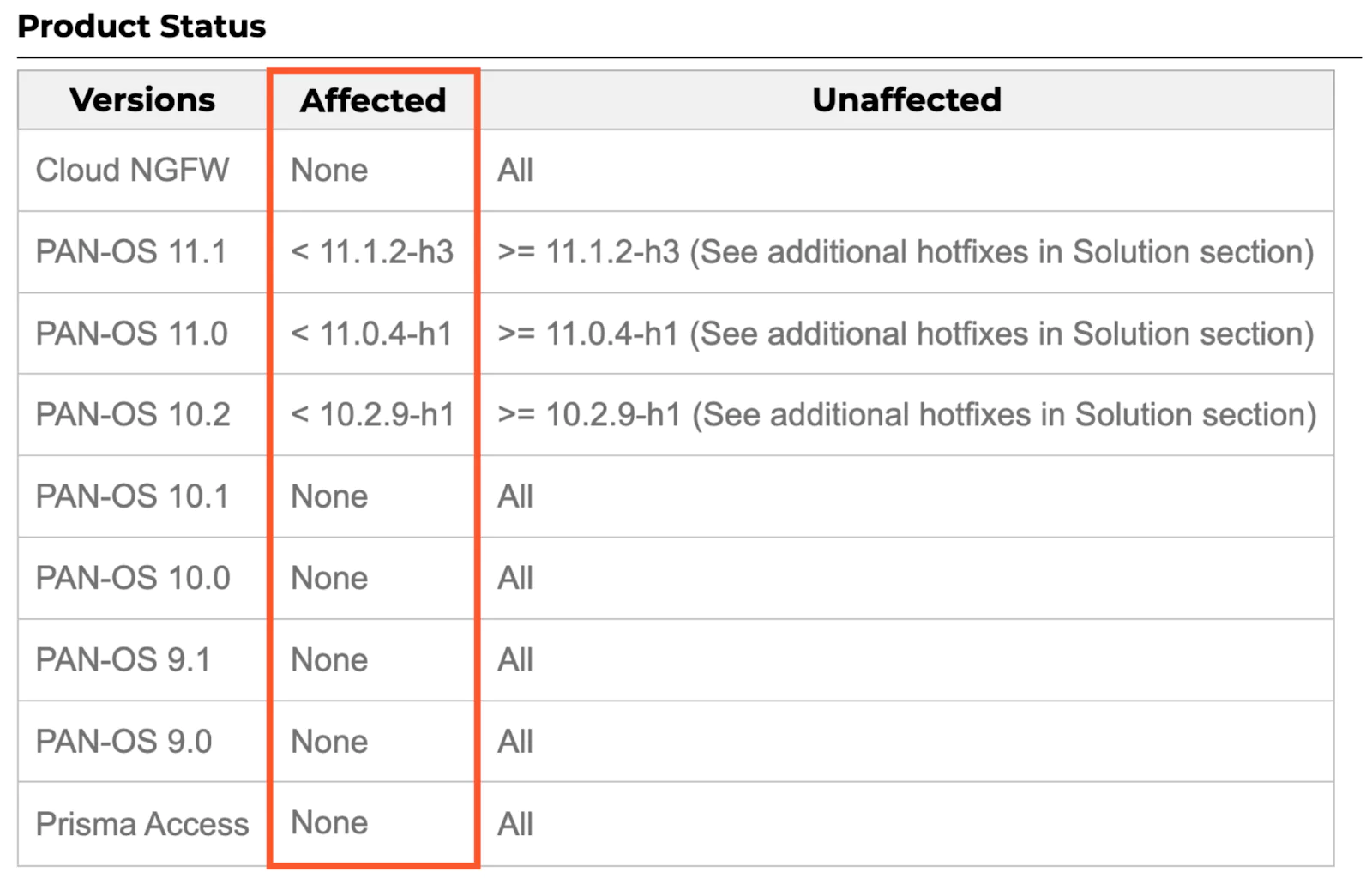
Products Not Affected
The vulnerability does not affect cloud firewalls (Cloud NGFW), Panorama appliances, or Prisma Access.
Mitigation/Solution
This issue is fixed in hotfix releases of PAN-OS 10.2.9-h1, PAN-OS 11.0.4-h1, PAN-OS 11.1.2-h3, and in all later PAN-OS versions. Hotfixes for other commonly deployed maintenance releases will also be made available to address this issue. Please see the details below for ETAs regarding upcoming hotfixes.
PAN-OS 10.2
– 10.2.9-h1 (Released 4/14/24)
– 10.2.8-h3 (ETA: 4/15/24)
– 10.2.7-h8 (ETA: 4/15/24)
– 10.2.6-h3 (ETA: 4/15/24)
– 10.2.5-h6 (ETA: 4/16/24)
– 10.2.3-h13 (ETA: 4/17/24)
– 10.2.1-h2 (ETA: 4/17/24)
– 10.2.2-h5 (ETA: 4/18/24)
– 10.2.0-h3 (ETA: 4/18/24)
– 10.2.4-h16 (ETA: 4/19/24)
PAN-OS 11.0
– 11.0.4-h1 (Released 4/14/24)
– 11.0.3-h10 (ETA: 4/15/24)
– 11.0.2-h4 (ETA: 4/16/24)
– 11.0.1-h4 (ETA: 4/17/24)
– 11.0.0-h3 (ETA: 4/18/24)
PAN-OS 11.1
– 11.1.2-h3 (Released 4/14/24)
– 11.1.1-h1 (ETA: 4/16/24)
– 11.1.0-h3 (ETA: 4/17/24)
Workaround
1. Customer with Threat Prevention Subscription
Customers with this subscription can block attacks for this vulnerability using Threat ID 95187 (available in Applications and Threats content version 8833-8682 and later).
2. Customer without Threat Prevention Subscription
Customers who don’t have the Threat Prevention subscription or are unable to apply the same can mitigate the vulnerability by Temporarily disabling device telemetry until the device is upgraded to a patched PAN-OS version. Once upgraded, device telemetry will have to be re-enabled on the device. If Panorama manages the firewalls, ensure that device telemetry is disabled in relevant templates (Panorama > Templates).
Coralogix Security Team Response
The Coralogix security team onboarded the above-mentioned IOCs into the Coralogix custom threat intel feed for real-time detection. The team then scanned SRC customer environments with Palo Alto integrations for the aforesaid IOCs.
The Coralogix security team has evaluated if any enhancements and/or additions were needed for our existing detections in light of this vulnerability.
If you need further assistance with respect to this vulnerability, our Security Resource Center (SRC) and Research team would be happy to engage. Please contact your Account Manager, TAM, or SRC SPoC regarding this.
Learn more about Coralogix’s quick start extension for Palo Alto with out-of-the-box security dashboards and alerts.




