Coralogix and observability at the edge
Observing Edge & WAF solutions is challenging. There are a host of unique problems to overcome, including security complexities and traffic intent identification. Let’s explore the…
Whether you are just starting your observability journey or already are an expert, our courses will help advance your knowledge and practical skills.
Expert insight, best practices and information on everything related to Observability issues, trends and solutions.
Explore our guides on a broad range of observability related topics.

There is one area of technology that requires the fastest possible response time, where every second has potentially enormous implications – security. Coralogix fits the security use cases elegantly for a simple reason. It’s very, very fast.
Coralogix alarms fire faster than any of our competitors. When benchmarking our closest competition, whose alarms responded in around 2-4 minutes, we left them behind with a median trigger time of 10 seconds across log alerts.
Malicious IP addresses are endemic in network traffic. The first sign of a malicious IP may be the opening salvo of a full-blown cybersecurity incident, and the difference between the two is the speed of remediation. The “Mean Time to Fix.” Our target with the Coralogix platform was to detect malicious IP addresses and invoke downstream automation to block them instantly.
We have tackled this problem using the following tools:
This hangs together in the following way:

Let’s visualize each connection step by step to better understand this solution from the user’s perspective.
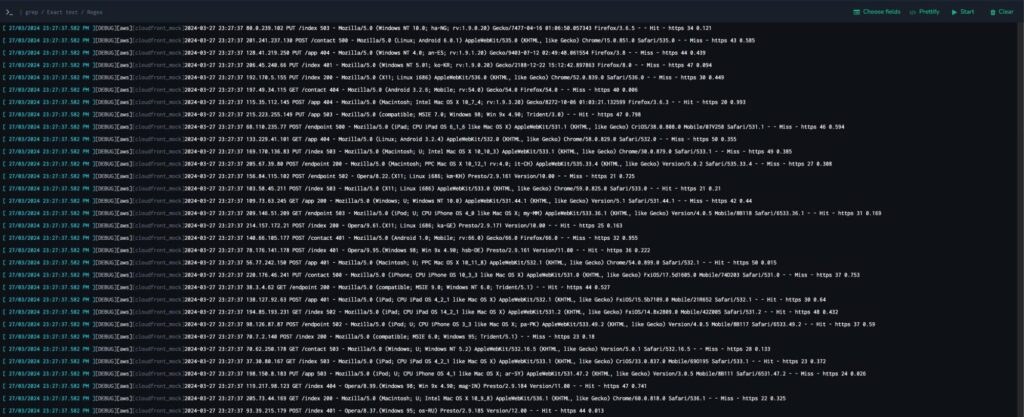
Log data is ingested from Cloudfront via Coralogix singles endpoint. This log data is processed through our unique architecture and indexed, although this indexing step is entirely optional.
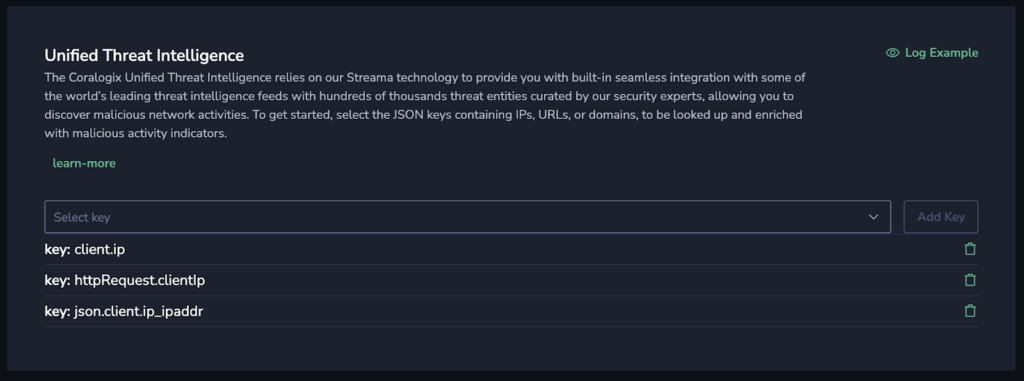
Within this data are client IP addresses. We can automatically analyze these IPs and search over a dozen well-known threat databases to see if they have been flagged by thousands of other providers. If a malicious IP address is detected, it is automatically enriched with important metadata.
This opens up an interesting avenue. On a typical platform, this type of process would have added minutes to the alerting time. Still, Coralogix’s architecture, Streama, handles this processing in parallel, eliminating the traditional performance impact.
Now we know which IP is which, we can define alarms, and this is where Coralogix’s unique architecture and comprehensive alerting shines. We can define an alarm with an “Immediate” condition. This means that the second a log document appears to satisfy the condition, Coralogix invokes the alarm.
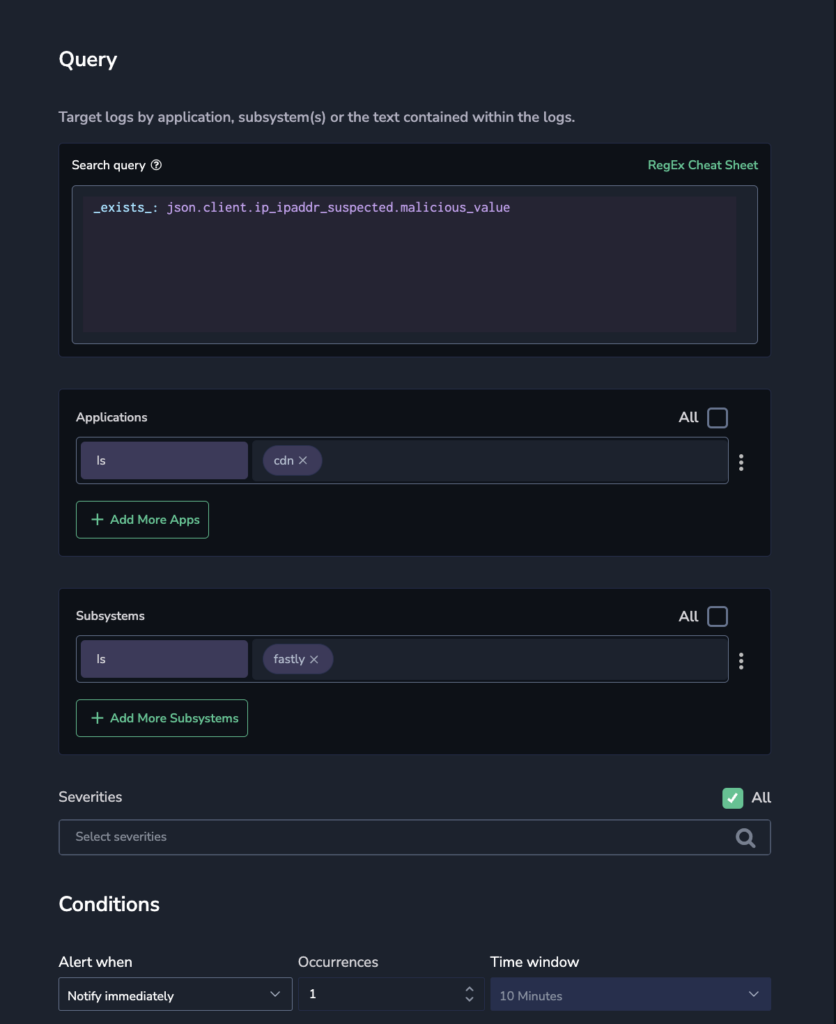
We’ll also configure this alarm to invoke our downstream outbound webhook. Outbound webhooks are extremely extensible tools in the Coralogix platform that allow alarms to invoke any HTTP interface. In this case, we will directly invoke the Lambda Function URL, informing it of the IP address that triggered the alarm.
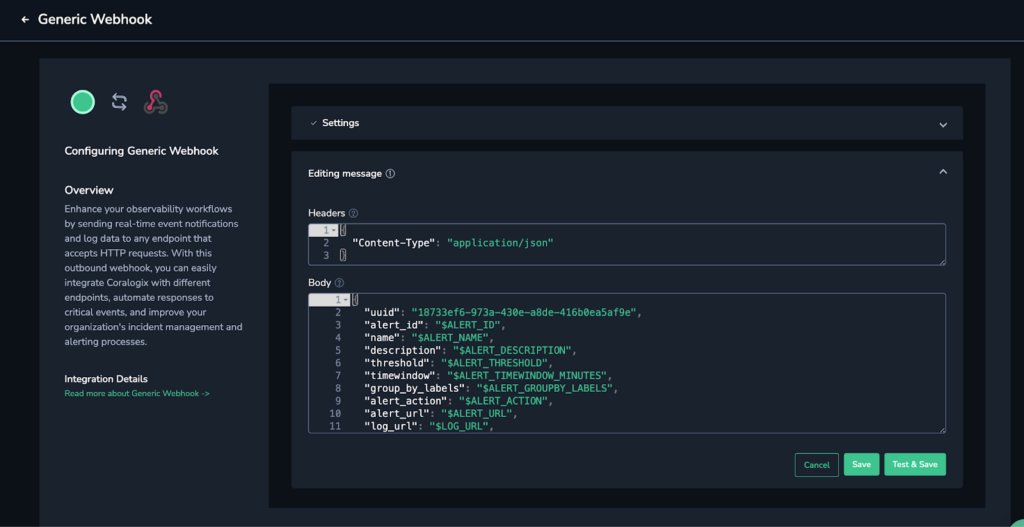
The alarm has invoked a lambda function that has a very simple and specific purpose. The code for this lambda function can be summarized as follows:
const body = event.body
const ip = pullOutIpAddress(body)
await updateWafRulesV2(ip)
const response = {
statusCode: 200,
headers: {
'Content-Type': 'application/json',
},
body:{
response: `${ip} has been added to WAF block rules`
},
};
return response;
The lambda function updates a WAF IP List, using the Node AWS SDK. This IP List is attached to a WAF rule that will automatically block all traffic whose source matches an IP range in the list. Throughout this pipeline, Coralogix has ingested access logs, enriched them to discover the malicious IPs, instantly triggered an alert, and updated downstream automation to remediate the issue.
The most appropriate measurements to take to understand the speed of Coralogix is from when the log was generated and sent to Coralogix, alert trigger time, and when the IP list updates. This gives us an idea of when Coralogix received the data, when the platform reacted to it, and when downstream processes drove the ideal customer outcome.
We dispatched a series of requests, some known to include malicious IP addresses, which were then ingested into Coralogix and enriched. The first such document was written and sent at 21:19:29.109 GMT+1, where it was enriched and indexed.
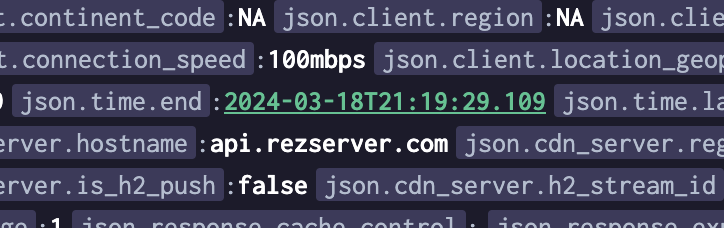
After a little over 1.2 seconds, the alarm triggered. In Coralogix, this does several things, including raising an incident that users can assign to an account or mark as acknowledged.
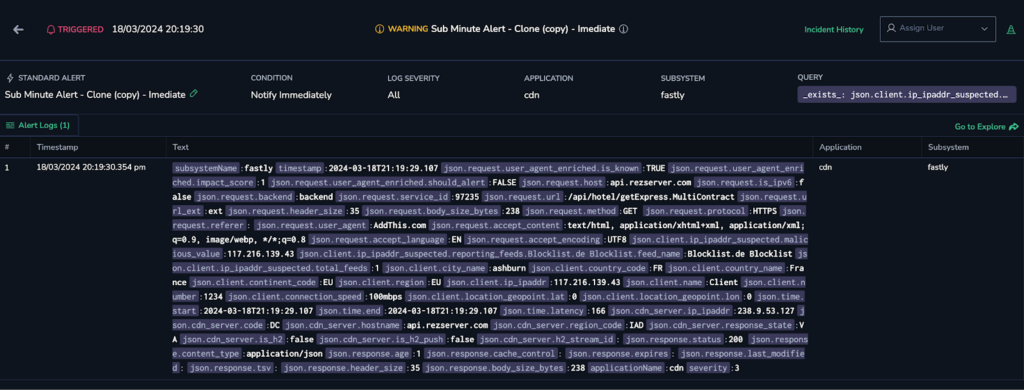
19 seconds later, the lambda function was invoked. (Note: the one-hour timezone difference in timestamps!)
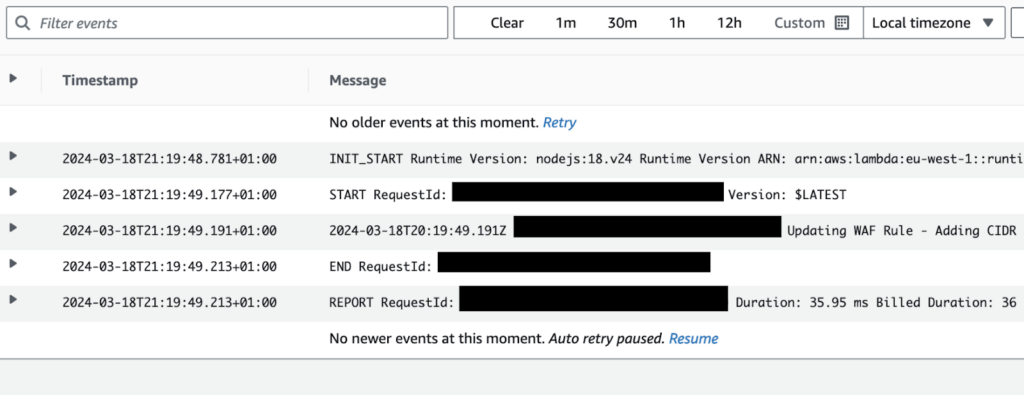
This means an elapsed time from log ingestion to IP rule only took ~20 seconds. This is a pace unmatched by any competing platform, and even AWS WAF offers only one-minute granularity on its rule-based blocking.
Every second a malicious user gets access to your system is a rapidly increasing risk. The sooner they can be removed, the better. The Coralogix platform, built on top of a streaming philosophy, delivers performance that our competitors, even those dedicated to the security space, can only imagine.

Observing Edge & WAF solutions is challenging. There are a host of unique problems to overcome, including security complexities and traffic intent identification. Let’s explore the…

In late November 2023, a phishing campaign successfully compromised hundreds of user accounts, including those belonging to high-ranking executives, across dozens of Microsoft Azure environments. Cybercriminals…
Coralogix is not just another monitoring or observability platform. We’re using our unique Streama technology to analyze data without needing to index it so teams can…






